Do we need another CERT?

Google's backing of oCERT is a major milestone in the history of open source.
It's not that I have anything against the Computer Emergency Response TeamCERT at Carnegie-Mellon. They do important work, not only in identifying risks but in educating people on them.
UPDATE: A CERT spokesman notes they've licensed the term, dropped the longer form of the name (like IBM did back in the day) and licensed it to oCERT.
What makes oCERT important is here, in the famous 2000 essay by Bruce Schneier on the "window of vulnerability."
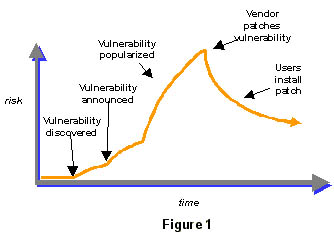
As Schneier noted, vulnerabilities, like fame, have five distinct phases.* A vulnerability is discovered, announced, becomes popular, gets patched, and then the patch is disseminated.
It's the last bit where the differences lie in open source. Windows machines are patched centrally, and that patch is distributed widely, quickly, sometimes forcefully.
Whether you get your patches directly from Microsoft or from a security vendor, the process is the same.
We have a well-established protocol for distributing fixes, so that curve downward, from distribution of a patch to fixing it, is sharp. It's like herding cows.
While open source doesn't suffer as many vulnerabilities, its dispersed nature makes fixing them more like herding cats than cows.
A central system like oCERT is needed so that, as open source gains market share, and malware writers target Linux, we can keep that last curve sharp.
* The five stages of fame. Who's Dana? Get me Dana! Get me someone like Dana! Get me a young Dana! Who's Dana? Insert your name for mine.