Obama community blog redirecting to malware

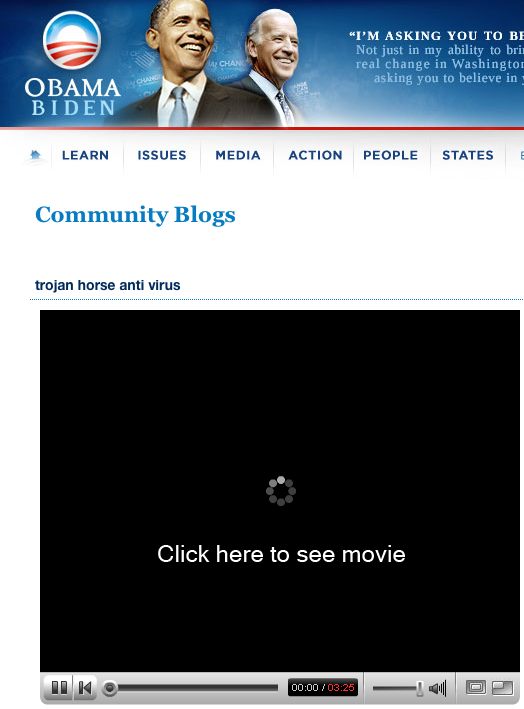
During the course of follow-up research on the Obama malware blast, Sascha Siekmann, a Support Engineer at Cloudmark (disclosure), discovered that malware authors are using the Community Blogs section of the Barack Obama campaign website as a first hop to a website hosting malware. Users are lead to the Community Blog page by searching on Google for terms like "obama trojan anti-virus". The community blog page contains a single antimated GIF image that, when clicked, takes users to the actual malware host.
Gaming search engines to redirect unsuspecting users is by no means a new trick. Attackers are using both the reputation of the search engine as well as the reputation of Barack Obama's community blog as additional incentives to lure people into installing malicious software. This specific instance is just another example of the extent of today's malware problem.