Microsoft: Windows, Mac malware gets in via Adobe, Java, Office

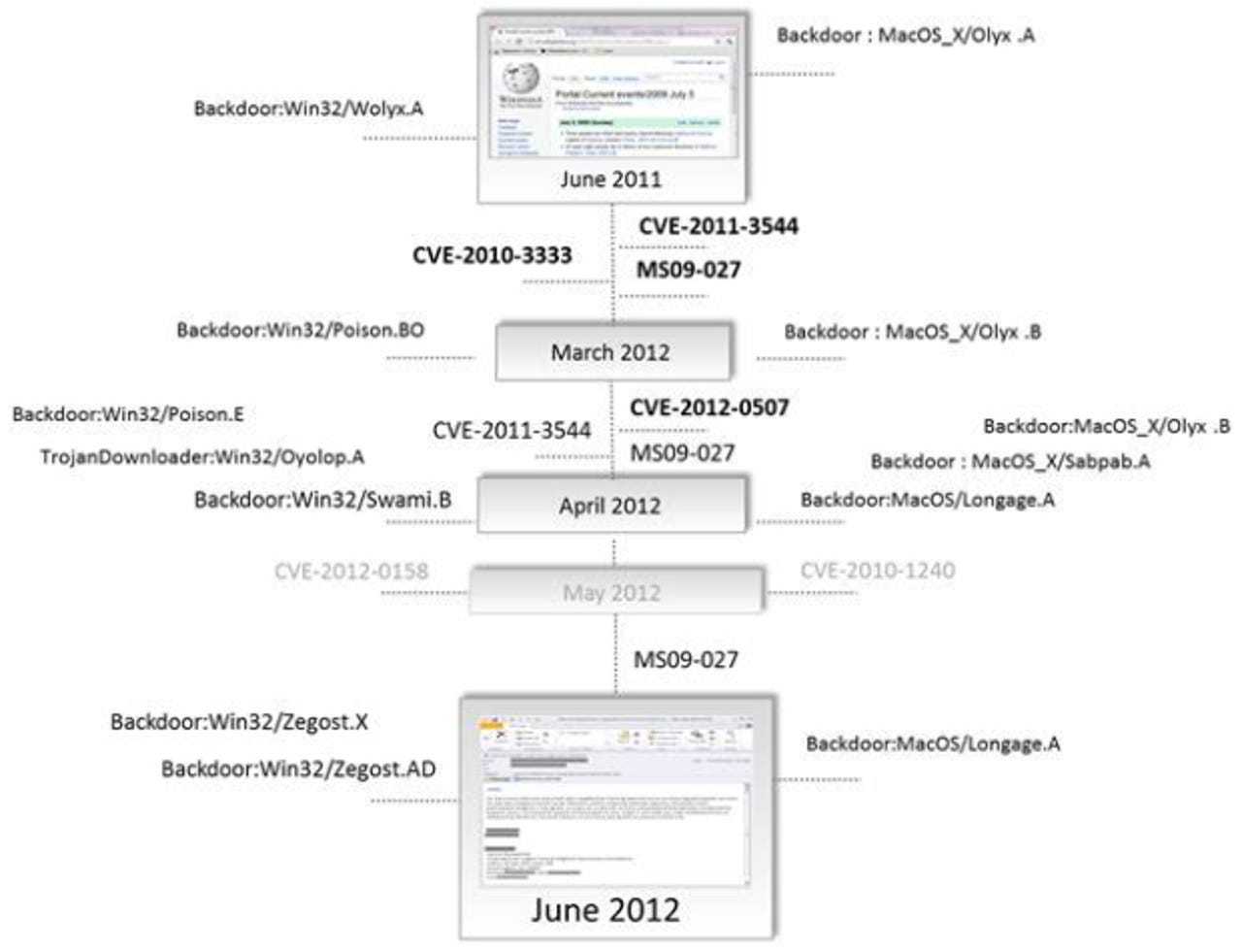
Microsoft has been doing some research into all the recent cross-platform malware (1, 2, 3) that attacks Windows, Macs, and sometimes even Linux. The company has concluded that current attacks exploit third-party vulnerabilities in software on these platforms. There are two ways the malicious code is being delivered, according to the software giant: via the Web and via e-mail attachments.
More specifically, Microsoft has found cybercriminals are currently leveraging 12 vulnerabilities in Java, seven in Adobe Flash, three in Adobe PDF applications, and three in Microsoft Office (one in Excel, two in Word). All of these can be used to target and attack multiple platforms. Since Java had the most, Microsoft has already recommended that you update it or kill it.
While these results are merely based on the samples Microsoft has identified, acquired, and processed, they confirm a trend other security researchers have been seeing with cross-platform vulnerabilities. It's basic economics. Malware writers love using a cross-platform plugin as an attack vector because it allows them to target more than one operating system, and thus more potential users. As such, we can expect the value and demand for these flaws to continue.
The most important thing to note is that all these aforementioned vulnerabilities have been patched. In fact, some of them are quite old. The security holes being exploited in Microsoft's software date back to 2009, the vulnerabilities in Adobe's software go back to 2010 and 2011, and the Java flaws range from 2010 to 2012.
"This highlights the importance of keeping security software up-to-date, and ensuring operating system and 3rd party security patches are installed (soon after they become available) in order to reduce the risk of malware infection," a Microsoft spokesperson said in a statement. "And, this best practice should extend to all devices and platforms, especially those in large enterprise networks."
See also:
- Microsoft: Update Java or kill it
- Cross-platform malware exploits Java to attack PCs and Macs
- Cross-platform Trojan checks your OS: Attacks Windows, Mac, Linux
- Cross-platform Trojan attacks Windows, Intel Macs, Linux
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan