FireEye warns about the proliferation of ready-made ICS hacking tools

FireEye security researchers warn that the proliferation of hacking tools with capabilities for targeting industrial control systems (ICS) is lowering the entry bar for attackers and increasing risks for organizations operating in the industrial sector.
In a study published today, the US cybersecurity firm said it analyzed all the hacking tools with ICS targeting capabilities that were released in recent years.
"While some of the tools included in our list were created as early as 2004, most of the development has taken place during the last 10 years," FireEye said today.
Most of the tools were vendor agnostic, the company said, having the ability to scan for generic indicators usually found on all ICS networks.
However, FireEye said it also found tools that were developed to target specific ICS vendors, suggesting they were explicitly created to hack into a particular system.
Here, per FireEye, the most targeted ICS vendor was Siemens, with 60% of the vendor-specific tools targeting its products.
Most tools focus on network discovery and exploitation
But FireEye also noted that hacking tools targeting ICS networks and devices were also very diverse. Researchers found tools for a wide variety of purposes.
For example, researchers found tools for scanning networks for ICS-specific devices, tools for exploiting vulnerabilities in ICS equipment, tools for interacting with mesh radio networks usually employed for inter-connecting ICS devices, and various others [see image below].
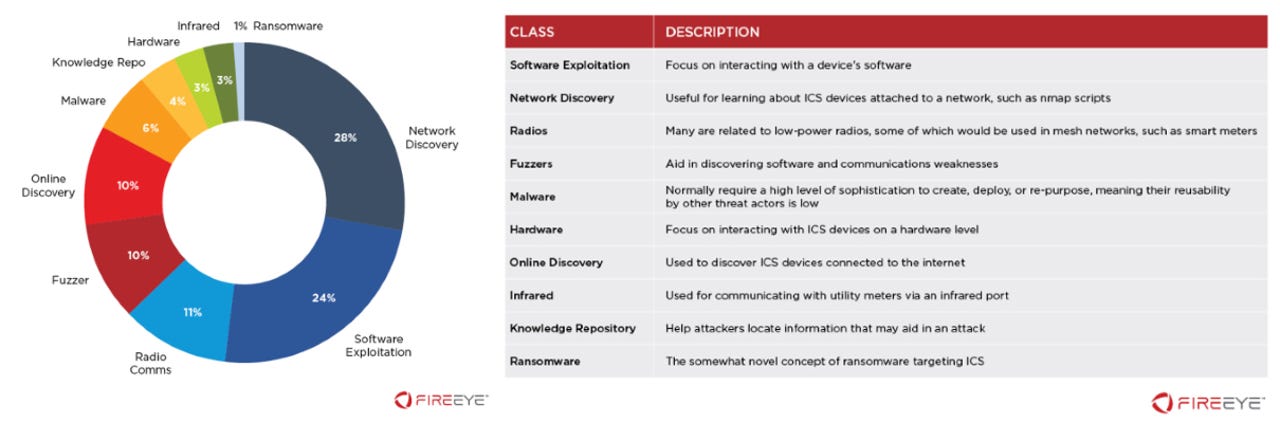
Classes of ICS-specific intrusion and attack tools
This wide spectrum of tools means threat actors can build a complete offensive arsenal by relying on publicly available tooling rather than build everything from scratch themselves.
However, this not only lowers the bar and effort that advanced (state-sponsored) actors need to put into assembling an offensive arsenal, but it also lowers the bar for low-skilled threat actors as well.
Threat actors who don't have any technical knowledge about how an industrial equipment works can orchestrate attacks against ICS targets with the push of a few buttons.
For organizations, the proliferation of these ICS hacking tools among threat actors means that instead of having to protect against a small set of hacking groups with a limited arsenal, they now have to protect against every type of hacker and all the tools currently available on the market.
Immunity has the most ICS modules but beware of Metasploit
According to FireEye, most of the ICS hacking tools they've tracked for this study were modules for three of today's most popular penetration testing frameworks -- namely Metasploit, Core Impact, and Immunity Canvas.
These are free (Metasploit) and commercial (Core Impact, Immunity Canvas) tools that security firms and security researchers use when assessing the security of a company that contracted their services.
However, attackers also love and regularly use these tools as well.
While the three pen-testing frameworks were designed for generic targets, they can also be used to test the security of industrial networks via ICS-specific exploitation modules.
FireEye said it currently tracks ICS-specific modules for these three frameworks that are linked back to more than 500 vulnerabilities.
While Immunity Canvas has the most ICS-specific modules of all the three pen-testing frameworks, FireEye warns that companies should pay very close attention to Metasploit. The reason is that Metasploit is an open-source project, and this makes it more accessible to threat actors than the other two, usually locked down behind licenses and vetting processes.
Furthermore, the ICS hacking modules for these three frameworks are also more evenly spread out among vendors, with exploits available for almost all the big names.
Vendors with 10 exploit modules or more
In addition, FireEye says that since 2017, users of the open-source community have also worked on developing an ICS-specific penetration testing framework, which focus primarily on the type of networks and vulnerabilities found in ICS environments only.
Some of the most notable ICS-specific pen-testing frameworks include Autosploit, Industrial Exploitation Framework (ICSSPLOIT), and the Industrial Security Exploitation Framework.
Going forward, FireEye warns that companies should be aware of the presence of these tools and their advanced features, and adapt risk indicators for their threat landscapes accordingly.
Security teams at companies running industrial equipment should use these tools to evaluate and secure their systems, but they should also have defensive measures in place to counter their use in the hands of an attacker.