Targeted spear phishing attacks

A colleague of mine, Dave Wong, from Ernst & Young's Advanced Security Center in New York, pointed me to a really interesting article on targeted spear phishing attacks by John Markoff of the New York Times. Phishing has been really interesting to me lately, as I've seen a wave of discussions, black hat presentations, and technologies abound that deal with phishing and identity theft. In fact, this article comes just one day after I watched another colleague, Nitesh Dhanjani, provide a presentation to a Security Interest Group here in Chicago, organized by Kevin Richards of Ernst & Young and involving numerous large companies from the Midwest area. The phishing and identity theft talk that Nitesh gave really raised some eyebrows, especially when he discussed the targeted spear phishing attacks.
Phishing has always been a hot topic, but this targeted spear phishing is more mature and doesn't involve just dumb email blasts. The emails are typically targeted to individuals at companies that are high ranking officials, possibly CXOs. The contents of the email will usually include personally identifiable information of the victim to build confidence in the email. This might include full name, telephone number, position, etc.
The attack covered by Markoff in his blog is possibly one of the best examples of a targeted spear phishing attack that I've seen. As Markoff states:
Thousands of high-ranking executives across the country have been receiving e-mail messages this week that appear to be official subpoenas from the United States District Court in San Diego. Each message includes the executive’s name, company and phone number, and commands the recipient to appear before a grand jury in a civil case.
A link embedded in the message purports to offer a copy of the entire subpoena. But a recipient who tries to view the document unwittingly downloads and installs software that secretly records keystrokes and sends the data to a remote computer over the Internet. This lets the criminals capture passwords and other personal or corporate information.
An example image (courtesy of the New York Times blog by John Markoff) of the article is show below:
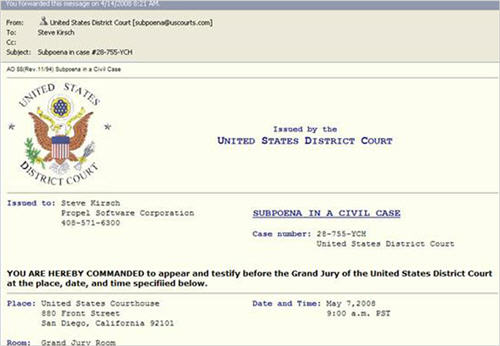
As Markoff states:
Another piece of the software allows the computer to be controlled remotely. According to researchers who have analyzed the downloaded file, less than 40 percent of commercial antivirus programs were able to recognize and intercept the attack.A large piece of Markoff's article continues on the statistics of the attack, as well as where the attack may be coming from (of course we're assuming China, although it could've came from the US and been just as devastating and anonymous, so what's the difference?), etc. I thought it might be interesting for me to discuss how to avoid this.
Obviously, the number one thing is user awareness. Unfortunately, the security community has been pushing user awareness for a decade, and the attackers just get less blatant and obvious about their attacks, making it more difficult for users to avoid this type of attack.
Of course, all the browsers and Google are trying to implement their own phishing site black listing, but as Nitesh mentioned in his presentation the other day, that's like playing whack a mole. Nitesh did mention that one thing phishing kits do is import in images and javascript, etc. from the site they are trying to pose as. An application could track the referer for requests for these types of resources and report remote referers to the company, allowing them to profile these sites (possibly even as they are being developed).
One thing that I've found as quite a creative solution is the use of something like a CAPTCHA for a SERVER to authenticate to the client (traditionally it's the other way around). Actually, Yahoo! Mail does this. You can choose some text or image, and if you don't see that image on a Yahoo! login page, then you know that you are being phished.
Of course, the attack reported in the New York Times is far more advanced and isn't really a phishing site as much as it is an email scam. I'd be interested if anyone had any other ideas on how to prevent this type of a phishing/email scam attack.
-Nate