Report: Malicious PDF files comprised 80 percent of all exploits for 2009
A newly released report shows that based on more than a trillion Web requests processed in 2009, the use of malicious PDF files exploiting flaws in Adobe Reader/Adobe Acrobat not only outpaced the use of Flash exploits, but also, grew to 80% of all exploits the company encountered throughout the year.
Are the flaws in Adobe's product line becoming the cybercriminal's favorite exploitation tactic? Depends, since from another perspective malicious attackers don't have preferences, they exploit whatever is exploitable.
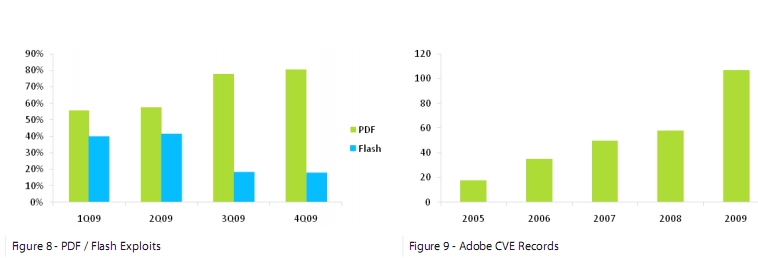
- As seen in figures 8 and 9, malicious PDF files comprised 56% of exploits in 1Q09, growing to 80% of all exploits by 4Q09. Conversely, Flash exploits dropped from 40% in 1Q09 to 18% in 4Q09. This trend is likely indicative of attackers’ preference for PDF exploit, probably due to a combination of increasing availability of vulnerabilities in Adobe Reader and Adobe Acrobat and the continued widespread use and acceptance of PDF files in both the workplace and consumer sectors.
From a cybercriminal's perspective, traffic optimization has evolved from exploit-specific wide-scale attacks, to today's cybercrime business model driven by web malware exploitation kits automatically enumerating potentially exploitable applications and browser plugins, and serving them the appropriate exploits. This malicious optimization of traffic has been an active strategy for several years, with the attackers realizing that the more exploits they introduce within their kits, the higher the probability of infection.
Chart courtesy of Trusteer research published in August, 2009
Therefore, the increasing use of malicious PDFs can also be interpreted as the direct result of the millions of users using outdated and exploitable Adobe products, with the only preference a malicious attacker could have in this case remaining the incentive based on the 99% penetration of Adobe Flash on Internet-enabled PCs. But how is the possible that with such a high market share, ScanSafe's report shows that Adobe Acrobat/Reader exploits grew while the use of Flash exploits declined?
Naturally, there are malicious attackers with clear preferences, based on a number of factors. Some of the widespread client-side exploit serving campaigns launched in the wild over the past few months, act as a good example of how cybercriminals actively monitor the metrics generated from their malicious campaigns, and tailor their exploitation tactics based on third-party application or browser plugins that contributed to most of the successful infections.
- Consider going through analysis of the malicious campaigns: IRS/PhotoArchive Themed Zeus/Client-Side Exploits Serving Campaign in the Wild; Tax Report Themed Zeus/Client-Side Exploits Serving Campaign in the Wild; PhotoArchive Crimeware/Client-Side Exploits Serving Campaign in the Wild; Facebook/AOL Update Tool Spam Campaign Serving Crimeware and Client-Side Exploits; Pushdo Serving Crimeware, Client-Side Exploits and Russian Bride Scams; Outlook Web Access Themed Spam Campaign Serves Zeus Crimeware
What these campaigns have in common, is the clear preference towards using Adobe Acrobat/Reader exploits only. Interestingly, the cybercriminals maintaining them are also relying on the KISS principle (Keep It Simple Stupid), since the campaigns are not necessarily exploiting the very latest flaws in Adobe's product line.
Case in point is the exclusive use of CVE-2007-5659; CVE-2008-2992; CVE-2008-0015; CVE-2009-0927; and CVE-2009-4324, with their choice either based on the already gathered metrics, which not surprisingly include traffic logs based on the hundreds of thousands of visitors hitting their fraudulent online properties. In this case, why would they bother buying a zero day on the underground market, when they already know that millions of end users are susceptible to exploits released two years ago? They won't.
What do you think - are Adobe's products insecure in general, is the company leaving the "window of opportunity" wide open for too long, or are their products on the top of the exploitation list due to the fact that millions of users continue using old versions of the company's software?
TalkBack.