Report: ZeuS crimeware kit, malicious PDFs drive growth of cybercrime
Symantec's recently released "Internet Security Threat Report trends for 2009" report, takes a deep dive into the world of cybercrime, by discussing some of the key driving forces behind its growth.
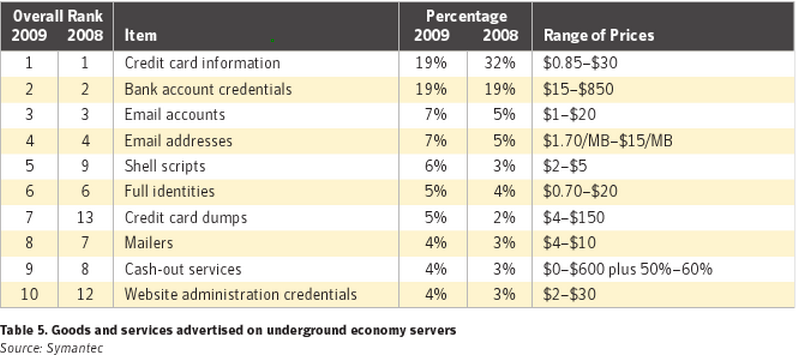
From the affordable price of the ubiquitous crimeware kit ZeuS, to the tremendous growth of malicious PDFs seen in 2009 based on the integration of Adobe flaws in popular malware kits , the report describes a cybercrime ecosystem whose entry barriers are becoming increasingly lower.
Key findings of the study:
- In 2009, the United States had the most overall malicious activity, with 19 percent of the total; this is a decrease from 23 percent in 2008, when the United States also ranked first
- The company observed 6,798,338 distinct bot-infected computers during this period; this is a 28 percent decrease from 2008
- Symantec created 2,895,802 new malicious code signatures in 2009, a 71 percent increase over 2008
- The top attacked vulnerability for 2009 was the Microsoft Windows "SMB2‘_Smb2ValidateproviderCallback()’ remote Code Execution Vulnerability"
- Of all browsers Symantec analyzed in 2009, Safari had the longest window of (vulnerability) exposure with a 13-day average
- Attack type "PDF Suspicious File Download" accounted for 49% of Web-based attacks for 2009. In comparison the use of malicious PDFs in 2008 was 11%.
- Crimeware kits like Zeus make it easier for unskilled attackers to compromise computers and steal information
Although the report is attributing the growth of cybercrime to the right factors, there's one element of the cybercrime ecosystem that has more effect that the overall availability and affordable price of the ZeuS kit - the Cybercrime-as-a-Service (CaaS) market model.
- Related services: Spamming vendor launches managed spamming service; 76Service - Cybercrime as a Service Going Mainstream; Zeus Crimeware as a Service Going Mainstream
What's more dangerous? The ever-decreasing price of the ZeuS crimeware kit, or the trending availability of Cybercrime-as-a-service propositions? Just how significant as a threat is the Zeus crimeware kit?
The company is not alone in observing the growth and success of the ZeuS crimeware kit.
September, 2009's “Measuring the in-the-wild effectiveness of Antivirus against Zeus” report by Trusteer, indicated that "the effectiveness of an up to date anti virus against Zeus is thus not 100%, not 90%, not even 50% - it’s just 23%." meaning that cybercriminals have clearly started excelling into the practice of bypassing signature-based malware scanners.
APWG Phishing Activity Trends Report for Q3 of 2009, also pointed out that based on the 22,754,847 scanned computers 15.89 percent were infected with banker malware. Moreover, Trusteer's latest data shows that one in every 3,000 computers from the 5.5m hosts they monitor in the US and UK, is currently infected with ZeuS.
Combined with the new features in the latest version of ZeuS (code protection with hardware-based licensing system), the kit's authors are clearly interested in strengthening their position as market leader of crimeware activity online:
- The new version of Zeus targets the growing population of Firefox users, in addition to Internet Explorer. Previous versions were incapable of exploiting Firefox to commit sophisticated online fraud against banks using strong layers of authentication. However, Zeus 1.4 supports HTML injection and transaction tampering for Firefox, two techniques which are effectively used to bypass strong authentication and transaction signing solutions.
It's clear that cybercriminals operate in an environment so comfortable, that it allows them to achieve their fraudulent objectives much easily than they used to a few years ago.
The keyword for ensuring that you don't become one of the millions of people infected with ZeuS or malware in general, is "situational awareness", next to the basic common sense tips for preventing a possible infection.