New Mac malware spies on you via Adium, Firefox, Safari, Skype

Earlier this week I wrote about a new Mac OS X Trojan that drops different components depending on whether or not it is executed on a user account with Admin permissions. The threat installs itself silently (no user interaction required) and does not need your user password to infect your Apple Mac. Further analysis now shows that the malware is actually set up to spy on your browsing and instant messaging activities.
Intego, which had to update its anti-malware signatures upon discovering the threat, refers to it as "OSX/Crisis." First, the malware arrives as a Java applet (adobe.jar, AdobeFlashPlayer.jar, or something else entirely) that relies on social engineering. Given that OS X 10.7 Lion doesn't include Java by default, however, it's very likely there are other ways for it to find its way onto your Mac.
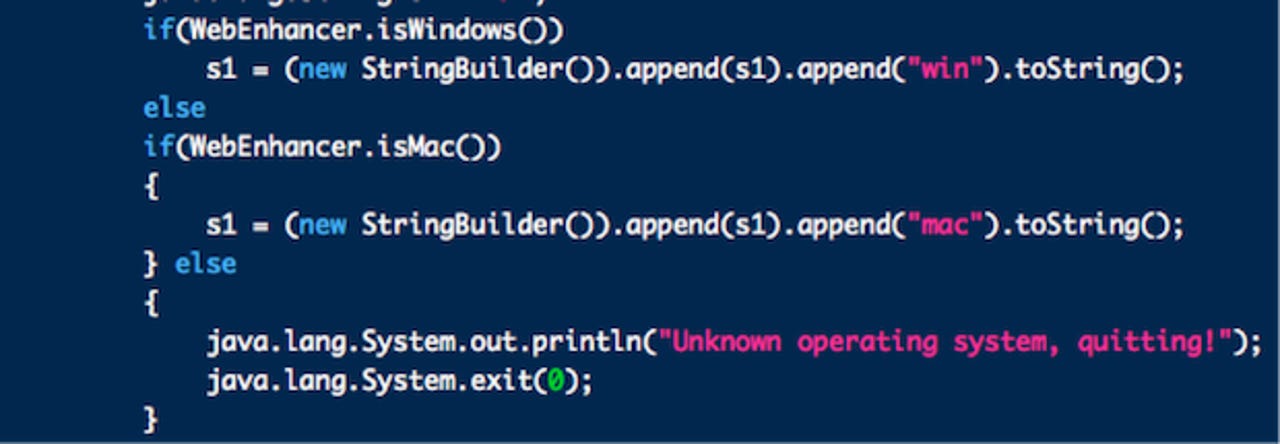
Once executed, the Java applet checks to see whether it's on Windows or OS X (as you can see in the code snippet above). Recently, cross-platform Trojans have become more and more popular (one, two, three) and are probably one of the reasons Microsoft wants you update Java or kill it.
This Mac Trojan is like most: when run, it installs silently to create a backdoor. What makes this threat particularly worrying is that depending on whether or not it runs on a user account with Admin permissions, it will install different components, which use low-level system calls to hide their activities. Either way, it will always create a number of files and folders to complete its tasks; the backdoor component calls home for instructions to the IP address 176.58.100.37 every five minutes.
If the dropper runs on a system with Admin permissions, it will drop a rootkit to hide itself. The malware creates 17 files when it's run with Admin permissions, 14 files when it's run without. Many of these are randomly named, but there are some that are consistent. With or without Admin permissions, this folder is created:
/Library/ScriptingAdditions/appleHID/
Only with Admin permissions, this folder is created:
/System/Library/Frameworks/Foundation.framework/XPCServices/
We already know the file is created in a way that is intended to make reverse engineering tools more difficult to use when analyzing the file (common in Windows malware, but not so much for OS X malware). Upon closer inspection, however, it turns out the backdoor patches several applications to spy on an infected user's activities when they use those programs: Adium, Skype, Microsoft Messenger, and Firefox. It even patches the Activity Monitor to hide itself from the user.
Intego says the malware allows the person operating it to:
- Spy on Skype audio traffic and recording all conversations and phone calls.
- Spy on Safari or Firefox browsers to record URLs and screenshots.
- Record IM messages in both Microsoft Messenger and Adium.
- Send file contents to the control server.
Furthermore, there are sections of code that point to this threat being part of Remote Control System (RCS), a €200,000 commercial malware package that is sold mostly in the U.S. and Europe. Since Intego has yet to see the malware in the wild (it was discovered on VirusTotal, a service for analyzing suspicious files and URLs), and since the security firm's analysis concludes the threat is very advanced, you're unlikely to get infected by it.
Still, if you use your Mac for critical work, store classified information on it, or are in general someone of importance, this Trojan is cause for concern. It further underlines the importance of protecting Macs against malware with the latest security updates as well as an updated antivirus program.
"From a technical perspective, this is a very advanced and fully functional threat," an Intego spokesperson said in a statement. "Due to the apparent cost of this malware package, it’s unlikely that this will be more than a targeted attack. But if you are the intended target, it’s very important that you have good security measures. Most vendors now have protection for the known components, but it’s unlikely that this is the last version of this malware (or its installation packages) that we will see."
Curiously, this particular malware only affects OS X 10.6 Snow Leopard and OS X 10.7 Lion. As I'm sure you know, OS X 10.8 Mountain Lion just came out.
I have contacted Intego to ask them if the latest version of Apple's operating system is vulnerable. I will update you if and when I hear back.
Update at 2:30 PM PST - Sophos, which detects this threat as OSX/Morcut-A, has more to add. The security firm found that its code can include hooks to control and/or monitor the following operations:
- Mouse coordinates.
- Instant messengers.
- Location.
- Internal webcam.
- Clipboard contents.
- Key presses.
- Running applications.
- Web URLs.
- Screenshots.
- Internal microphone.
- Calendar data & alerts.
- Device information.
- Address book contents.
"In short, if this malware managed to infect your Mac computer it could learn an awful lot about you, and potentially steal information which could read your private messages and conversations, and open your email and other online accounts," a Sophos spokesperson said in a statement. "By the way, if you're curious about where the name 'Crisis' came from, it's a name which appears inside the malware's code. As far as we can tell, the author appears to have wanted his malware to be called 'Crisis'."
Update at 5:00PM PST - No, OS X 10.8 is not affected by this malware.
See also:
- New Mac Trojan installs silently, no password required
- New Flashback variant silently infects Macs
- New targeted Mac OS X Trojan requires no user interaction
- Over 600,000 Macs infected with Flashback Trojan
- Cross-platform Trojan checks your OS: Attacks Windows, Mac, Linux
- Microsoft: Update Java or kill it