Don't panic: The Internet is not collapsing, despite a spike in global 'attack' traffic

The Internet isn't about to collapse or crumble, despite two long threads on popular technology site Hacker News and news-sharing site Reddit suggesting (in some cases) that it might.
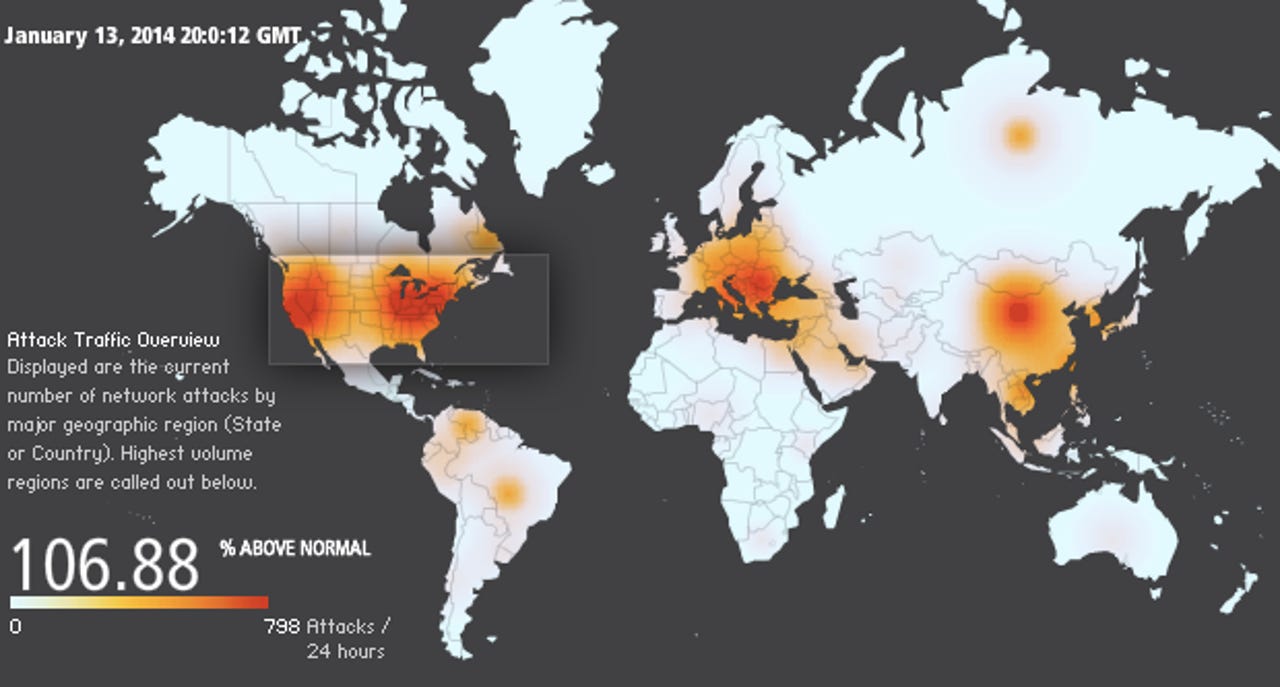
Pointing to Akamai's Real-time Web Monitor, which tracks "global Internet conditions around the clock," many drew concern from the meter showing that attacks were — at the time — up as much as 98 percent.
At the time of writing, the meter showed attacks were up by close to 107 percent above normal.
Across the U.S., which saw some of the brightest colors in the attack vector heatmap, New York saw 36 attacks in a 24-hour period, while Illinois had 40 attacks, and Idaho had 137 attacks. California, home to Silicon Valley technology giants, saw a massive 497 attacks in the day-long period.
Some speculated it was due to the recent one-year anniversary of hacker Aaron Swartz's death, reported by ZDNet's Violet Blue. One commenter on Hacker News said:
Likely an accumulation of attacks in commemoration of the anniversary of Aaron Swartz's death, as have been going on the last few days.
While Reddit users took to a giant thread under the name "Internet's Going Down, Abandon Ship!" Except, it wasn't. Further speculation on the thread pointed to AT&T, Google, a bevy of DNS servers, the Internet backbone, or even Syria.
In fact, Akamai, which provides the Internet attack heatmap, tweeted that Syria saw a massive country-wide outage that lasted more than an hour on Monday.
Likely neither we to blame for the near-blind panic and speculation.
Akamai's Robert Morton explained on the phone to ZDNet said that it was "not a massive distributed denial of-service (DDoS) attack against anyone."
The apparent spike in attack traffic is more of a reflection of what the tool is designed for.
On its description page, it says:
"We collect data on the number of connections that are attempted, the source IP address, the destination IP address and the source and destination ports in real time. The packets captured are generally from automated scanning trojans and worms looking to infect new computers scanning randomly generated IP addresses. The attack traffic depicts the total number of attacks over the last twenty-four hours."
The malicious packets are "generally" from automated scanning malware — not too dissimilar to a burglar with a key trying on each door in a neighborhood to break into someone's home. Eventually, statistically, the thief will break in.
Featured
"The visualization took is a look at what we call the darknet — where the information comes from our unnamed, unadvertised 'honeypot' servers," he said. "We count any hit or look at our servers as 'malicious traffic'."
"Anyone looking for those servers would be considered a malicious attack," he added.
Akamai also confirmed that it's not unusual to see large fluctuations above or below the normal amount — such as Monday — when the real-time monitor's meter was registering almost 800 attacks per hour.
While many consider the Akamai monitor to be DDoS traffic, the tool in fact registers "malicious" traffic, which boiled down is an attempt to connect to one of Akamai's hidden set of Internet-connected servers.
In speaking to the company's security contacts, he suggested it could be that someone is testing out a new scanning tool, or simply looking for vulnerable servers. "While you may see a large percentage spike in traffic, it's actually a small sample set than the overall platform."
Bluntly putting it: "The Internet is not collapsing around itself," Morton said.
Well that settles it. Back to sharing kitten pictures and animated GIFs, then.