Japanese government to create and maintain defensive malware

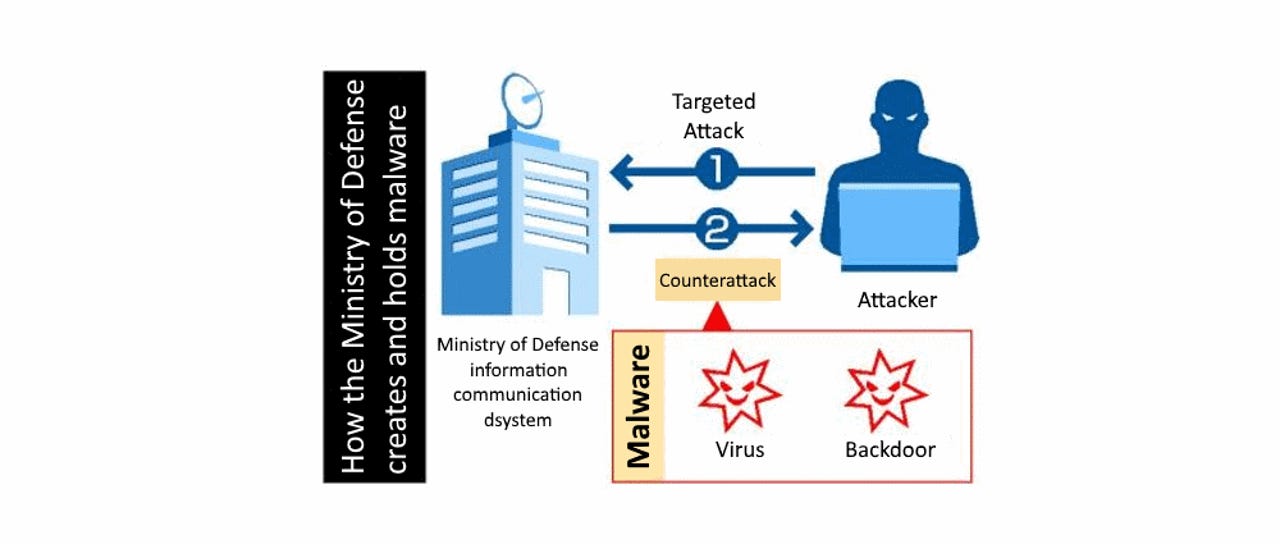
The Japanese Defense Ministry will create and maintain cyber-weapons in the form of malware that it plans to use in a defensive capacity.
Once created, these malware strains, consisting of viruses and backdoors, will become Japan's first-ever cyber-weapon, Japanese media reported earlier this week, citing a government source [1, 2, 3].
The malware is expected to be finished by the end of the current fiscal year and will be created by contractors, and not government employees, a source familiar with the situation told ZDNet.
No official details are available about what the malware's capabilities will be or the exact scenarios in which the government plans to use it, although a graph released by the government suggests the malware will only be used when Japanese institutions will be under attack, and only against the attacker.
Japan expanding into cyber battlefield
The news comes as the Japanese military has been expanding and modernizing to keep up with modern times and to counteract China's growing military threat in the region.
As part of this modernization effort, the Japanese government plans to expand its military's reach into "cyber," which NATO formally declared as an official battlefield in June 2016, next to air, ground, and sea.
Japan becomes just the latest country to formally recognize that it owns and develops cyber-weapons. The others include the US, the UK, and Germany.
Israel, China, Russia, North Korea, and Iran are countries that own, develop, and aggressively use cyber-weapons, but they've never formally acknowledged it.
Tokyo government sources told local media that they hope that just by being in the possession of a cyber-weapon, this would deter foreign actors from attacking the country.
This might be a foolish approach, as the US --the country with one of the largest and most dangerous assortments of cyberweapons-- is constantly under attack from Chinese, Russian, Iranian, and North Korean hackers.
This is also the second time the Japanese government attempts to create a cyber-arsenal after a previous attempted didn't yield expected results, when in 2012 it contracted Fujitsu to create "search and destroy" malware.
Japan's plan to hack citizens' IoT devices
Security
Nevertheless, the Japanese government seems set in its plan for bolstering its cyber-capabilities and its ability to react to cyber-attacks.
Earlier this year, the government passed legislation allowing National Institute of Information and Communications Technology (NICT) employees to hack into citizens' IoT devices using default or weak credentials, as part of an unprecedented survey of insecure IoT devices.
The plan is to compile a list of insecure devices that use default and easy-to-guess passwords and pass it on to authorities and the relevant internet service providers, so they can take measures to alert consumers and secure the devices.
This plan was set in motion to secure IoT devices before the Tokyo 2020 Olympics and avoid Olympic Destroyer and VPNFilter-like attacks.
Ironically, all these plans are originating from Japan's new Cybersecurity Department, part of its Defense Ministry. Yoshitaka Sakurada, chief of Japan's Cybersecurity Department came under heavy criticism and ridicule last year when he publicly acknowledged that he does not own, use, or know that much about computers.
North Korea's history of bold cyber attacks
Related government coverage:
- DHS gives agencies 15-day deadline to patch security flaws
- French government releases in-house IM app to replace WhatsApp and Telegram use
- Only six TSA staffers are overseeing US oil & gas pipeline security
- EU votes to create gigantic biometrics database
- China uses biometrics and digital scanning 'data doors' to track Muslim minority
- UK could build an automatic national defence system, says GCHQ chief
- How Estonia became an e-government powerhouse TechRepublic
- Sri Lanka blocks social media after deadly Easter explosions CNET