Google blasts Web bots: PC big culprit in drive by downloads

Provos chaired a Google sponsored research forum on Botnets last month in conjunction with the Advanced Computing Systems Association.
Provos himself is leading Google research on the “ghost in the browser.” In analyzing Web-based malware, Google indicates:
Although very beneficial, Internet transactions can expose user sensitive information. Banking and medical records, authorization passwords and personal communication records can easily become known to an adversary who can successfully compromise any of the devices involved in online transactions.
Unfortunately, the user’s personal computer seems to be the weakest link in these transactions.
Contrary to the small set of applications running in the tightly managed and frequently updated commercial servers, a personal computer contains a large number of applications that are usually neither managed or updated. To make things worse, discovering older, vulnerable versions of popular applications is an easy task: a single visit to a compromised Website is sufficient for an attacker to detect and exploit a browser vulnerability.
In most cases, a successful exploit results in the automatic installation of a malware binary, a drive-by-download.
The installed malware often enables an adversary to gain remote control over the compromised computer system and can be used to steal sensitive information such as banking passwords, to send out spam or to install more malicious executables over time.
What does Google aim to do?
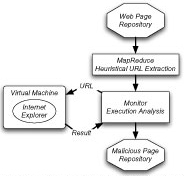
To address this problem and to protect users from being affected while browsing the Web, we have started an effort to identify all Web pages on the Internet that could potentially be malicious. We apply simple heuristics to the crawled pages repository to determine which pages attempt to exploit Web browsers.
Our goal is to observe the malware behavior when visiting malicious URLs and discover if malware binaries are being downloaded as a result of visiting a URL. Websites that have been identified as malicious are labeled as potentially harmful when returned as a search result.
Google has determined “attack strategies” on content that enable browser exploitation to turn Web pages into “malware infection vectors”: Advertising, third-party widgets, user contributed content and Web server security are all in (not so nice) play.
The number one search engine Google proudly declares that it is often used by people as the “gateway to the Internet.”
Google has a $150 billion (market cap) vested interest in:
1) A harmless Internet gateway,
2) An infection free billions of Web pages that it provides the gateway to,
3) Deflecting botnet responsibility to the (Microsoft) PC.
ALSO: Google zeal breeds more identity theft risks and
Google user data cloud: Do you trust it? and
Google vs. Google on privacy, or not and
Google plots server farm land grab in Europe