Sony PlayStation's site SQL injected, redirecting to rogue security software
The latest high trafficked web site to fall victim into the continuing waves of massive SQL injection attacks courtesy of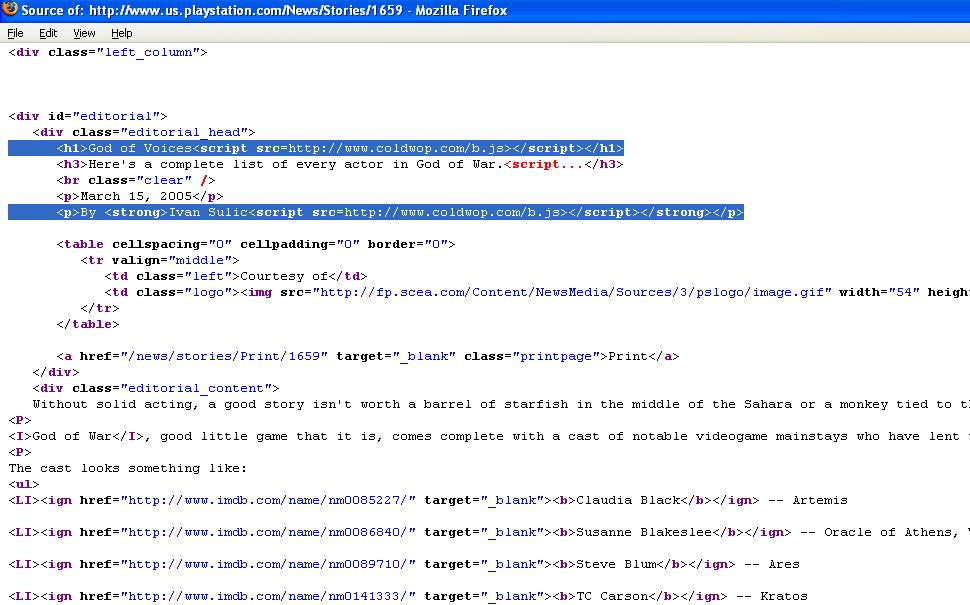
"Researchers at IT security firm Sophos have warned lovers of video games that pages on the US-based Sony PlayStation website have been compromised by hackers. Experts at SophosLabs have discovered that cybercriminals have successfully used an SQL injection attack to plant unauthorized code on pages promoting the PlayStation games "SingStar Pop" and "God of War".
At the time of writing the hacker's code attempts to dupe web surfers by running a fake anti-virus scan and displaying a bogus message that their computer is infected with a variety of different viruses and Trojan horses. The hackers' aim is to scare unsuspecting computer users into purchasing a bogus security product. Sophos warns, however, that it would be trivial for the hackers who have compromised the webpages to alter the payload so that it became more malicious, and installed code designed to turn Windows PCs into a botnet or to harvest confidential information from users. "
Sony PlayStation's site hasn't been hacked, it's been abused as a redirector to a malicious site serving rogue security software while participating in a SQL injection launched by Chinese hackers. Moreover, it's important to point out that, Sony's PlayStation site hasn't been on purposely targeted, it's been targeted automatically in between the rest of the 794 domains SQL injected with the same domain - coldwop .com. Let's get down the bottom of this campaign.
The number of SQL injected sites with this domain is close to 39, 000, and I'm in fact surprised that for the time being the
The botnet masters are continuing to put efforts into ensuring the survivability of their campaigns. In the previous ones they were injecting a single malicious domain on as many vulnerable sites as possible. These days, I'm coming across over 5 different injected domains on a single site, all of which are naturally in a fast-flux. This attack optimization approach clearly indicates that the botnet masters are keeping track of the success rates of their campaigns, and are applying metrics to assess them.
If you don't take care of your web application vulnerabilities, someone else will.
Related posts:
- Over 1.5 million pages affected by the recent SQL injection attacks - Redmond Magazine Successfully SQL Injected by Chinese Hacktivists- 200,000 sites spreading web malware, China's hosting the most - Google introducing Safe Browsing diagnostic to help owners of compromised sites - Microsoft ships free code auditing tools to thwart SQL injection attacks