Survey: 88% of Mumbai's wireless networks easy to compromise
The key findings of the survey are:
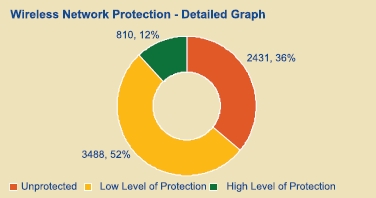
- Of the 6729 wireless networks seen, 36% appeared to be unprotected i.e. without any encryption
- 52% were using low level of protection i.e. Wired Equivalent Privacy (WEP) encryption
- Over 95% of the networks broadcast their SSID, with 25% of these using their router's default SSID
- Balance 12% were using the more secure Wi-Fi Protected Access (WPA)
What's the practical applicability of these insecurities?
Last week, it became evident that a group of Indian militants took unethical hacking courses, and once learning the basics of wardriving, used the insecure wireless network of a U.S expatriate to send emails claiming responsibility for serial bombings that took place in July and September :
"Roaming around Mumbai with Wi-Fi detectors, the suspects looked for open Wi-Fi signals and programmed the e-mail messages to be sent from hacked wireless networks prior to the blasts, the Indian police said. The technique used by the militants is similar to "wardriving," where hackers roam around to detect and access Wi-Fi networks with security weaknesses.
They would roam in a car to sites where wireless internet was available and then send the emails at designated timings, he said. "The police have seized a laptop, six computers, a radio frequency detector, a wireless router, anesthetic injections and tablets from the trio," said Gaffoor. Mohammed Akbar Ismail Chaudhary, the driver of the vehicle in which they travelled to send the threatening emails, has also been arrested. "Chaudhary had taken a house in Surat on rent under a fictitious name prior to planting bombs there," said Maria."
And whereas Deloitte didn't attempt to verify whether or not the wireless networks with default SSIDs were also using the default router passwords, that may web be the case as well. Living in Mumbai or not, consider going through the WiFi Security Awareness booklet accompanying the survey.
Sadly, Mumbai isn't an exception to the overall rule that best practices supposed to have been implemented, are not, since the same lack of basic security awareness can be seen literally all over the world - Caracas (Venezuela); London; Paris; China; Monterrey — Mexico; Sao Paulo – Brazil; England; Germany - CeBIT2006; Warsaw.