New KryptoCibule Windows malware is a triple threat for cryptocurrency users

Cyber-security firm ESET has published a report today detailing a new strain of Windows malware that the company has named KryptoCibule.
ESET says the malware has been distributed since at least December 2018, but only now surfaced on its radar.
According to the company, KryptoCibule is aimed at cryptocurrency users, with the malware's main three features being to (1) install a cryptocurrency miner on victims' systems, (2) steal cryptocurrency wallet-related files, and (3) replace wallet addresses in the operating system's clipboard to hijack cryptocurrency payments.
These features are the results of extensive development work from the part of the malware's creators, who have slowly added new items to KryptoCibule's code since its first version back in late 2018.
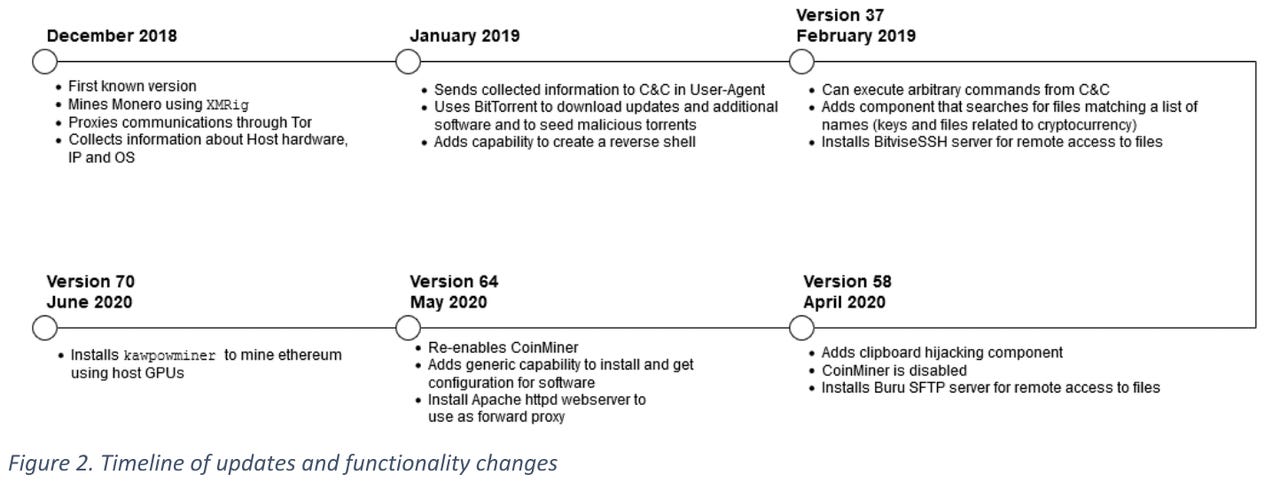
According to ESET, the malware has slowly evolved into a convoluted multi-component threat, far above what we have seen in most other malware strains.
Currently, the malware is spread via torrent files for pirated software. ESET says that users who download these torrents will install the pirated software they wanted, but they'll also run the malware's installer as well.
This installer sets up a reboot persistence mechanism that relies on scheduled tasks and then installs the core of the KryptoCibule malware (the launcher), the OS clipboard hijacker module, and Tor and torrent clients.
ESET says KryptoCibule uses the Tor client to securely communicate with its command-and-control (C&C) servers, hosted on the dark web, while the torrent client is used to load torrent files that will eventually download other additional modules, such as proxy servers, crypto-mining modules, and HTTP and SFT servers, all useful for one or more tasks in the malware's modus operandi.
All in all, KryptoCibule is bad news for cryptocurrency users, since this is clearly a strain designed by persons with knowledge of modern malware operations.
However, there is also good news, at least for now. ESET says that despite being a pretty complex threat, KryptoCibule's distribution appears to have been limited to only two countries, namely the Czech Republic and Slovakia.
ESET researchers say that almost all the malicious torrents distributing pirated software laced with KryptoCibule were only available on uloz.to, a popular file-sharing site in the two countries.
This limited distribution appears to have been something that was planned from the beginning, as KryptoCibule also contains a feature that checks for the presence of antivirus software on a victim's computer, and this module only checks for the presence of ESET, Avast, and AVG - all three being antivirus companies based either in the Czech Republic and Slovakia and most likely to be on the computers of most targeted users.
However, the fact that this malware strain is currently only distributed in a small area of the globe is no reason to believe this will remain so in the future.
Users should remain vigilant, and the simplest way to avoid a threat like KryptoCibule is to not install pirated software. Multiple reports over the last decade have warned users that most torrent files for pirated software are usually laced with malware and not worth the risk.