DMARC's abysmal adoption explains why email spoofing is still a thing

techrepublic cheat sheet
Companies around the world are still failing to see the benefits of implementing DMARC, an email security protocol designed to prevent email spoofing, the primary trick used by cybercriminals to deliver phishing emails and BEC scams.
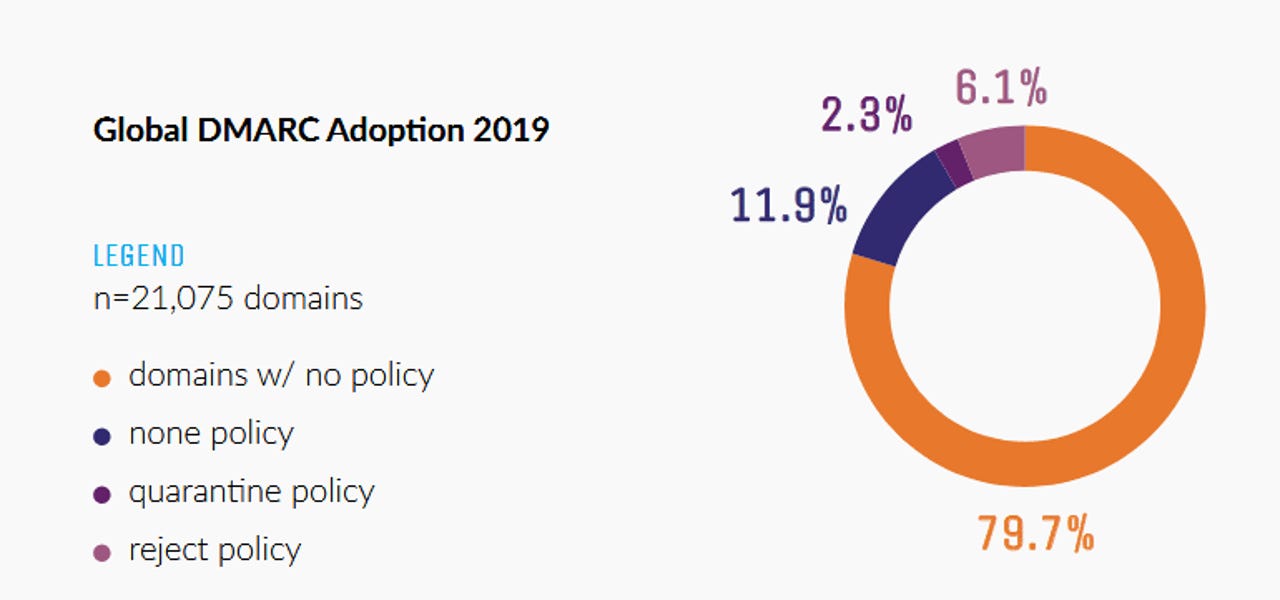
Around 79.7% don't use DMARC, according to a report that surveyed the DMARC policies deployed with 21,075 business and government domains.
The survey, carried out by email security and analytics firm 250ok, analyzed domains from sectors such as Fortune 500, US government (Executive, Legislative and Judicial), the China Hot 100, the top 100 law firms, international nonprofits, the SaaS 1000, education, e-commerce, financial services, and travel sectors.
The survey looked specifically at DMARC adoption because of the protocol's importance.
What is DMARC?
DMARC, or Domain-based Message Authentication, Reporting & Conformance, is a protocol that works on top of email servers that already support the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM).
DMARC lets email server administrators put policies in place that can detect when an incoming email is lying about its real "From:" address.
It's the best mechanism companies have at their disposal today for detecting spoofed emails that claim to come from an employee or a contractor, but come in reality from a threat actor just trying to pose as a legitimate sender.
DMARC adoption still very low
However, companies are not taking advantage of the protocol, despite the fact that DMARC has been around for years.
This means that most companies are still vulnerable to business email compromise (BEC) attacks, phishing emails, and other types of email scams, as hackers can easily make their emails look authentic and pass their scams as legitimate communications.
The good news is that DMARC adoption rate is better than previous years. However, the bad news is that the needle is moving too slowly to make a difference.
An FTC report from 2017 found that only 10% of 569 businesses with a significant online presences had deployed DMARC policies with their domains.
A November 2018 Agari report found that half of the Fortune 500 companies were supporting DMARC, but that only 13% of companies had actually bothered to set up DMARC rejection policies -- meaning the DMARC protocol was installed, but wasn't actually used to stop spam, phishing, and scams from spoofed domains.
A quarter later, in February 2019, the same Agari reported that the percentage of Fortune 500 companies actively using DMARC policies had gone up to 15%. A small increase, but still insufficient, since this still left hundreds of the world's biggest companies open to attacks.
DMARC adoption in China lagging behind
The 250ok survey published earlier this month found that the number of Fortune 500 companies using DMARC policies had moved again, and is now at 23% -- but still very low.
According to 250ok experts, the SaaS 1000 sector had the best adoption, with 46% of companies using DMARC.
Another domain that had a good adoption of DMARC policies was the US government sector, but not all of it.
In the US, the DHS issued Binding Operational Directive (BOD) 18-01 in October 2017, a document that instructed US federal agencies to implement a series of web and email security protocols, including DMARC.
According to 250ok, the executive branch of the US government appears to have taken the BOD seriously, because 81.5% of .gov domains were using a DMARC policy to stop spoofed emails.
But on the other hand, the legislative and judiciary branches were seriosuly lagging in terms of DMARC adoption, with only 17.3% and 13.0% of their domains using DMARC policies to stop spoofed emails, and leaving government employees open to attack.
But outside SaaS companies and some .gov domains, DMARC is not widely adopted anywhere else. Further, the lowest adoption rate found by 250ok researchers was in China, where only 6.5% of surveyed companies were using DMARC policies to protect against spoofed emails.
"This is likely the result of China's reliance on social platforms and SMS rather than email," said Matthew Vernhout, Director of Privacy at 250ok.
"Quartz.com reported while China's residents tend to have email addresses, they prefer communication over one of their local social channels such as WeChat or SMS. This would also support the idea that email is simply not a priority for businesses or consumers in the region, and better illuminates the general lack of adoption of email authentication."
Tangible benefits abound
While implementing DMARC might be difficult because this also implies supporting SPF and DKIM as well, the benefits are tangible for companies that do.
According to the FBI, US companies reported losses of nearly $1.3 billion in 2018 due to BEC scams, the most popular form of cybercrime last year.
On the other hand, an October 2018 report from the Global Cyber Alliance estimated that DMARC usage helped companies avoid losses from BEC scams ranging from $19 million to $66 million during 2018.
So, while DMARC might be hard to implement, once it's enabled, it can help companies protect themselves against one of today's most prevalent forms of cybercrime.
DMARC may not be an answer to all forms of cybercrime, but it can greatly limit hackers' bags of tricks by taking "email spoofing" out of the equation.
Data leaks: The most common sources
Related cybersecurity coverage:
- US company selling weaponized BlueKeep exploit
- Google bans DarkMatter certificates from Chrome and Android
- No More Ransom project has prevented ransomware profits of at least $108 million
- APT-doxing group exposes APT17 as Jinan bureau of China's Security Ministry
- Kazakhstan's HTTPS interception efforts target Facebook, Google, Twitter, others
- NSA to establish a defense-minded division named the Cybersecurity Directorate
- iOS developers still failing to build end-to-end encryption into apps TechRepublic
- The best identity theft monitoring services for 2019 CNET