Researchers spot malware using a stolen government certificate
Researchers from F-Secure have spotted a digitally signed malware using a stolen government certificatebelonging to the Malaysian Agricultural Research and Development Institute.
From F-Secure's post:
Every now and then we run into malware that has been signed with a code signing certificate. This is problematic, as an unsigned Windows application will produce a warning to the end user if he downloads it from the web — signed applications won't do this. Also some security systems might trust signed code more than unsigned code.
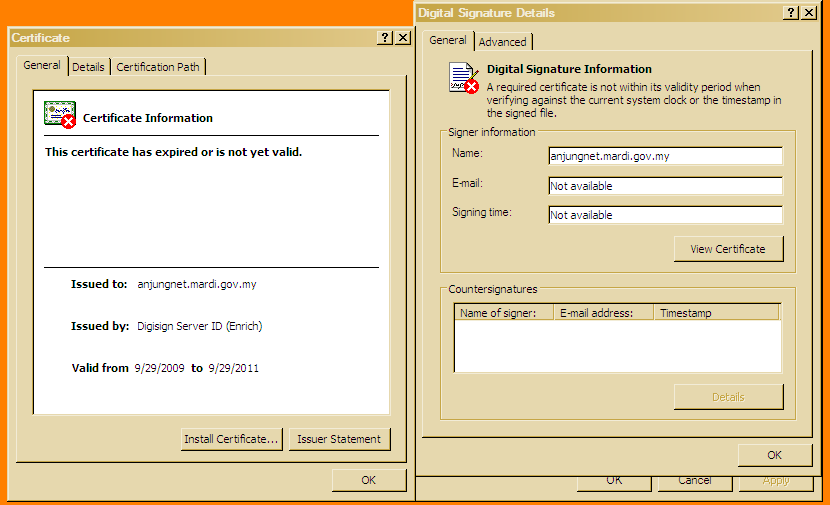
In some of these cases, the certificate has been created by the criminals just for the purpose for signing malware. In other cases they steal code signing certificates (and their passphrases) so they can sign code as someone else. We recently found a sample signed with a stolen certificate.
According to the vendor, the malware spreads through malicious PDF files that drop it after exploiting Adobe Reader 8. Interestingly, F-Secure notes that "This particular malware does not gain much advantage of the signature any more, as the mardi.gov.my certificate expired in the end of September."
The malware is currently detected as Trojan-Downloader:W32/Agent.DTIW.
Recommended reading: