Safari on Mac OS exposes web login credentials

Kaspersky researchers have discovered that Apple's Safari web browser on OS X stores session information, including the username and password, in a plain text XML file, available for any user to read.
[UPDATE: I have checked with Kaspersky and they say that this problem was fixed in Safari 6.1. This fact is not in their blog, or at least it wasn't in the initial version. Since Safari 6.1 comes by default on OS X 10.9 (Mavericks), users on that OS are not affected. Apple also did supply a Safari 6.1 update for OS X 10.8 (Mountain Lion) and OS X 10.7 (Lion), so users who apply that update will not be vulnerable.]
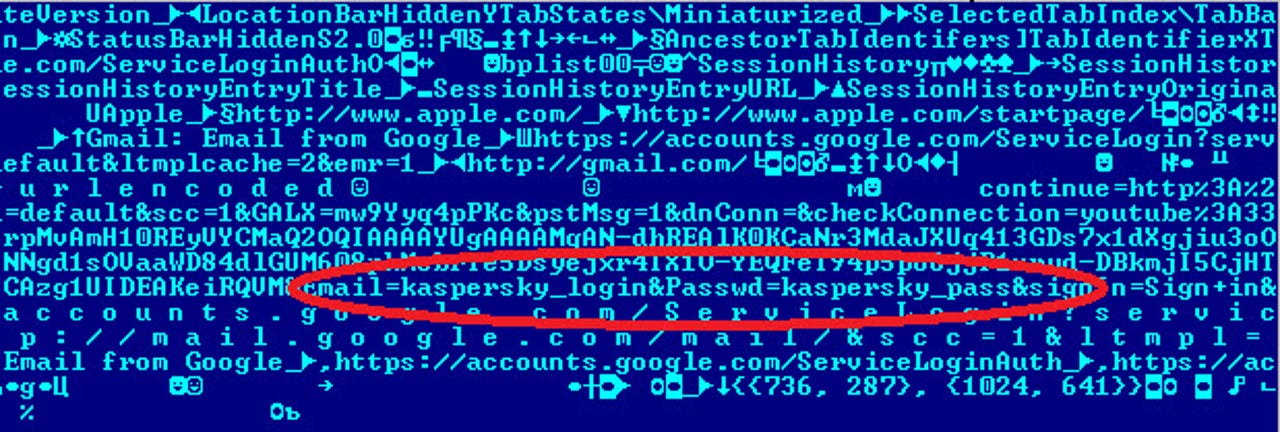
Like many other browsers, Safari can save the locations and state of open web pages when the user exits in order to reestablish then when the browser is reopened. When Safari does this, according to Kaspersky researcher Vyacheslav Zakorzhevsky, it saves the session state in a file named LastSession.plist. The file is in a hidden directory, but access to it is not restricted. The data in the file is unencrypted, even if the session itself used HTTPS.
Kaspersky says they have confirmed the issue on these versions of OS X and Safari:
- OSX10.8.5, Safari 6.0.5 (8536.30.1)
- OSX10.7.5, Safari 6.0.5 (7536.30.1)
They say nothing in their blog about 10.9, the current and only supported version; we are researching this and will update this article if we learn more. They also don't say if the same problem exists on Safari on other platforms, basically Windows and iOS. [UPDATE: As I mention above, OS X 10.9 and earlier versions running Safari 6.1 are not vulnerable.]
The potential downside is that a malicious user or program, even with an unprivileged account, could gain access to a user's web site login credentials. Kaspersky says "As far as we are concerned, storing unencrypted confidential information with unrestricted access is a major security flaw that gives malicious users the opportunity to steal user data with a minimum of effort."
They have informed Apple, but have not yet received a response.
[UPDATE: There really isn't anything for Apple to respond to; they have addressed the problem in Safari 6.1, although they did not mention such a fix in their vulnerability disclosure for that version.]