Bitdefender reveals Mandrake spyware targeting Aussie Android users

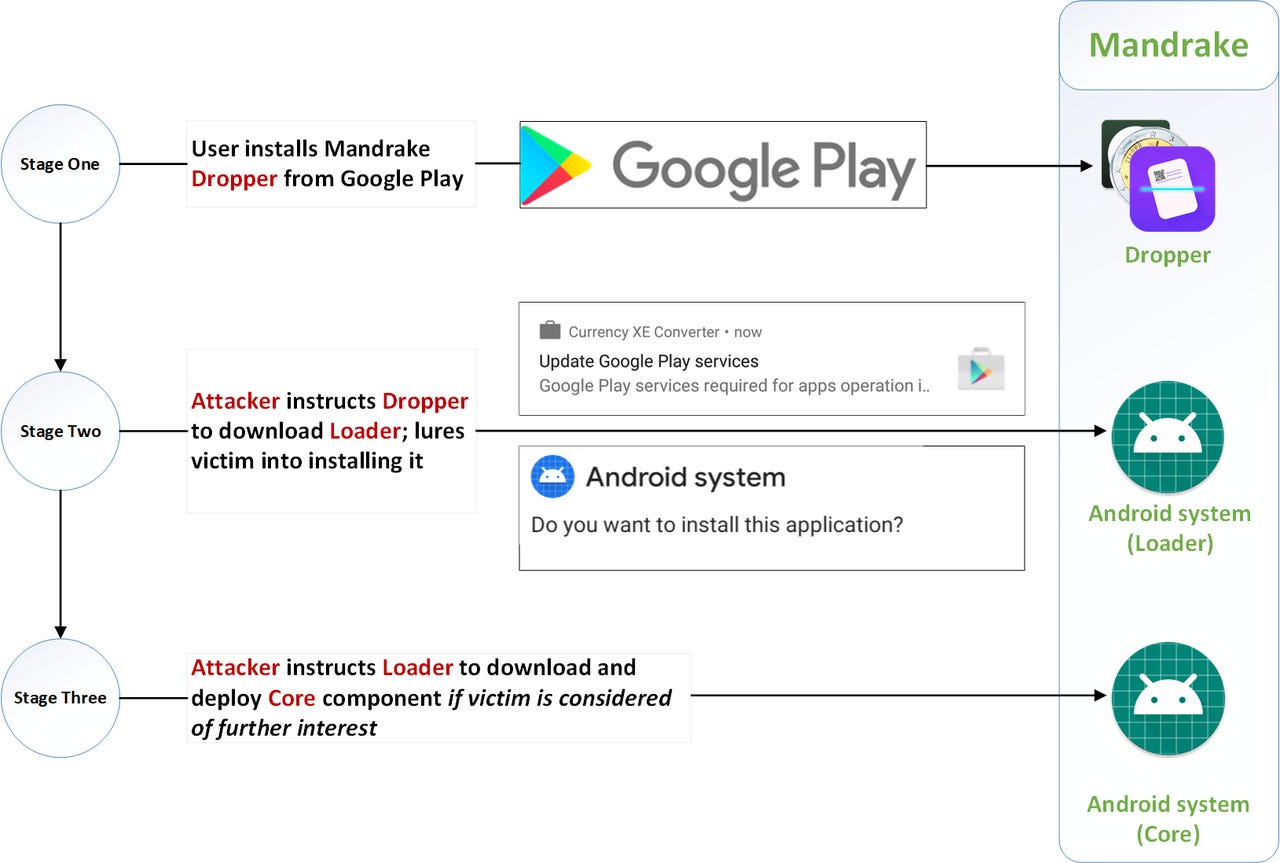
Mandrake stages
The Bitdefender cybersecurity investigative team has uncovered a new Android spying operation specifically targeting Australian users.
The company found "Mandrake" earlier this year and believe the highly sophisticated spying platform has been active for at least four years.
Bitdefender said it has seen a rapid spread of attacks in Australia over the last two years, due in large part to Australia's high mobile banking usage, which sees the country targeted by more banking trojans than any other developed country in the world.
To date, the team has recorded Mandrake subverting Google Chrome, Gmail, ANZ Australia, Commonwealth Bank of Australia, Bank of Melbourne Mobile Banking, Bank of SA, Australian Super, and PayPal apps.
Lead investigator Marius Tivadar told ZDNet, from analysing data captured over a two-month period, the team identified 500 unique victims from Australia who had one or multiple devices compromised. He warned that the number could be much higher.
According to Bitdefender, the criminals are using the software to attack on an individual basis. Mandrake is well developed, with a constant evolution over the four-year timeline of adding new features and solving bugs or dropping functionalities.
"They are human conducted and not automated," Tivadar explained.
"Weaponisation will take place after a period of complete spying of the device and victim. The attacker has access to things like preferences, screen recording, device usage, and inactivity times."
It can even turn down the volume of the phone and block calls or messages.
"Next to this the attacker could do anything from credential stealing, information exfiltration to money transfers, and blackmailing," he added.
The first discovered sample dates back to 31 January 2016.
Tivadar said its authors seem to be interested only in some "special kind of consumers", those who have something they can benefit from.
"We saw the attacks are manually orchestrated, this is highly unusual as it seems every victim is analysed independently and an attacker issues commands tailored for him," Tivadar explained. "This also tells us that this cannot be the work of a lone wolf. It would also be possible for them to run some affiliate program, 'selling' victims to others."
The first attack wave in 2016-2017 had an affinity for the UK, US, Germany, and the Netherlands. The current 2018-2020 attack wave is more spread in Australia but is also present in the US, Canada, and Europe.
"Subverted applications and services seem to be more in number in Australia. We do not know a real reason for this," he said.
"Australia seems to have a very high mobile banking penetration also having a high GDP per capita, might explain why looks so appealing."
The most dangerous iOS, Android malware and smartphone vulnerabilities of 2019
SEE ALSO
- The ultimate guide to finding and killing spyware and stalkerware on your smartphone
- This Android malware can take photos and videos and spy on your app history
- Over 58,000 Android users had stalkerware installed on their phones last year
- This new Android ransomware infects you through SMS messages
- This huge Android trojan malware campaign was discovered after the gang behind it made basic security mistakes