How this one innocuous tweet could hack a bank account

Meet Alex.
I knew remarkably little about him when we first met. Alex is not his real name — it's a pseudonym to protect his identity. But everything else about him is very real. He travels to our New York newsroom and our San Francisco office from his home near Charlotte, NC, where he lives with his family.
Alex is one of a growing population of "privacy ambivalent" users. He keeps his Social Security number close to his chest, and rarely gives out his personal email address unless he has to. But he isn't clued up on the latest Facebook privacy options, and doesn't particularly mind who reads his tweets.
Because Alex is — like myself — a British expat, he and I chat now and then about the differences between life in the U.K. and here in the U.S. Last month, we fell into conversation about the “backward approach” of online banking security in America.
Both of our U.S. banks require an alarmingly vague offering of details to access our bank accounts over the phone, such as our home addresses, our dates of birth, and now and then the last four digits of our Social Security numbers. In contrast, British banks rarely ask for anything less than username, password, three-digit, variable drop-down boxes of codes, memorable names, iris scans, fingerprints, the exact weight of your first born child, and the name of your dog that you always forget even though he was your "best friend" growing up in the suburban bliss of outer London.
Sharing personal anecdotes of how lax U.S. banks appear to be with our life savings compared to British banks left us both a little shaken.
He asked me: "Wouldn't it be interesting to see how much information there was on me out there? Like, what you can find out from the Internet and try to get on the phone with my bank?"
Yes, Alex. Yes, it would.
Based on just his name and his employer, would that be enough to steal his identity and take over his life?
The bet was laid and the plan we formulated was simple enough: To gather enough intelligence about Alex to convince his call center operator at his bank that I was him. Like something out of a Mission Impossible film, I would have to bypass the automated phone system, steer through the security questions, and — armed with a fictional and empathy-driven sob story — socially engineer my way into his bank account.
And then, out of nowhere and in a chilling moment of awkwardness, I forgot his surname — despite the fact we'd met before and shared a pint in the pub over the road.
I was mortified.
But, being British and all, one doesn't beat about the bush. On the verge of asking him, I stumbled over my words — I admitted I didn't know, but also didn't want to know — stopping him as he was about to mutter, "Oh, it's…"
In just half an hour, I walked back into his office and read out a five-digit number.
"That's my house number... How the f**k did you get that?"
Because the less I knew, the better.
I took him up on his offer, and we agreed a strict set of rules.
For one, I would be acting the "civilian" hacker, rather than a journalist. (Journalists often have access to paid-for accounts that would churn out public records and other data.) Because of this, I was not allowed to use CBS' internal tools to find out any information on him, or strap down and waterboard our human resources director into handing over information.
I had nothing but the Web to use as my hacker's toolbox.
In as little as half-an-hour later, I walked back into his office and announced a five-digit number that made Alex’s smile loosen and his jaw drop.
"That's my house number," he said. His face was mixed with shock, terror, and awe. "How the f**k did you get that?"
One single innocuous tweet sent more than a year ago let him down.
I sat down at my desk after our bet first began and immediately turned to Google. No matter which social network you use, Google is a better engine for finding keywords — even keywords within those social networks. I knew his first name, and I knew the company he worked for. I bashed in "Alex" and "CBS Interactive," the owner of ZDNet and CNET, and behold, his LinkedIn page (and surname) landed at the top of the list.
His LinkedIn account confirmed his full name, his position, and his employer. I found his Twitter account on his LinkedIn profile, but the other top three Google search results also churned out his handle.
Surely there were Github or browser scripts that could have scraped his entire Twitter account, which confirmed in his profile that he lived in Charlotte, NC, along with more than 1,500 tweets and the occasional uploaded photo. But instead, I took the raw viewing approach, by scrolling down to his very first tweet and began to search through the stream. It was quick and lazy, but easily searchable within my browser
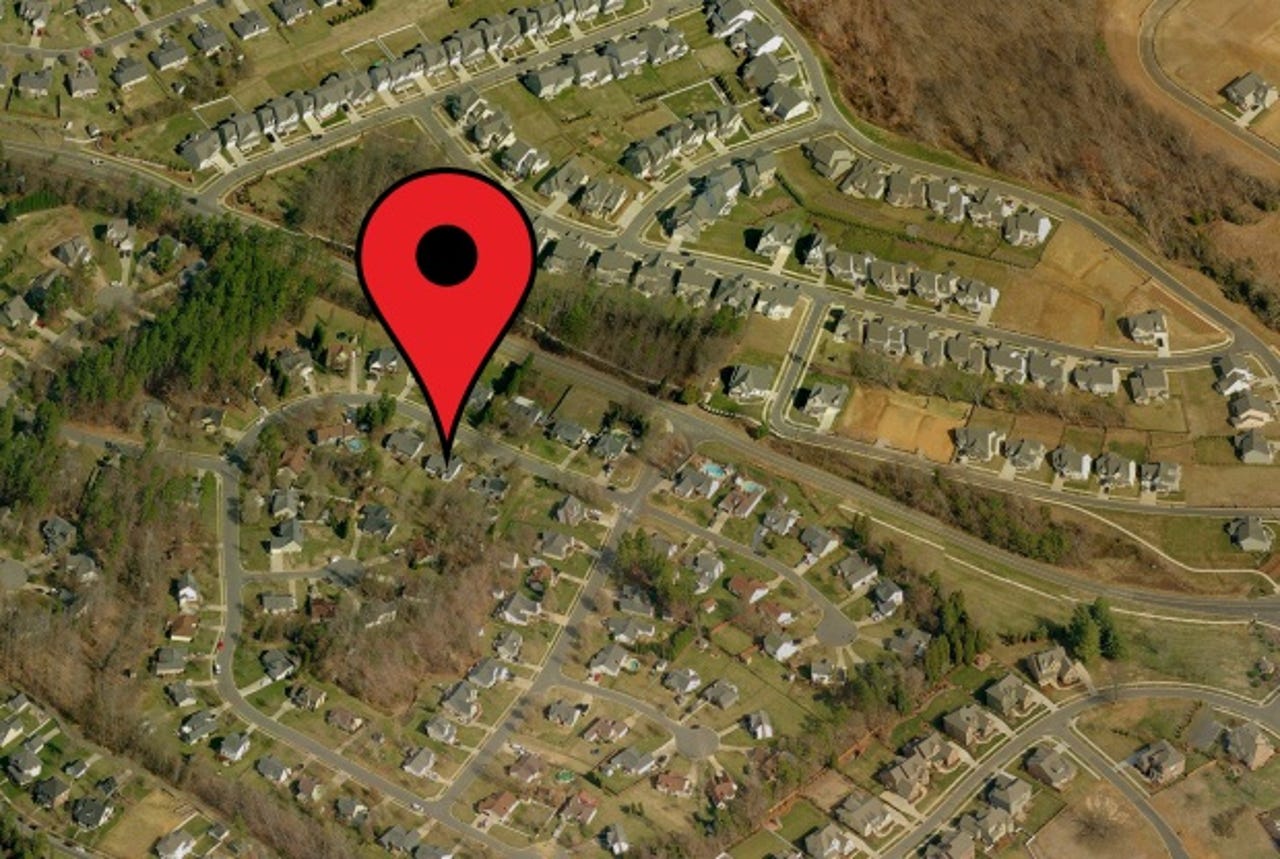
There were a few scatterings of location-based tweets. Some from New York, some from San Francisco, and a few others from places where we have offices around the world. A few search terms later, I found one single search term reference to "NC," or North Carolina. From just one tweet buried in the midst of innocuous tweets, a new tab opened and Google Maps pinpointed his suburban home address — at least, so I assumed — with ground-level Street View imagery on demand.
I was even able to tell him what color his front door was. He slumped back in his chair, clearly taken back.
But I didn't stop there. He authorized me to look further.
What I was ultimately after were possible or even specific security questions that a bank might ask for. Armed with those, I could — in theory — take over almost every aspect of his life.
Public records showed how much he paid for his home and when. This gave me the very first personal data reference, which could be a PIN code or security question that I may use later. There were also North Carolina public records, which churned out tax receipts and other information that pointed me to his wife's name, who we shall call Sarah.
The amount of information available from their mercilessly open Facebook pages was nothing short a hacker's dream. From photos, status updates, the "about" page, and other check-in and location data, I was able to determine intimate details of his family — his child's name and date-of-birth, and the anniversary of his marriage to Sarah — which I saw as the second, third, and fourth personal data references.
I was a little sickened with how much data I had collected on this man's life and family by this point. I was already bordering on what felt like the side of unethical behavior — the fact he had authorized me to keep going was the only thing that encouraged me to continue.
A few more further keyword searches yielded Alex's birthday, a date in mid-June, from a written confirmation from one of his tweets — something he likely thought nothing about at the time. I could guess his age, but it wasn't enough for a fifth data reference that could be used as a security question or code.
Facebook would once again hold the answer, or at least part of it. What came next took logic and variable plugging.
I knew his personal username from his Facebook account URL, but the hacker in me — admittedly with the restraint of a saint — could have garnered even more personal and sensitive information if I were to access his personal email account without his authorization. At least, that was the assumption I was going with.
By opening an incognito window, removing my own cookies and Facebook account from the equation, I plugged his information into the site's password reset facility.
Thrown back at me was: a*****9@g*********.com.
I tested with my own account. Facebook masks the exact number of characters from any email addresses provided. It took a smidge common sense guess to identify he had a legacy Gmail account with a @googlemail.com address. The next step in determining his email address would not be easy, and would take multiple attempts and plugging in possible variables, but Facebook's password reset facility would be enough to fill in the blanks based on at least two hours worth of guesswork.
With the first and last character — the first being the letter "A" and the latter being a number — I assumed it was his full first name, with space for the first letter of his surname, perhaps, the last two digits of his year of birth.
After about three hours, I plugged in multiple combinations, unmasked the asterisks, and on my screen was his Facebook account. And yes, as I suspected, 1979 was his birth year. I now had his full date-of-birth, which tied in with the rough timing of his academic history from his LinkedIn account.
Armed with his full personal email address, I next hit Gmail's password reset facility. Although Google's security and validation system for inaccessible email accounts is better than most email providers, Alex's own security questions let him down. Often the weakest link in the security chain is the person in question.
I was already walking on thin ice. Though I had uncovered his security question, I refrained from attempting to answer it. Suffice to say, I probably could have.
By this point, I had already discovered at least five pieces of data that could be used as a security answer or code with his bank. But in order to get access to his checking or savings account, I would almost certainly require his Social Security number. Many banks require a full bank account, or credit or debit card number. Accessing his physical cards would be nigh on impossible. When no card details are given, a Social Security number is almost always used as a fallback.
But how would I get his Social Security number? Two hours of searching some of the Web’s darker hacker forums was leading me nowhere.
Alex is a British expat, likely in the country on a visa or a green card. When he married Sarah, a U.S. citizen based on her Facebook profile, it's possible that he had obtained permanent legal residency through a marriage-acquired green card. But, that was based on assumptions. Even if he submitted a green card application at the time he was married, would he have even received it by now? I was guessing, and going down this path of thinking likely wouldn't yield any definitive answers.
I needed his Social Security number, but my options were fading fast.
Hours later, my eyes lit up. What is one of the first things you get if you relocate to a foreign country? A cell service plan.
Most cell service providers — AT&T, Verizon, and Sprint, among others — require you to present certain forms of identification, often including a Social Security number, before you can sign up.
In theory, the next challenge seemed easy enough. In reality, I would rely on sheer luck.
If I could find his cell phone number, and if he used a cell provider that required a Social Security number, I could then, in theory, acquire at least a few of those golden government digits from his cell provider through similar social engineering techniques I would reserve for his bank.
It turned out that sooner rather than later, I would have to use those very techniques directly on my target.
How exactly would I get his phone number? By asking for it — directly or indirectly — by sending him an email asking for it. Knowing his work and what he does for a living, I would need to throw out the "phishing" line by pretending to be a potential client. And for the purposes of this exercise, I would want to talk to him on the phone about it.
Though I already had his personal Gmail account, I needed to send him a note through his work email. I already had knowledge of his work's email address naming scheme, but after a few searches it was clear that it was, like many organizations, it followed the "firstname" dot "lastname" at the company's domain scheme.
In a matter of minutes, I created a full-name personal email address with Gmail, and, with knowledge of his work and expertise, carefully crafted an email that would not only get his attention, but also surely warrant a reply.
"Hi Alex. We're a B2B startup based in Mountain View, and we're looking to advertise. I'm traveling for the next couple of days, could you email me back letting me know how might be the best approach going forward?" — 'John'
I sent the email, and waited. The next day, he replied. Behold, in his email signature, was his cell phone number. I didn't need to continue the thread any further. I plugged the phone number into a popular cell provider lookup website. His cell phone provider was Verizon.
I was unthinkably close to acquiring the golden goose: at very least the final 4-digits of his U.S. government-issued identifier, or at most the full 9-digit figure.
And that's where I stopped.
I geared back into "journalism mode," and set up a call with Alex to discuss my findings. Every shred of my being wanted to fight until the bitter end and see how far I could go. The thirst for this data reached such levels that I was uncomfortable in how I was acting. There was a line in the sand though that I would not cross. I would not impersonate him without him being physically there in our New York office — a place he rarely visited.
How I would have loved to have told you how I stood in his office with his phone on speaker, with him watching over me as I read aloud his personal and sensitive data, playfully chatting with a call center operator at his bank, joking along and chuckling about how my wife had "spent a bit too much on the kids again," and wanting to review my current checking account balance.
Alas, that call I had longed to make for days never came to fruition.
We discussed my findings at length. I explained that going any further would be unethical, and possibly illegal. Enough was enough, and my point was made.
I knew more about Alex than most of our other colleagues' did. I had his home address, date of birth, the date of his wedding anniversary, and his child's date of birth — all of which may have served as security answers to his various real-world accounts. I also had his personal and work email address, his cell phone number, his employment status and history, and even a good guess at his immigration status.
We agreed that this was a good time to stop.
The information I had would have, as it turns out, been enough to socially engineer my way through to the Verizon customer call center. Whether or not the operator would have divulged his Social Security number to someone they thought was in fact him, we will never know. But if that were the case, there would have been a strong possibility that I could have, with that 9-digit number, accessed his bank account.
But all that from a workplace wager and a single, innocuous tweet? It wasn't bad for just shy of two days of work.
Featured
Because the information I collected on Alex was so sensitive, it was inputted and stored on a locked-down computer. It was disconnected from the network and required a complex alphanumeric password to unlock it. That data was encrypted in a document that was also protected with a different, strong alphanumeric password. The information was subsequently obliterated with an erase tool once it was no longer needed.
Alex is not a chief executive, a rock star or a celebrity, or a government employee with access to state secrets. This was an authorized "vendetta." This was personal. I wanted to break into his life and crack it open to see what I could find. It's atypical from a black hat hacker who might scrape out personal information from a hack or data breach in order to siphon off money.
In that respect, it wasn't the average intelligence gathering exercise.
But it threw him off his privacy pedestal. And the results certainly put chills up and down my spine.