Fake Chrome, Adobe Flash updates

This morning I stumbled across what seems to be a new malware-spreading technique: A fake updates for Google Chrome and a fake "media player" update that is designed to look like it's coming from Adobe.
Both updates are digitally signed by valid VeriSign code signing certificates. This is not unprecedented, but it's highly unusual for malware authors to use an expensive provider like VeriSign. VeriSign Authentication Services are now part of Symantec.
The fake Chrome update uses a logo similar to Chrome's, but obviously distinguishable from it. The page correctly identifies the version of Chrome I was running (the current version) and then says that it "may be outdated".
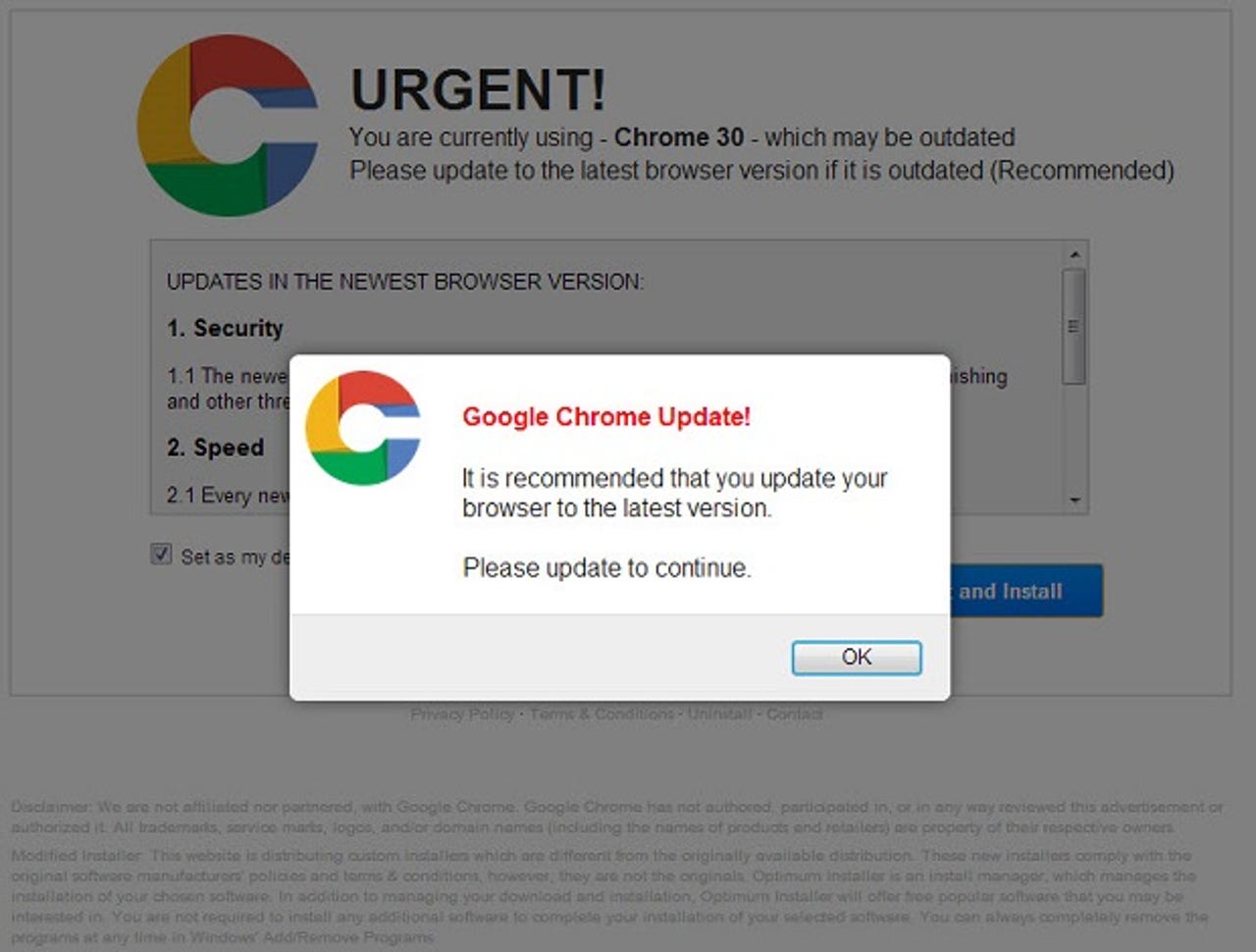
The file is named Chrome_Security_Plugin_Setup.exe and is 1.74MB. The file information identifies it as "Express Install" version "3, 7, 1, 0". The publisher, also identified in the VeriSign code signing certificate, is "TINY INSTALLER".
According to VirusTotal Friday morning, five out of the 48 products they work with recognized the file. Fortinet and ESET recognize it as W32/Kryptik. A Fortinet blog entry from earlier this year described a different variant of Kryptik as being focused on stealing FTP information, and congratulated the author on the high quality of his code.
The fake Adobe update is a little less clear on what product is mimicking. It commands the user "Upgrade your Media Player now [required]" and uses the look and feel of an Adobe update.
The file name is "Flash Player 12.exe" and is 814KB. The publisher in both the PE header and VeriSign code signing certificate is identified as "Air Software" and the PE Product name is "Adobe Flash Player" version 2.0.4.54. VirusTotal finds 9 of 48 companies that identify it, often as adware.
I discovered the files by accident. Through a typo in the address bar I went to an address from which the browser was redirected a couple of times until it ended up on a page which loaded one of the two attacks described above. I have notified the Administrative contact for the domain, which appears to have been parked.
The first time I encountered the files I got to the pages with no problem. Shortly thereafter, Google Safe Browsing API blocked access to them in Firefox and Chrome.