Cryptolocker: Menace of 2013

Security software company Symantec this month named Cryptolocker the “Menace of the Year”.
Bitdefender logged over 12,000 victims in a week last month. That's not huge on a global scale but it should be a big enough number to make businesses pay attention.
While relatively few have been affected so far, many of those that have succumbed experienced a world of pain, as the victim stories below will attest.
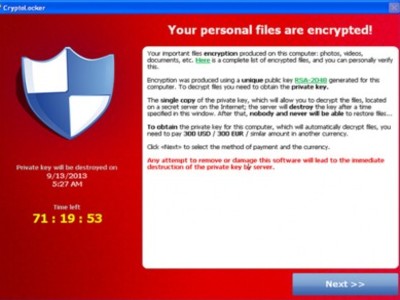
For anyone who hasn’t been paying attention, Cryptolocker is a variant of ransomware that unlike its predecessors does not work by locking a computer. Instead, it encrypts all data and demands a ransom in Bitcoins for the user to regain access.
It is usually distributed as an executable attachment disguised as a Zipped document and presented as an invoice or report or similar via a spam campaign.
All of that would be frightening enough for individual users, but Cryptolocker more than most trojans is a threat to businesses too. that's because it not only attacks data on the PC on which the executable was opened, but also on devices and drives connected to that PC.
So, what’s it like being on the receiving end?
One business in Australia that was shut down for five days with staff sent home on leave. Every network share’s business data was encrypted, over 64,000 files, after a staff member clicked on an attachment, despite telltale suspicious signs.
The firewall failed to detect and stop the infection as did antivirus software.
After the download, multiple files executed from a website and downloaded more malicious code to boot at startup via the registry.
Backup is key. It allows companies to enter their own personal Tardis and, like Dr Who, wind the clock back.
In this case it failed. The server had made room for the latest revised data by deleting all the old backups.
“The receptionist could not wait for the backup to complete on the last known backup date, and pulled out the USB drive early.”
This forced the IT fixers to restore from an older backup, losing many proposals and quotes. The system was recovered “but at great expense and emotional cost”.
Contrast that with a New Zealand law firm where, through good management and a bit of luck, backup was effective.
“Only 45 minutes of work was lost and as this all happened at around midday a lot of staff were at lunch so there was not much activity in regards to the data.”
The most famous victim to date is the Police department of Swansea, Massachusetts. Infected in November, the department decided to pay the ransom demand of two bitcoins, around US$750 at the time, and recovered its data.
In the process it not only revealed its vulnerability, but also drew heat for rewarding the criminals.
Cryptolocker is not entirely new. It emerged in September, but similar malware families date back as far as 2005.
Symantec says due to the publicity around ransomware, there are fewer uninformed potential victims and that had lowered the effectiveness of the tactic and its profitability.
Cryptolocker is their response.
“Due to this increased public awareness, in the last quarter of 2014 [sic] we have seen cybercriminals reorganize around a new type of extortion: Cryptolocker. This threat is pervasive and preys on a victim's biggest fear: losing their valuable data…
“If files are encrypted by Cryptolocker and you do not have a backup of the file, it is likely that the file is lost.”
There is no way to retrieve locked files without the attacker's private key. There can also be a time limit, usually 72 hours, in which to pay the ransom.
Almost comically, the criminals were making so much coin from a surging bitcoin value, they later reduced the ransom.
Users are being advised to take the following precautions:
- Backup all files regularly and off the network
- Lock down directories
- Make sure you have a business grade unified threat management (UTM) firewall with current subscriptions
- Keep all virus protection software up to date
- Make sure all employees are aware of this danger, trained in response and know to not open attachments without first talking to the IT department.