New Internet Explorer 10 zero-day exploit targets U.S. military

Hackers are actively exploiting a newly discovered zero-day flaw within the browser Internet Explorer 10, and have used it in a watering hole attack on the U.S. Veterans of Foreign Wars' website.
Discovered by security researchers from FireEye and dubbed "Operation Snowman," the campaign -- believed to be operating out of China -- is similar to Operation DeputyDog and Operation Ephemeral Hydra, both of which used zero-day flaws to deliver remote access trojans in order to hit strategically important targets.
According to the researchers, the zero-day exploit in Operation Snowman (CVE-2014-0322) is a "classic drive-by download attack," a phrase relating to browser-based attacks that hoodwink website visitors in to visiting malware-infected sites. The security firm says the attackers added an iframe to the VFW website's HTML code which then loaded the infected page in the background. When this code is loaded within the IE 10 browser, a Flash object is ran which downloads, decodes and executes an XOR-encoded payload from a remote server.
Following the discovery of the flaw, Malwarebytes researcher Jerome Segura tested the exploit and was able to reproduce a successful infection on Windows 7, Internet Explorer 10 with the latest version of the Flash Player. As Segura notes, the security flaw is "a use-after-free bug that gives the attacker direct memory access at an arbitrary address using a corrupted Adobe Flash file. It then bypasses both Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP)."
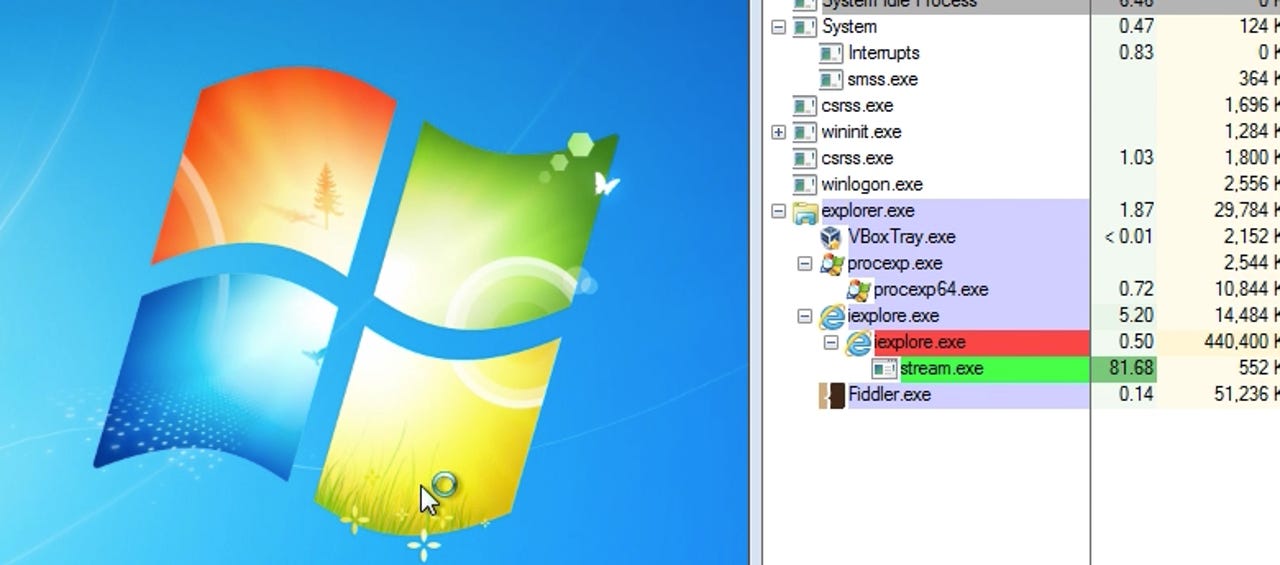
However, if a user is browsing with a different version of IE or has installed Microsoft’s Experience Mitigation Toolkit (EMET), the exploit will not function.
"A possible objective in the SnowMan attack is targeting military service members to steal military intelligence," FireEye researchers say. "In addition to retirees, active military personnel use the VFW website. It is probably no coincidence that Monday, Feb. 17, is a U.S. holiday, and much of the U.S. Capitol shut down Thursday amid a severe winter storm."
FireEye and Microsoft are currently collaborating as part of an investigation in to the IE 10 flaw and subsequent exploit. The Redmond giant has confirmed the vulnerability, stating:
"Microsoft is aware of targeted attacks against Internet Explorer, currently targeting customers using Internet Explorer 10. We are investigating and we will take appropriate actions to help protect customers."
Disclosure of the security problem comes two days after Microsoft released a large swathe of update patches for Internet Explorer editions. In total, seven updates have fixed 32 vulnerabilities, and an update for IE 10 alone contained 15 flaw fixes.