Wardriving police: password protect your wireless, or face a fine
Internet users in Germany, whose wireless networks are left password unprotected, can be fined up to 100 euros, according to a recent ruling by Germany's top criminal court.
The ruling is in response to a musician's lawsuit against a user whose unprotected wireless network was used for downloading and sharing music over P2P.
Just how realistic is the ruling, from a security perspective? Is a weak password protected wireless network, any different than the one with no password security at all?
"Private users are obligated to check whether their wireless connection is adequately secured to the danger of unauthorized third parties abusing it to commit copyright violation," the court said. Internet users can be fined up to euro 100 ($126) if a third party takes advantage of their unprotected WLAN connection."
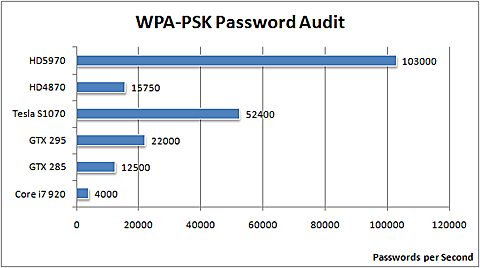
The ruling is not just missing the emphasis on the importance of strong passwords, but it also "doesn't expect users to constantly update the security of their wireless networks". Moreover, it's not even building awareness on the fact how the choice of the encryption protocol, can greatly slow down a potential attacker, in a combination with strong password.
With GPU-accelerated WiFi password recovery speeds prone to increase over time, as well as the increasing availability of DIY cracking kits, emphasizing on the use of strong passwords in a combination with with right encryption protocol, next to basic MAC address filtering, is the right security awareness building approach.
The main problem with insecure wireless networks, is the fact that malicious wardrivers can easily forward the responsibility for their activities to the owner of the unsecured wireless network.
It became evident that a group of Indian militants took unethical hacking courses, and once learning the basics of wardriving, used the insecure wireless network of a U.S expatriate to send emails claiming responsibility for serial bombings that took place in July and September -
“Roaming around Mumbai with Wi-Fi detectors, the suspects looked for open Wi-Fi signals and programmed the e-mail messages to be sent from hacked wireless networks prior to the blasts, the Indian police said. The technique used by the militants is similar to “wardriving,” where hackers roam around to detect and access Wi-Fi networks with security weaknesses."
Three years later, Mumbai's police started implementing the practice, in response to the abuse of insecure wireless networks by Indian militants:
Additional Commissioner of Mumbai Police K Venktesan told Business Standard: “If the Wi-Fi connection in a particular place is not password protected or secured then the policemen accompanying the squad will have the authority to issue a notice to the owner of the connection directing him to secure it."The police could issue a notice under section 149 of the Criminal Procedure Code (CrPC) to anyone found not securing their Wi-Fi connection and user may face criminal investigations.
Again in 2009, the Australian police also planned similar wardriving sessions:
The Queensland Police plans to conduct a 'wardriving' mission around select Queensland towns in an effort to educate its citizens to secure their wireless networks. When unsecured networks are found, the Queensland Police will pay a friendly visit to the household or small business, informing them of the risks they are exposing themselves to.
Although the problem with insecure wireless networks is often greatly underestimated, the big picture has to do with the fact that, when there are hundreds of thousands of password-unprotected wireless networks, this well known fact allows malicious attackers to efficiently propagate wireless malware. Related studies done on the subject, prove just how easy it is to execute such a malware campaign.
What do you think?
Does the "Wardriving police" concept have any future? Is your neighbor's insecure wireless network setting up the foundations for a cybercrime-friendly infrastructure, or are there much more important issues to take care of first, before starting to drop off "Insecure Wireless Network Detected!" brochures?
UPDATED: Several German readers have contacted me, since they believe the story was misinterpreted in a way that it makes it sounds as if the German police is wardriving around, looking for insecure wireless networks, and fining their owners:
"The music company and a troll demanded $250k compensation and damages. The owner appealed, and eventually reached the highest German court. This rejected the music company's claim, but ruled that the owner of a WLAN had a duty to secure the WLAN with the usual techniques at the installation time. The second ruling limited the liability of the WLAN owner for misuse by war drivers to 100 Euro, about $120. This is NOT a fine, and it doesn't mean that the police will look for unsecured WLANs and fine the owner."
The angle of this article was to emphasize on the increasing policing of insecure wireless networks across the globe with India and Australia cited as examples, the potential for forwarding the responsibility for malicious actions that took place over the insecure network to its owner in the context of the ruling, the futility of offering password protection advice without emphasizing on strong passwords in terms of the ever-improving brute forcing speeds, and to facilitate a conversation on the pros and cons of the "wardriving police unit" trend, clearly seen across the globe.
Talkback, and share you opinion.
Image courtesy of ElcomSoft's GPU-accelerated wireless security auditor.