Six Clicks: Encryption for your webmail

So you want maximum security for your email...
It shouldn't have been any surprise at all, but Edward Snowden's leaks of NSA information have raised awareness of the fact that our data in public clouds, like Gmail, is not entirely private. The government can get a warrant for it and the cloud company can (make that "has to") give them access to all your data. Or they can spy on the internal communications of the cloud provider and not bother with the warrant.
So what can you do? For a very long time you've been able to use PGP (Pretty Good Privacy) and similar software to make encryption end-to-end, so that only you and the person with the right encryption key can see the contents. Everyone else only sees "ciphertext" which is only crackable with an inordinate amount of time and computing resources.
Yesterday Google announced a new development effort to make the use of strong, end-to-end encryption in Gmail easier to use. It's called "End-To-End" and, for now, it's just an alpha-stage programming project. It's written as a Chrome extension that uses OpenPGP.js, an open source OpenPGP implementation written in JavaScript, to run the encryption/decryption on the local computer inside the browser.
PGP has always been the gold standard for privacy in email, but notorious for poor usability. The idea of End-To-End is that by implementing PGP inside Chrome, it can be made easier to use.
One big usability barrier for PGP is that it relies on a trust model called the "web of trust," illustrated here. Everyone has to trust people specifically and keep track of who they trust and what their keys are, although they can make trust transitive by signing someone else's key: If Alice signs Bob's key, they anyone who trusts Alice will trust Bob.
If this sounds complicated, that's because it is. Can Google make it easy? If not, it may not matter.
(Image courtesy GnuTLS)
Previously on Six Clicks:
Six Clicks: How do you keep track of all your passwords?
Six clicks: How hackers use employees to break through security
Six clicks: Weird tricks that will actually make you happier with Windows 8.1
Six clicks: Microsoft OneDrive tricks that make it easy
Six clicks: Simple and time-saving Google search tricks
Mailvelope: What Google aspires to build?
Amazingly (or not), someone has already built the system that Google is planning to build, and it's not just for Chrome and Gmail.
Mailvelope is a webmail implementation of OpenPGP which uses the same OpenPGP.js library as End-To-End. It is written by Thomas Oberndorfer and is open source. Oberndorfer tells me that the idea goes back to FireGPG, a Firefox extension project, since discontinued, to implement GPG (GnuPG, for GNU Privacy Guard, another OpenPGP implementation) in the browser.
Mailvelope is available now and works with Gmail, Outlook.com, Yahoo! Mail and GMX. It is available as a Chrome extension or Firefox add-in.
Mailvelope integrates into these webmail user interfaces, but it has to be careful how it does so. It can't let the servers gain access to unencrypted data, so it launches its own UI in which the user composes and/or edits email, picks the recipients and encrypts (or merely signs) the message.
(Image Mailvelope)
First, cut some keys
Before you use any PGP system you have to generate a public/private key pair, which Mailvelope makes easy. You provide a passphrase which Mailvelope uses to control access to the private key in the Key Ring, more about which on the next page. The public key, as the name implies, needs no security, and in fact you want everyone to have it.
You can view the private key if you want, but it's not usually necessary. And if you don't know what it looks like then you can't give it up if you get captured and they torture you.
(Image ZDNet/CBS Interactive Inc.)
Key Ring
You might have several keys for various accounts of your own or want to keep the public keys of those to whom you want to send messages. When you generate keys, Mailvelope puts them in the Key Ring, or you can import the keys of others. Access to the Key Ring is controlled by a passphrase; two-factor authentication would be a really good option here.
(Image ZDNet/CBS Interactive Inc.)
Composing an email
When you want to compose an email, you can't trust the webmail interface windows because they are in the provider's domain. Mailvelope puts a button on the UI that you can use to start a Mailvelope message session in a local window, showed here.
Other buttons allow you to select the keys of recipients with which to sign the message, and to encrypt it.
(Image ZDNet/CBS Interactive Inc.)
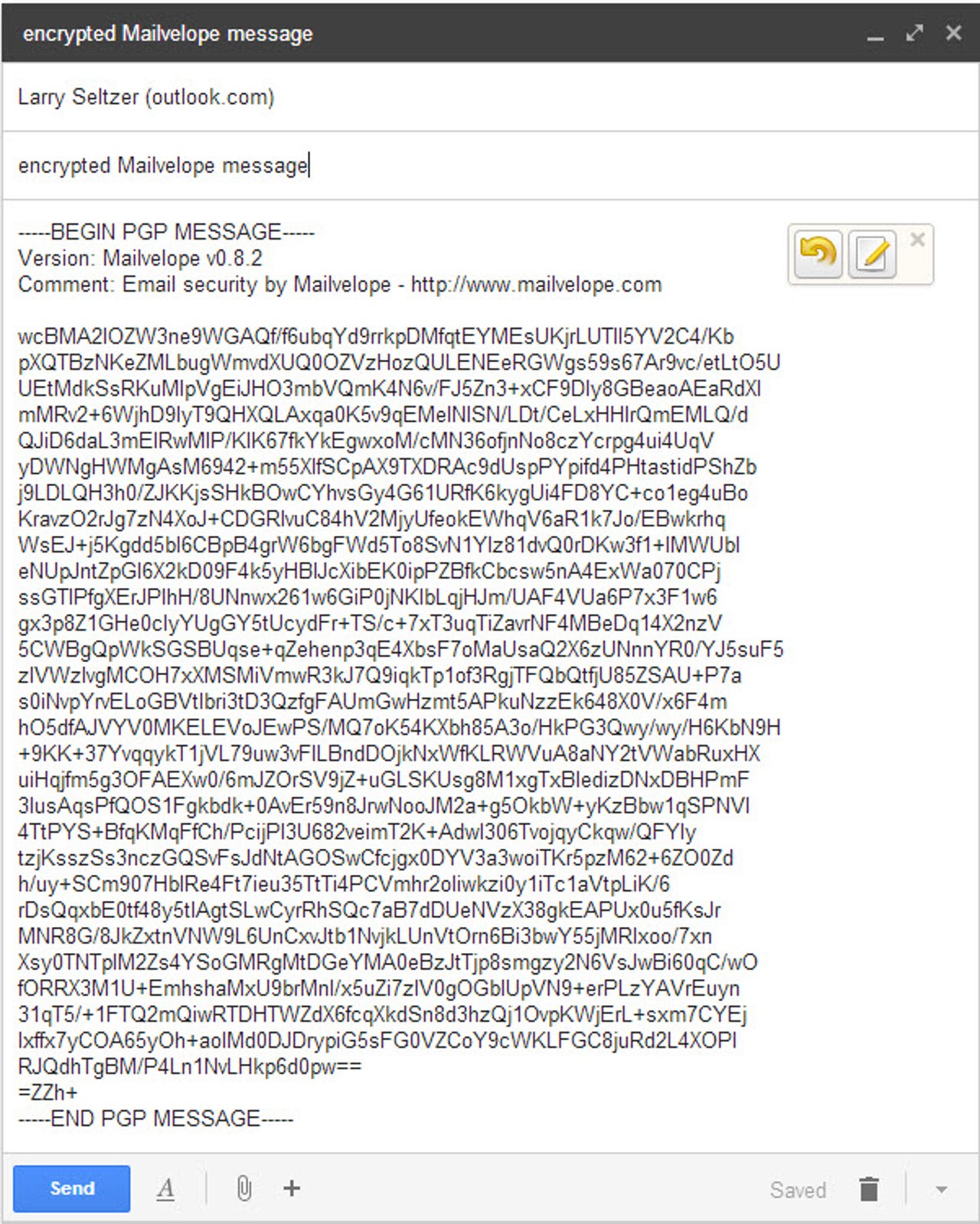
The encrypted message
After you encrypt the message in the Mailvelope window, you press a button which transfers the encrypted contents to a compose window for the webmail system. This image is a Gmail window. You enter the recipient(s) and a subject line.
Notice that the contents of the message are encrypted and none of the body is usable by someone without a key. The recipient(s) and subject line are in clear text though. It will remain like this, at the hosting provider, at any other server and on the wire, until the message is received by a user who uses PGP or Mailvelope or some other compliant program to decrypt it.
The fact that the recipients and subject are not encrypted (and, because of the way SMTP works, can't be) is a potential vulnerability for the system, if the user is not careful. An outsider can still determine who is emailing whom, what the subject lines are and anything else in mail headers.
(Image ZDNet/CBS Interactive Inc.)
Received and decrypted
Here we see the recipient, using Outlook.com, after having decrypted the Mailvelope message using a UI similar to that used on the Gmail side to encrypt it. A signature is also present, allowing the user to verify the identity of the purported sender.
Compared to ordinary email, this system is highly complex, even though it is a very simplified version of PGP. There are more polished interfaces built as plugins for Microsoft Outlook, but none of the free/open source products are near usable enough.
(Image ZDNet/CBS Interactive Inc.)