Duqu Trojan programming language identified

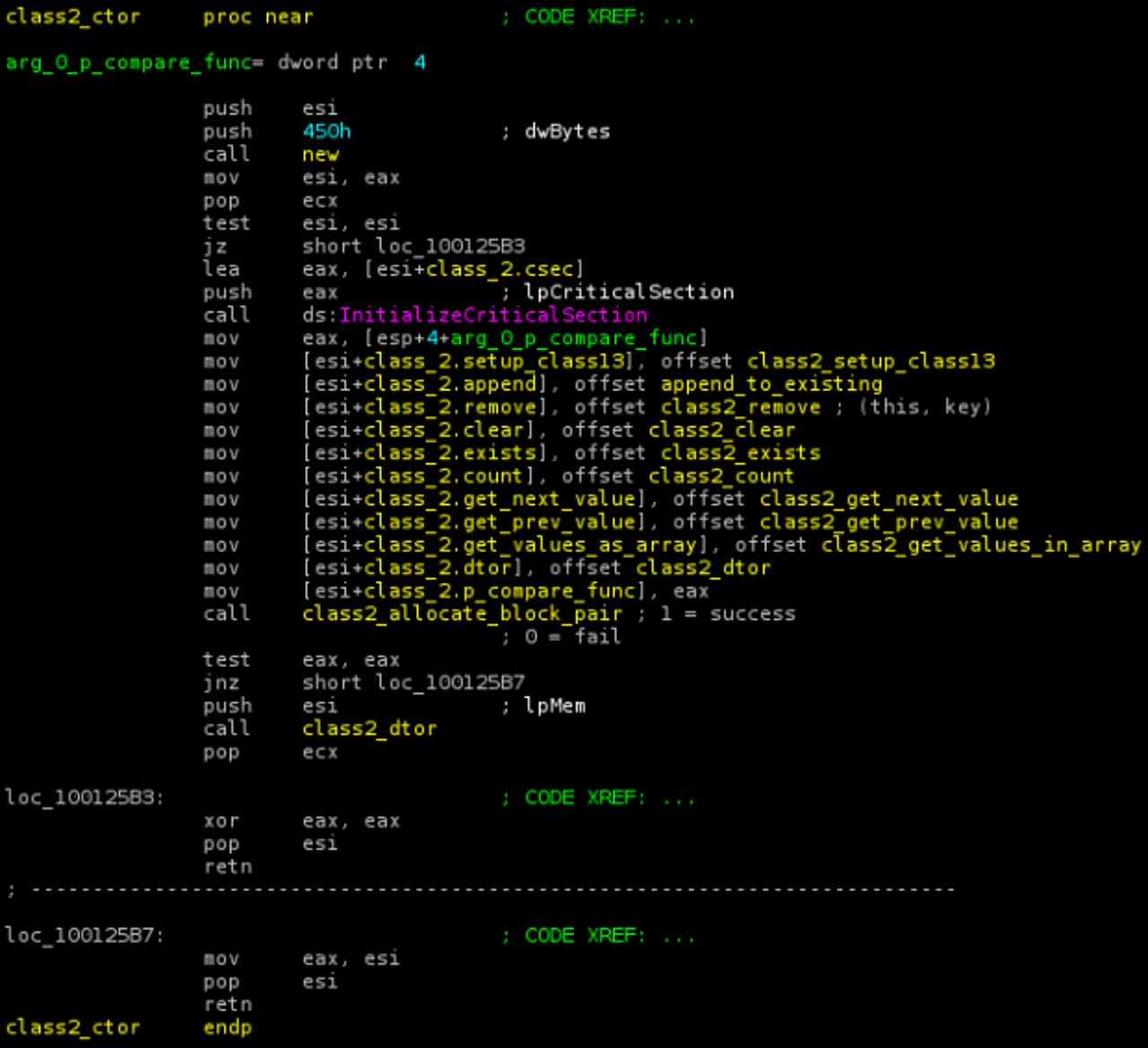
The sections responsible for downloading and executing additional modules in the Duqu Trojan, referred to by some as Stuxnet 2.0, were written in standard C++. A big chunk of it, the payload DLL, which communicates exclusively with the Command and Control (C&C) server so that the worm knows what to do once it has infected a system, has object-oriented code that doesn't resemble anything seen before. Security researchers worked out what the mystery code does, but because they weren't sure about the syntax, they asked the community for help in identifying the programming language. Over a week later, it turns out the Duqu Framework was written in C code, which was then compiled with MSVC 2008 and options /O1 (minimize size) /Ob1 (expand only __inline).
Kaspersky confirmed the finding by writing C code that, when compiled as described, produces the opcodes identical with the ones in the Duqu binary (an excerpt is pictured above). Changing the order of operations and if/else blocks modifies the resulting code; MSVC 2005 compiler produces slightly different code, too. The firm thus concludes that the resulting binary was compiled with MSVC 2008, with options /O1 /Ob1, and that the input source code was pure C.
This means the code was either written using a custom OO C framework, based on macros or custom preprocessor directives (this is the most common way to combine object-oriented programming with C), or the code was written in OO C manually, without any extensions to the language (technically, it is near impossible to distinguish code written with macro directives from manually copy-pasted code).
Here is what Kaspersky's analysis concluded earlier this month:
- The Duqu Framework appears to have been written in an unknown programming language.
- Unlike the rest of the Duqu body, it's not C++ and it's not compiled with Microsoft's Visual C++ 2008.
- The highly event driven architecture points to code which was designed to be used in pretty much any kind of conditions, including asynchronous commutations.
- Given the size of the Duqu project, it is possible that another team was responsible for the framework than the team which created the drivers and wrote the system infection and exploits.
- The mysterious programming language is definitively NOT C++, Objective C, Java, Python, Ada, Lua and many other languages we have checked.
- Compared to Stuxnet (entirely written in MSVC++), this is one of the defining particularities of the Duqu framework.
Here is what Kaspersky's analysis now concludes:
- The Duqu Framework consists of "C" code compiled with MSVC 2008 using the special options "/O1" and "/Ob1"
- The code was most likely written with a custom extension to C, generally called "OO C"
- The event-driven architecture was developed as a part of the Duqu Framework or its OO C extension
- The C&C code could have been reused from an already existing software project and integrated into the Duqu Trojan
"All the conclusions above indicate a rather professional team of developers, which appear to be reusing older code written by top 'old school' developers," writes Kaspersky Lab Expert Igor Soumenkov. "Such techniques are normally seen in professional software and almost never in today’s malware. Once again, these indicate that Duqu, just like Stuxnet, is a 'one of a kind' piece of malware which stands out like a gem from the large mass of 'dumb' malicious program we normally see."
The Duqu Framework may have been created by a different programming team, since it is unique to Duqu, unlike many parts of Duqu that seem to be directly borrowed from Stuxnet. The sophistication of the worm points to some seriously deep pockets backing the project. Security experts have suggested that a state must have been involved in its development.
Duqu was first detected in September 2011, but Kaspersky Lab believes it has seen the first pieces of Duqu-related malware dating back to August 2007. The Russian security firm also notes Duqu, like Stuxnet before it, is highly targeted and related to Iran's nuclear program.
See also:
- Kaspersky: Duqu Trojan uses 'unknown programming language'
- Stuxnet 2.0? Researchers find new 'cyber-surveillance' malware threat
- Hungarian Lab found Stuxnet-like Duqu malware
- Windows kernel 'zero-day' found in Duqu attack
- Microsoft issues temporary 'fix-it' for Duqu zero-day
- Open-source Duqu detector toolkit released