Six big iOS 8 issues for enterprises

IT must be prepared for the new capabilities
The new generation of Apple iOS hardware and software forces enterprises once again to make tricky decisions. It's a BYOD world and now employees will be bringing devices with new, significant functions. Enterprises will want to adopt some of them on them actively. Others may be just for the users, but they still complicate the situation for IT.
I spoke with Ojas Rege VP Strategy at MobileIron, a leading EMM (Enterprise Mobility Management) vendor about these challenges. He thinks enterprises aren't asking the right questions. Rather than look for security and management feature charts, they should ask "what are the implications for our organization of extensions, handoff, Healthkit and other major mew iOS 8 features? Should we allow users access to them? Should we adopt them for our own use?
Rege identified six iOS 8 issues that enterprises must confront.
Handoff
In iOS 8 and OS X Yosemite, when the user moves between devices, the same program will retain context. As Apple puts it, "Handoff lets you pick up right where you left off."
The different devices have to be signed into the same iCloud account. Many built-in apps (Apple lists Mail, Safari, Pages, Numbers, Keynote, Maps, Messages, Reminders, Calendar, and Contacts) support it. But developers can build Handoff into their own software.
Do you want your corporate applications and data being moved around this way and through iCloud? Some of the devices may be unmanaged; is this something you want to allow? It's time to set some policies and see if your EMM platform allows management of Handoff.
At the same time, you might want to build into your in-house apps, but be very careful to follow your own policies. Some data may be critical enough that Handoff is an unwarranted risk.
Devices get ever more personal
From the dawn of the BYOD age, devices have had personal information on them, if only innocuous things like family photos. With iOS 8 and the Apple Watch, Apple has raised the significance of personal data to a new level.
The iOS 8 Health app and third-party apps built with the HealthKit may only contain data like how long your last run was or how many calories you ate this week, but they might also have critical health data on which your life could depend.
You can back this data up to iCloud if you wish — it is encrypted both in transit and at rest — but Apple won't do anything with the data without your permission. This means that the critical data may only exist on the iPhone.
In light of this, the brute force policy of remotely wiping data on devices in some circumstances could be a real problem. If the organization hasn't been rigorously separating the management of user and enterprise data, it had better start now. Except in very rare cases you never want to do a full wipe. You need to be able to do partial wipes properly.
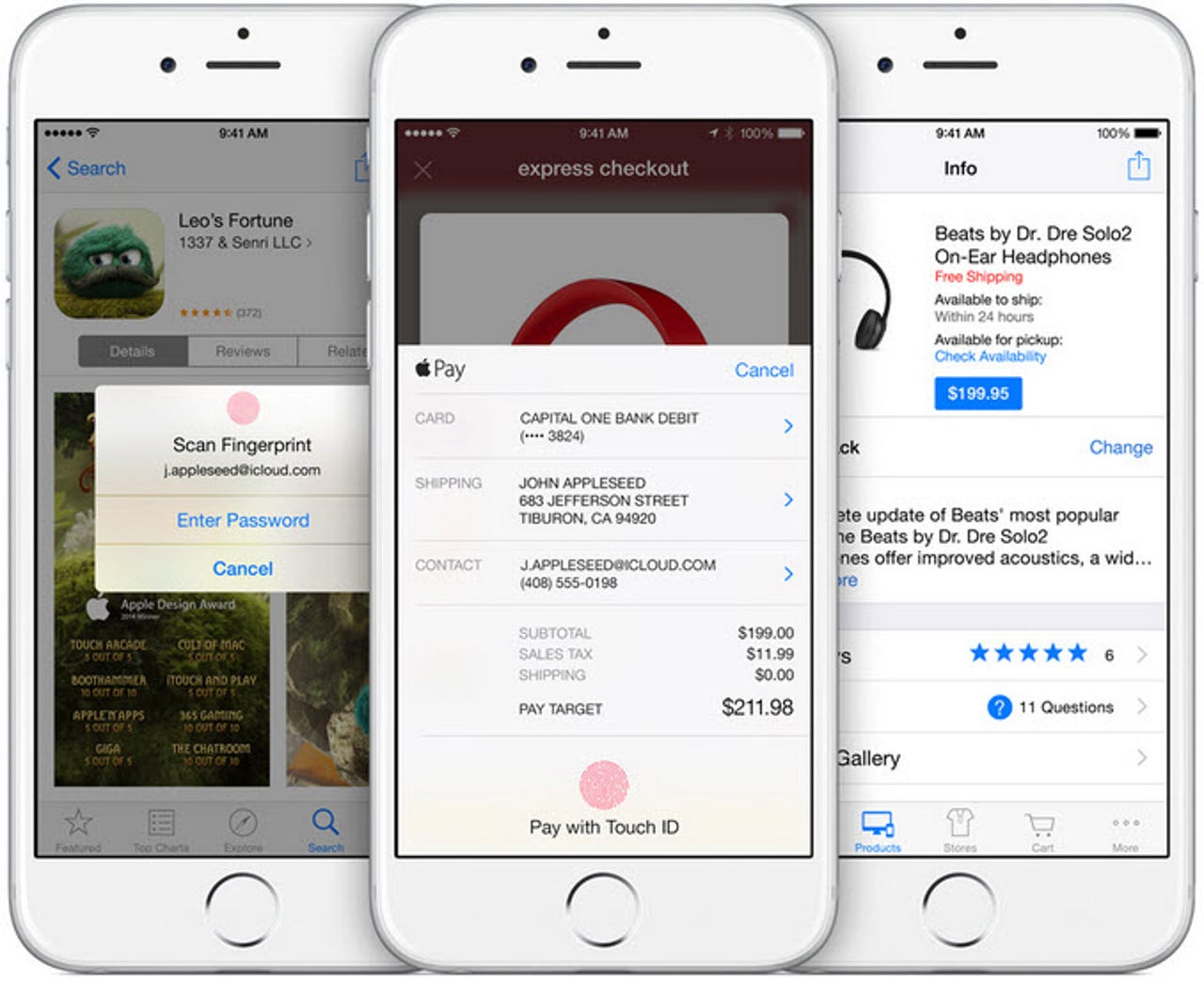
Give your apps the finger
Apple's Touch ID fingerprint sensor had a limited introduction in the iPhone 5s and iOS 7. With iOS 8 Touch ID is available for general use as an authentication mechanism. Enterprises can use it in their own in-house apps. ISVs like LastPass are implementing it.
MobileIron's Rege thinks enterprises should consider using Touch ID. Two-factor authentication constantly shows its value with every theft of userids and passwords. Even as a sole factor Touch ID is strong, and Apple may have created the first biometric experience with sufficient usability for broad use.
Extensions: your program runs outside the app
Developers can write new types of programs in iOS 8 called extensions. Extensions allow third-party programs to extend the functionality of the system.
There are many different kinds of extensions and they provide a broad sharing framework for software in the system. They can operate in the background independent of any foreground app. Using extensions, whether your own, from Apple or a third party, create opportunities for data loss. Enterprises need to define policies for their use.
Pictured here are three examples of extensions:
- First a Document Provider, in which an ISV can define how other programs work with their file types. These are iOS only
- Second is a Custom Keyboard, in this case Swype, famous from Android. These are also only for iOS.
There are several other types:
- Widgets, which perform a quick update or task in the Today view of Notification Center, and which run on either iOS or OS X.
- Shares, which post to a sharing website or share content with other entities, such as social sharing websites or upload services. These run on iOS or OS X.
- Actions, which edit or display content. These run on iOS or OS X.
- Photo Editors, which can edit a photo or video within the Photos app. Photo Editors are iOS only.
- Finder Sync which displays the sync status directly in Finder and only on OS X.
The right-hand screen in the image is an example of a Safari Custom Action. These can extend Safari and have access to the DOM. There are two forms of an action: A View Controller and No View.
New-Fangled Comm feature
NFC has always been designed for payments, and that's the main thing Apple is doing with it. Other companies have been shipping NFC-enabled phones for years, but it didn't amount to much in the real world. Now that it's in the iPhone and Apple Watch many in the payments business are taking up the bet.
Payments may or may not be interesting to enterprises, but NFC has other applications, and others have been using them for years.
NFC has been supported in BlackBerry devices since 2011 and the company describes uses of it as an ID badge, tickets for events or travel, sharing of contacts or other small amounts of data, even assisting with Bluetooth pairing or router configuration. In some of these applications, the NFC can act as a second authentication factor.
Get your developers on-board
The improvements in iOS 8 create numerous opportunities for data loss and other security problems. Developers need to know what they can and cannot do.
Most enterprises outsource app development, perhaps to multiple outside shops. If you're not clear with them what is required of them and what is not allowed, you open up the possibility that someone will use some neat feature just because they think it's cool or expeditious.