Trust the PKI or it's anarchy on the Internet

The PKI (Public Key Infrastructure) is an imperfect system, requiring trust in organizations that not everyone trusts. Even so, nearly everyone on the Internet is dependent for their security, to some degree, on the system of digital certificates and the software which employs them.
The system fails now and then and, when it does, it rightly attracts a lot of attention. It works 99.(some very large number) percent of the time, but the only way it works is if we submit to it. We have to put our trust in the certificates issued by Symantec and Comodo and their ilk. And it's not just them, it's also Apple and Microsoft and many large telecom companies and, in many countries, the government. (Of course, we now know that, even in the US, if you trust Microsoft and Apple you implicitly trust the US government.)
There's really no choice. Even for those who know what's going on with their SSL and certificates, it's impractical to try to trust the system just a little or to pick and choose. The vast bulk of the Internet population wouldn't even know what to do.
So it's unhelpful to complain, as German magazine C'T does, that Microsoft's automatic updating of root certificates lacks transparency. (That article is in German; I can't find an official English translation and I'm mostly relying on the account of Johannes Ullrich, who discussed the article in his daily ISC StormCast on July 31.)
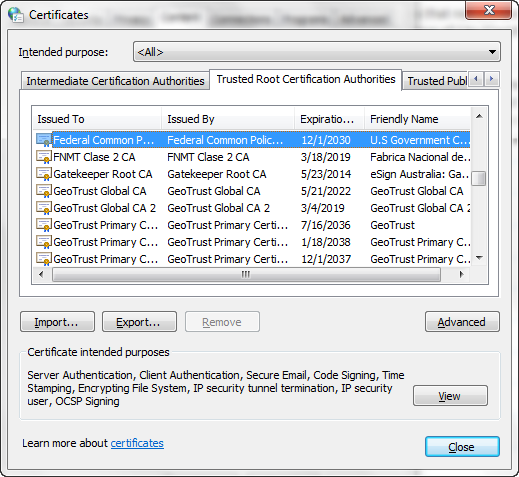
Trusted root certificates are digital certificates that are trusted inherently in the system. Individual certificates for sites cannot be trusted on their own, so they refer up a certificate chain of issuers which the client can verify up to the root. The issuers of these roots - generally Certificate Authorities - are the ones you have to trust. Below is a screen grab of the Windows 7 trusted root certificate list.
C'T's complaint is that Microsoft automatically issues updates to their root certificate list without user interaction or any clear indication that it has made any changes.
The implication, and based on Google Translate I think C'T says this out loud, is that Microsoft could issue a root certificate at the behest of the NSA or some other shadowy agency to assist them in compromising your computer and accounts.
Yes, of course they could do this. We're talking about Microsoft, the people who write the operating system. They could put code to compromise your computer right into the operating system. But the government doesn't need to use Microsoft to issue malicious root certificates; as the screen grab above shows, the US government has its own certificates in the list. (Of course, if you don't trust Microsoft, why should you trust that the list itself is accurate?)
Automatic updating of root certificates is essential to the proper functioning of the PKI. At times the list changes: root certificates are issued and revoked, or they may even expire. In the case of a root certificate revocation it's essential that the update go out quickly in order to protect users. In that same Certificates manager in the screen grab you can find the "Untrusted Publishers" tab; several of those certificates are root certificates.
Too many users ignore updates to let this go unaddressed. Incidentally, it's not just Internet Explorer; Google Chrome, Apple Safari and a lot of other software - basically any software which uses the Windows CryptoAPI - relies on the Windows Certificate Store, which is the database displayed in the Certificates list in the image above.
Mozilla software, including Firefox, is the exception. They have their own crypto code and their own certificate store, and they update it too, although they do so through documented updates such as this one. Microsoft doesn't announce their root certificate updates (that I've found), but they do provide the updates separately in the Download Center so you could look them up there. And there's nothing new about this practice by Microsoft. C'T links to a Technet article on how Windows Server 2003 performs this function. .
Microsoft provides ways for you to turn off the updates using registry hacks or group policy, but it would be a bad idea to do so. If you do, you can expect errors in the browser (IE, Safari, Chrome) and elsewhere indicating certificates being signed by untrusted authorities.
Ullrich says that automatic updating is "kind of a good thing," but I wouldn't qualify it the way he does. It's an obviously good thing, and the counterarguments are petty. Ullrich points out that the only real alternative, unless you reject the PKI entirely, is to create your own list of trusted root certificates and install it manually. Almost nobody does this; it's completely impractical.
What are the checks and balances on the software companies and CAs? One is the market; if a CA gets a bad rep they may lose customers to their numerous competitors. The CAs know that their business depends on their reputation. In theory the market also applies to the software companies in this way, but it's hard to see certificate management being a major factor in customers shifting between operating systems or even browsers. The companies, like Microsoft and Mozilla, that manage certificate stores, also have policies for inclusion of root certificates that could result in a certificate being removed for insecure practices of the organization.
But the main check is the research community. These are the hackers, like Moxie Marlinspike, who focus on the weaknesses in the CA system and put pressure on them to work as best they can, even if, as Moxie would argue, the system itself is fundamentally flawed. Like I said, CAs need to have a good reputation, and hacker exposés are bad for business.
There are experiments going on for how to replace the CAs as part of the PKI, but they are clearly not ready for prime time, and it's not at all clear that they will scale to Internet levels of demand. The best-known is TACK (Trust Assertions for Certificate Keys) by Marlinspike and others, but the standards draft they wrote has a lot of dust on it and I see no evidence the IETF is interested.
No, your choices are to trust all those big, bad corporations or anarchy. I don't think that's hyperbole; an Internet without a CA system today would be anarchy. Nobody could perform any sensitive operations like banking and you'd be nuts even to do email on it. So just accept that you have to trust Microsoft and Symantec and, for what it's worth, the NSA.