Bad, bad, cybercrime-friendly ISPs!
From Starline Web Services, to ZlKon, Internet Path/Cernel, HostFresh and UralNet, the series draw a simple conclusion - that a dysfunctional abuse departments can indeed act as driving factor for the growth of cybercrime.
The main objective of a dysfunctional abuse department is to on purposely delay the review and take down process of a domain/customer in question, thereby increasing the average time for the campaign to remain online. Which is exactly what most of these ISPs are involved into, while charging premium prices in the process of ignoring community requests for shutting down a malicious campaign in question.
Interestingly, what we're witnessing for the time being is a mixed abuse of, both, legitimate infrastructure and purely malicious one. For instance, the bad actors that FireEye is profiling, will receive traffic coming from abused legitimate infrastructure such as the Digg, Google Video and YouTube's latest malware campaigns. Moreover, we cannot talk about cybercrime-friendly ISPs without mentioning the domain registrars of choice for the majority of cybercriminals, which KnujOn keeps profiling. Their February, 2009 Registrar Report states that 10 registrats are responsible for 83% of the fraudulent sites that they've analyzed, with the Chinese registrar XIN NET topping the chart for a second time.
With new cybercrime-friendly ISPs popping up on the radar, consider keeping an eye on the upcoming additions to the bad actors series.
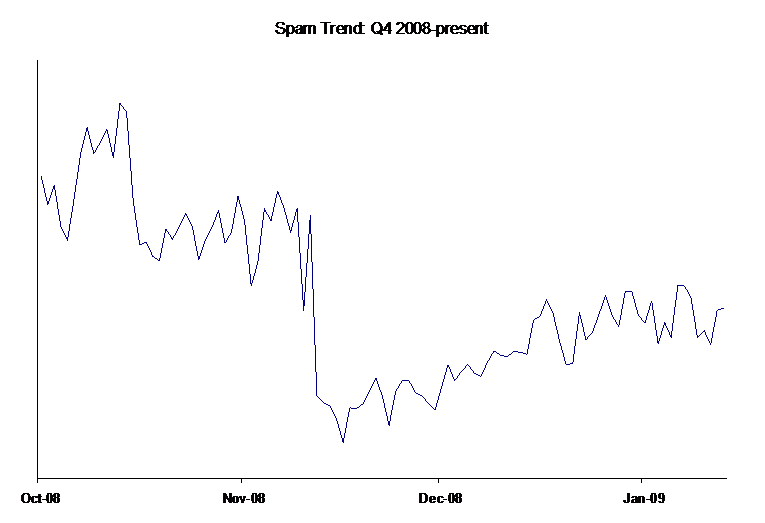
Image courtesy of Google's Postini 2008 Spam Report in a post-McColo Internet.