Microsoft's security report shows Windows 7 is safer

The 64-bit version of Windows 7 is the least likely version of Windows to be affected by malware, with 2.5 infections found per thousand PCs, and Windows XP SP2 the most likely, with 19.3 infections found per thousand PCs. However, since this shows 98 percent of XP SP2 PCs as uninfected, it's not a good reason to panic. Oracle's Java is the most common attack vector, ahead of HTML/Script (mainly malicious iFrames) and the operating system. The adware JS/Pornpop, which serves pop-under porn advertising pages, is now the most prevalent bit of malware.
The numbers and charts come from Microsoft's Security Intelligence Report Volume 10, which covers the second half of 2010 in an 88-page PDF report. They are based on running Microsoft's Malicious Software Removal Tool (MSRT) as part of the Windows Update process, which means that hundreds of millions of PCs running pirated copies of Windows are excluded.
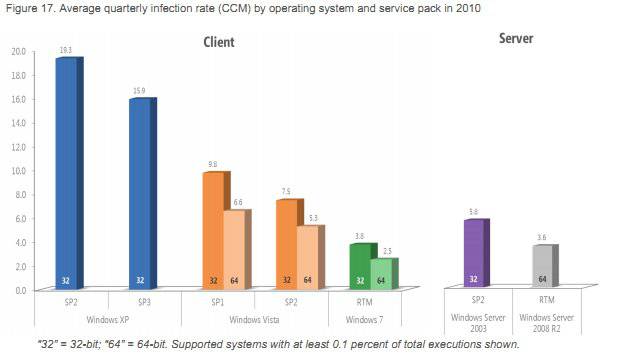
The operating system chart shows that Microsoft has got progressively better since the malware debacles that afflicted the early days of Windows XP. The customers who are still on XP SP2 have the highest incidence of infections with 19.3 found per thousand PCs, The numbers fall to 7.5 and 5.3 for Vista SP2, then to 3.8 and 2.5 for Windows 7 RTM. In each case, the 64-bit version does better than the 32-bit code. As Microsoft points out, the 64-bit versions "still appeal to the more technically savvy", which helps. So does the 64-bit version's PatchGuard, which the anti-virus industry tried to stop.
Another factor, of course, is that malware is a commercial business and attacks only the most profitable targets. Currently that's probably users with pirate or out-of-date copies of Windows XP, since the vast majority of attacks are aimed at exploiting security holes that have already been patched. (For those not paying attention, it's important to apply patches for CVE-2010-1885 and CVE-2010-2568.) There's relatively little financial incentive to attack more malware-resistant operating systems, but that is changing with the rapid adoption of Windows 7. Indeed, the infection rate for 32-bit Windows 7 jumped by almost a third compared with the first half of the year.
Microsoft sees increased security as one reason for upgrading from XP to Windows 7 and, in truth, there are several of those. However, the reduced incidence of malware infections (including adware) may be overstated. There is clearly a big drop from 15.9, scored by XP SP3, to 2.5, for 64-bit Windows 7. Still, in terms of PCs found "clean", it's only a reduction from 98.4 percent to 99.75 percent. The vast majority of people who are smart enough to use Windows Update will not have malware infections removed by MSRT whether they use XP SP3 or Windows 7.
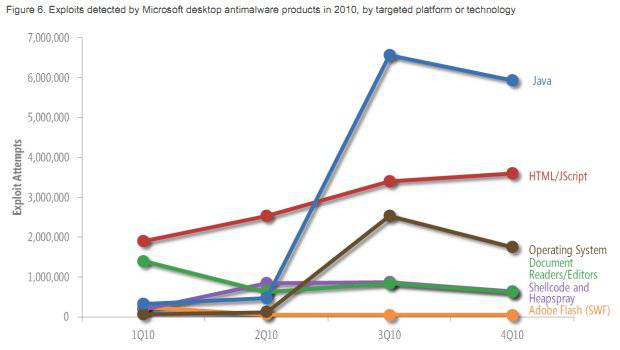
In terms of exploits classified by their target platform or technology, Oracle's Java remained the market leader. Microsoft notes (page 19):
"Malware written in Java has existed for many years, but attackers had not focused significant attention on exploiting Java vulnerabilities until somewhat recently. In 3Q10, the number of Java attacks increased to fourteen times the number of attacks recorded in 2Q10, driven mostly by the exploitation of a pair of vulnerabilities in versions of the Sun (now Oracle) JVM, CVE-2008-5353 and CVE-2009-3867. Together, these two vulnerabilities accounted for 85 percent of the Java exploits detected in the second half of 2010."
There was also a dramatic rise in the number of exploits targeting Microsoft's browser, Internet Explorer. Microsoft adds: "Most of these exploits targeted CVE-2010-0806, a vulnerability that affects Internet Explorer versions 6 and 7 running on versions of Windows earlier than Windows 7."
The free report also covers topics such as email, spam, phishing, malicious websites, and document-based exploits. There are maps of Global Infection Rates, which show that South Korea was the worst place for malware, with 40.3 computers cleaned for every thousand MSRT executions. After that came Spain (33.2), Turkey (32.8), Taiwan (24.3), and Brazil (20.8). Large countries with low infection rates included the Philippines (3.1), India (3.8), and Japan (4.4).