Scareware pops-up at FoxNews
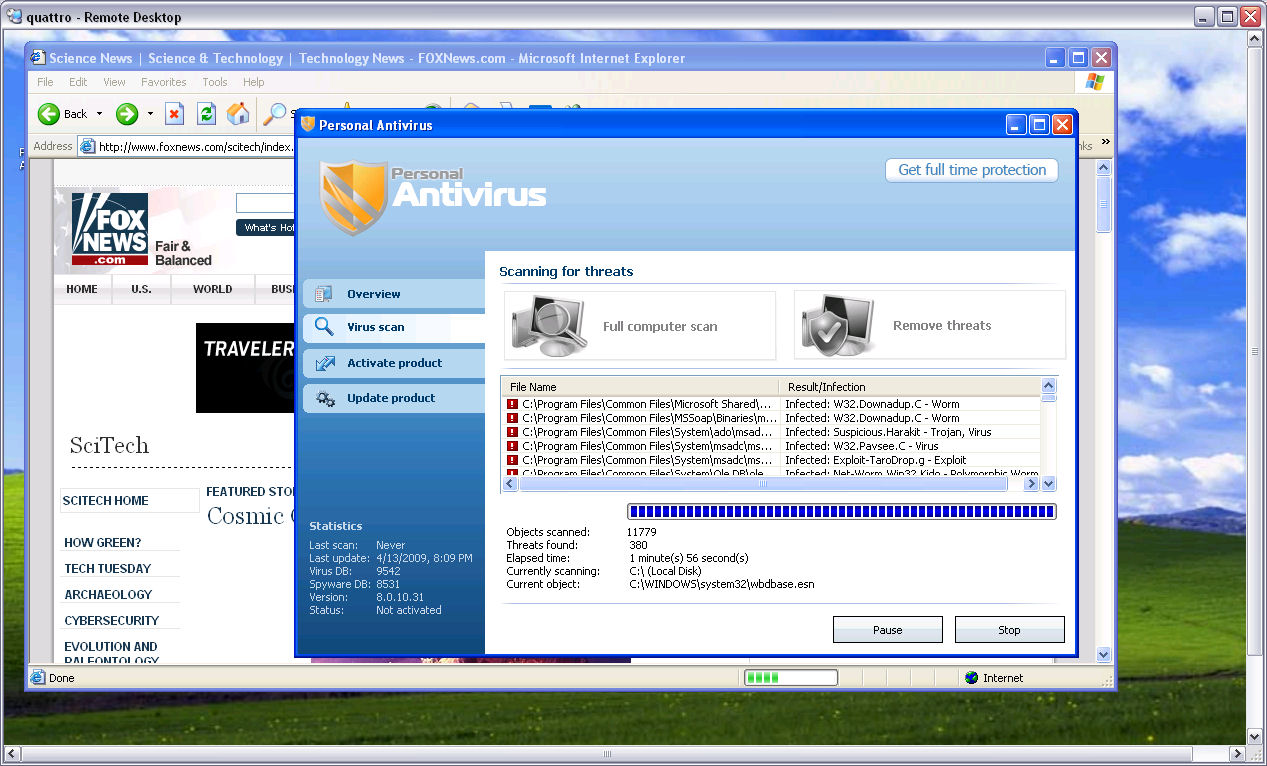
This most recent case of malvertising (MSN Norway serving Flash exploits through malvertising; Fake Antivirus XP pops-up at Cleveland.com) once demonstrates that whenever a direct access to a high-trafficked site cannot be obtained through a compromise, cybercriminals are logically exploiting third-party content/ad networks to achieve their goals.
Reproducing malvertising campaigns is tricky due to the geolocated nature in which the ads are served, as well as the cybercriminals' awareness on the fact that the amount of traffic which they expose to scareware is logically increasing the risk of having their campaign exposed. A risk which they hedge by temporarily inactivating the campaign or basically rotating the geolocation preferences and displaying the malicious ads to random countries.
- Go through related rogue security software posts: Scareware meets ransomware: "Buy our fake product and we'll decrypt the files"; Rogue security software spoofs ZDNet Reviews; Sony PlayStation’s site SQL injected, redirecting to rogue security software; Fake Antivirus XP pops-up at Cleveland.com; Google sponsored links spreading (scareware) rogue AV
Here's a brief analysis of the campaign which now appears to have been removed by FoxNews. Until the next time. According to SandShark, the warning issued by Google's Safe Browsing was in respect to the a domain redirector rd-point .net which is still active and is redirecting to the rogue ExtraAntivirus (extrantivirus .com) followed by previous known redirectors to another scareware RapidAntivirus.
It's worth pointing out that a scareware pop-up at a high-trafficked web site that is basically relying on the social engineering factor, is not as ugly as the introduction of a hybrid scareware demanding ransom for the decryption of files, or client-side exploits. With the list of the major web properties that have been historically affected by much more malicious malvertising incidents (e.g. MySpace, Excite, Expedia, Rhapsody) continuously expanding, maintaining a decent situational awareness next to a client-side vulnerabilities free host, mitigates a great percentage of the currently active threats.
Who's to blame anyway - the advertising networks for working with phony content publishers, the affected web sites for not policing themselves, or the web site visitor for the lack of situational awareness on emerging threats/scams like scareware?
Talkback!