Massive comment spam attack on Digg.com leads to malware
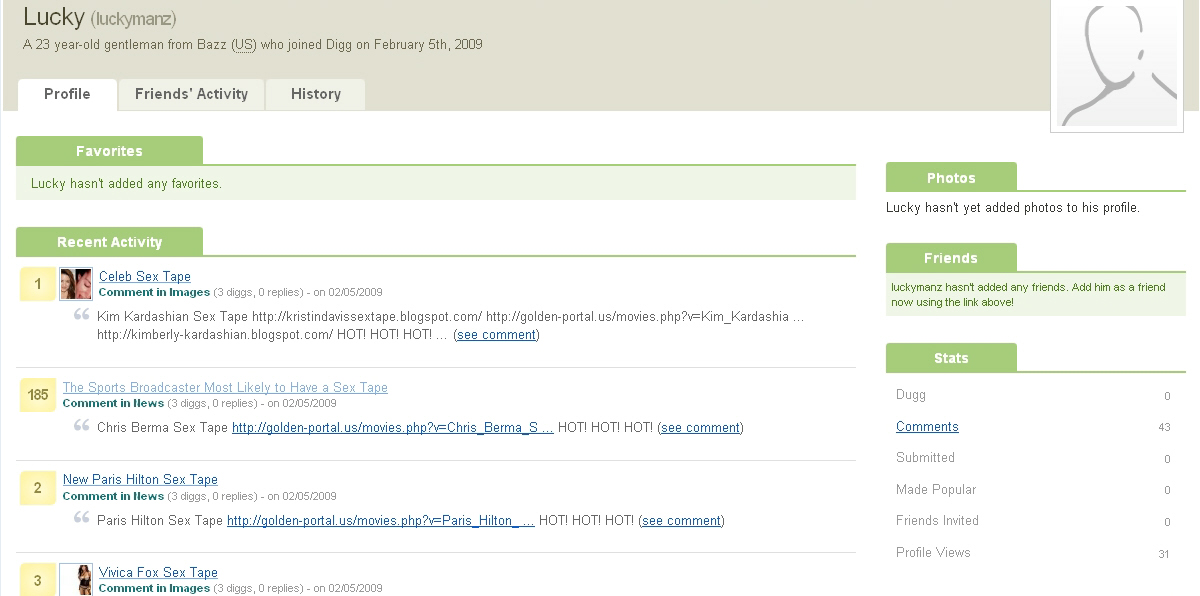
Despite the obvious similarities with last month's Google Video keywords poisoning attack, the comment-spam campaign at Digg.com is unique in the sense that it appears to have been active for over an year now. Let's dissect the campaign, and explain how it works.
So basically, you have a catchy title submitted through a bogus account, with a multitude of bogus accounts commenting on it, and linking to more malware serving domains. Or exactly the opposite - bogus accounts commenting on legitimate stories since January, 2008. This practice of self-recommendation greatly reminds me a similar Ebay bot talk scheme back in 2006, where bogus accounts were automatically giving positive recommendation to fraudulent accounts, all operated by the same person/gang.
- Go through related abuse of Web 2.0 services by cybercriminals: Bogus LinkedIn profiles serving malware; Spammers targeting Bebo, generate thousands of bogus accounts; Malware and spam attacks exploiting Picasa and ImageShack; Twitter being used to distribute malware; Cybercriminals syndicating Google Trends keywords to serve malware; Malware-infected WinRAR distributed through Google AdWords
Digg.com's abuse department has already been notified of all the related malware domains used across the site.
UPDATE: The following is a complete list of the malware domains used within the comments posted at Digg.