460,000 Turkish card details put up for sale, web skimmers suspected

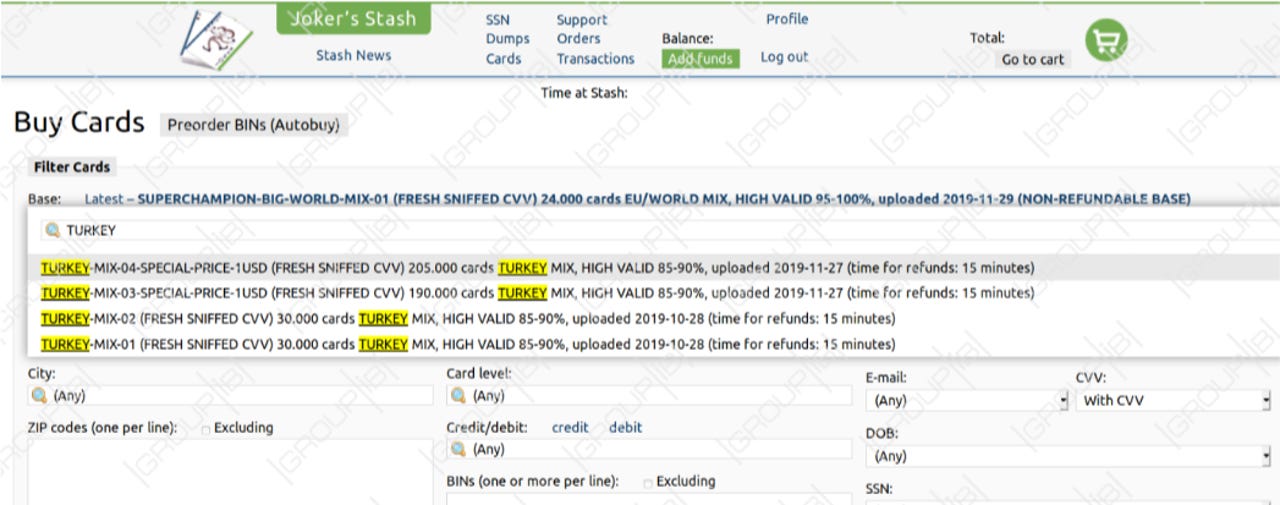
Details for 463,378 Turkish payment cards are currently being sold online, ZDNet has learned today.
The card dump was put up for sale on Joker's Stash, the internet's largest carding shop, security researchers at Group-IB told ZDNet.
The data, published in four batches between October 28 and November 27, represents the largest sale of Turkey-based payment card details in recent years.
"Cards from Turkey are very rare on cardshops," Group-IB told ZDNet. "In the past 12 months, this is the only big sale of payment cards related to Turkish banks."
Group-IB, who tracks the underground market for stolen credit cards, says the four batches (30K + 30K + 190K + 205K) are estimated to net hackers more than $500,000, when sold.
Source unknown, but JS skimmers are suspect #1
According to Group-IB, the card dump included both debit and credit cards, and the cards originated from a broad spectrum of Turkish banks.
The wide variety of card types and issuing banks suggests the data came from a source that handles payments, rather than a single bank's hacked system.
"All the compromised credit and debit cards records in this database were identified as raw cards data also known as 'CCs' or 'fullz' and contained the following information: expiration date, CVV/CVC, cardholder name as well as some additional info such as email, name and phone number," said Dmitry Shestakov, Head of Group-IB's сybercrime research unit.
The presence of emails and phone numbers automatically excludes that this information was obtained from skimming devices installed on ATMs or PoS devices.
Shestakov believes the data could have come from sources like: (1) users who were fooled into entering card details into phishing pages, (2) malware that harvested this data from browsers, or (3) JavaScript-based skimmers that stole the data as the user was entering it on a hacked online store.
The third option is most likely the answer. Ever since Magecart attacks (JS skimmers) have become widely popular, they've breathed new life into the carding scene. However, Shestakov told ZDNet that they can't yet "tell if JS-sniffers were involved or not."
"The source of this compromise remains unknown," he said.
"As per the JS-sniffers in general, we've indeed seen some JS-sniffers families (not related to this breach), whose operators sell stolen cards on underground shops," Shestakov told ZDNet.
"One example would be the G-Analytics Family described in detail here," he added. "The operators of this family are connected to a cardshop named 'Cardsurfs' ([REDACTED_URL]) which likely sells payment cards stolen by JS-sniffers."
Authorities notified
This is the second major card dump Group-IB has spotted this year. In October, the company spotted crooks putting up for sale a batch of 1.3 million Indian cards. The company said this was the largest card dump that's been ever recorded being put up for sale on Joker's Stash.
The Turkish batches got lost in the huge Indian card dump.
However, Shestakov said that once they learned of the card dumps they notified relevant Turkish local authorities so they can take appropriate measures.