Click-fraud ZeroAccess botnet rises from the ashes

The ZeroAccess botnet, disrupted by Microsoft in 2013, has risen up once more to commit click-fraud and data theft.
Originally discovered in 2013, the ZeroAccess botnet -- also known as Sirefef -- targeted major search engines and browsers, commandeering search results and routes queries to websites rigged to infect computers with malware, steal information or to generate revenue from fake online ad clicks.
ZeroAccess gathers machines when users visit compromised websites and unwittingly download malware. In turn, this malicious code rigs the computer up to the botnet, becoming another slave machine the botnet operator can control.
Microsoft, together with Europol's European cybercrime centre, the FBI, and tech industry figures disrupted the botnet system in 2013, which the Redmond giant estimated cost advertisers $2.7 million monthly.
However, after six months of relative inactivity, the botnet is once again operating. According to Dell SecureWorks researchers, the peer-to-peer botnet began to resurface from March 21, 2014 until July 2, 2014, and on January 15 2015, click-fraud templates are now once again being distributed to compromised systems.
There does not appear to be any new slave elements or compromised systems in the network beyond its disruption in 2013. Instead, ZeroAccess is composed of "residual hosts from past compromises, so it is much smaller than it has been in the past," the researchers say.
While this in itself is good news, how long this will remain the case remains up for speculation.
The ZeroAccess network has segmented into two distinct botnets which operate over UDP ports, Dell SecureWorks says. One port is used by compromised Windows systems running on a 32-bit architecture, while the other is used by PCs on 64-bit architecture.
Every compromised computer within the P2P network acts as a singular node, and over time receives click-fraud templates which include URLs for attacker-controlled template servers. As systems visit these URLs, the malware begins a system of redirects which leads to a Traffic Direction System (TDS) that sends the bot to its final destination.
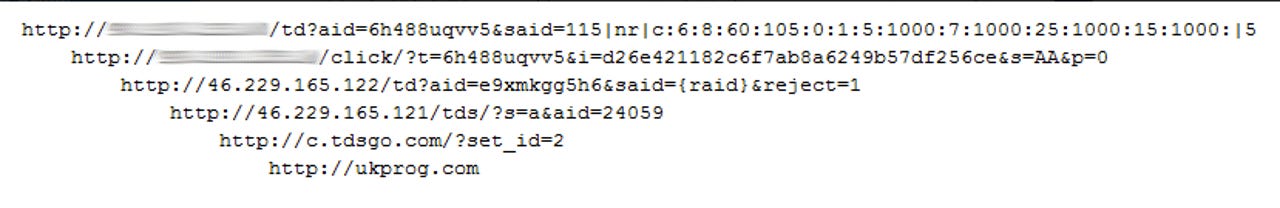
Between January 17 and January 25, 2015, the researchers tracked 55,208 unique IP addresses participating in the botnet.
Most hosts are found in Japan, India and Russia. However, there are also nodes in Italy, the US, Brazil, Taiwan, Romania, Venezuela and Germany.
While the operators behind ZeroAccess have not made any significant attempts to refine the botnet over the past year, its resilience "is a testament to the tenacity of its operators and highlights the danger of malware using P2P networks," the team says.
ZeroAccess is a significant problem, but is not the threat that many other botnets pose to the general public -- those focused on banking fraud and identity theft. Instead, ZeroAccess focuses on striking advertisers through click-fraud and generating income through illegal means.
Read on: In the world of security
- Most US businesses vulnerable to insider threats
- Over 90 percent of data breaches in first half of 2014 were preventable
- Bluster, bravado and breaches: Today's 'terrorist' players in cybersecurity
- Mobile malware on the rise worldwide, ransomware hits the spotlight
- Verizon rushes fix for email account open season security flaw
- Microsoft Outlook hacked following Gmail block in China
- High volume DDoS attacks rise in Q3 2014
- Hackers for hire: Anonymous, quick, and not necessarily illegal
- UK hires hackers, convicts to defend corporate networks
- ZeuS variant strikes 150 banks worldwide
Read on: Fixes and Flaws