Only 5.5% of all vulnerabilities are ever exploited in the wild

New research published this week has shed some much-needed light onto the world of vulnerability exploitation, revealing how many of the total number of security flaws discovered in the past ten years have been actually exploited in the wild.
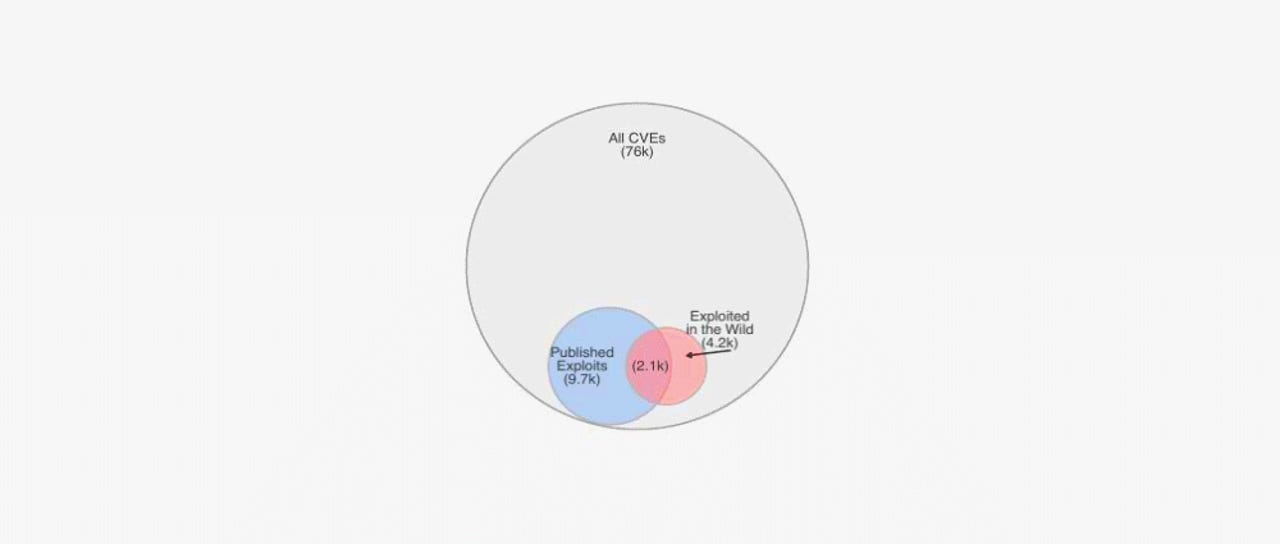
The research -- considered the most extensive of its type to date -- found that only 4,183 security flaws from the total of 76,000 vulnerabilities discovered between 2009 and 2018 had been exploited in the wild.
More interestingly, researchers found that there was no correlation between the publication of proof-of-concept (PoC) exploit code on public websites and the start of exploitation attempts.
The research team said that of the 4,183 security flaws that were exploited in the wild between 2009 and 2018, only half had exploit code listed on public sites.
This means that the lack of a public PoC did not necessarily stop attackers from exploiting certain vulnerabilities -- with some hackers crafting their own exploits when needed.
High-severity flaws were exploited the most
Furthermore, the research also exposed that most vulnerabilities that are exploited in the wild are security flaws that have a high CVSSv2 severity score (which can go from 1 to 10, with 10 being assigned to the most dangerous and easy to exploit vulnerabilities).
"Just under half of all exploited vulnerabilities have a CVSS score of 9 or higher," the research team said.
Research work sources
The data at the heart of this research has been compiled from a multitude of sources.
For example, the list of all security flaws, scores, and vulnerability characteristics has been extracted from NIST's National Vulnerability Database (NVD).
Data relating to exploits found in the wild was collected from FortiGuard Labs, and evidence of exploitation was also gathered from the SANS Internet Storm Center, Secureworks CTU, Alienvault's OSSIM metadata, and ReversingLabs metadata.
Information about written exploit code came from Exploit DB, exploitation frameworks (Metasploit, D2 Security's Elliot Kit, and Canvas Exploitation Framework), Contagio, Reversing Labs, and Secureworks CTU, with the research team finding 9,726 PoCs published between 2009 and 2018.
Furthermore, through Kenna Security, security researchers also obtained a count of the prevalence of each vulnerability derived from scans of hundreds of corporate (customer) networks derived from vulnerability scanner information.
The future
Researchers hope that their work on assembling the biggest study on security flaws (and their exploitation) known to date will help companies prioritize the vulnerabilities they want to patch first, and which are most likely to come under attack.
The team's work showed that the higher the CVSSv2 score a vulnerability has, the higher are the chances that it will come under heavy exploitation, regardless if exploit code becomes public or not.
Furthermore, the number of vulnerabilities that come under attack is one in 20, rather than one in a 100, as older research work had shown in the past.
Last but not least, the research team also wants that their work will "augment the overall CVSS framework" with new information about the chances that a specific vulnerability is likely to come under exploitation, helping provide better guidance to organizations who rely on CVSS scores to assess and prioritize patches.
Additional details about this research can be found in a white paper named "Improving Vulnerability RemediationThrough Better Exploit Prediction" that was presented yesterday at the 2019 Workshop on the Economics of Information Security in Boston.
Top tips to keep safe around your voice assistant
Related cybersecurity coverage:
- I2P network proposed as the next hiding spot for criminal operations
- Hollywood lie: Bank hacks take months, not seconds
- New attack creates ghost taps on modern Android smartphones
- Apple announces 'Sign in with Apple' feature
- New Iranian hacking tool leaked on Telegram
- Wave of SIM swapping attacks hit US cryptocurrency users
- How WannaCry is still launching 3,500 successful attacks per hour TechRepublic
- The best identity theft monitoring services for 2019 CNET