openid: The once and future enterprise Single Sign-On?

The decision two weeks ago by Yahoo! to support the burgeoning openid initiative, where users choose their preferred user account provider for logging into other Web sites, was a defining moment for the increasingly popular effort to bring order and sanity to the often confusing world of user identity on the Web. This major move by Yahoo! underscores how new models for user identity and security are becoming strategically important in the online world, and it also has long-term implications for the enterprise, as we'll see.
Enterprises will be able to manage the growing problem of the proliferation of accounts created in external, off premises Web apps.There's no doubt that Yahoo!'s addition of over 250 million accessible user accounts to openid, which can now be used to log into the thousands of openid-compliant Web sites, is a significant win for an initiative that is starting to reach critical mass. My own tests show that Yahoo!'s support for only the newer, more secure specification of openid greatly limits the number of external Web sites you can actually access with your Yahoo! account, however this issue will surely be resolved as more 3rd party sites adopt the new spec.
More interestingly, Yahoo! at this time does yet not allow 3rd party issued openids to be used to access its own Web properties. Why is this vital? Because it will fundamentally limit the usefulness of open Web identity, and openid; what's the point of having an identity from your preferred provider -- or as we'll see below, from your workplace -- if you can't use it where you want to? This one way adoption of open Web identity is common among the major adopters in the space so far.
Provider-only support of open Web identity is going to be a major challenge for the movement until someone articulates the value proposition for allowing 3rd party authentication of accounts from other Web sites. Read Dare Obasanjo's reasoning around this in the second half of this post.
Other major Web firms and software companies have been pursuing the grail of open -- or mostly-open -- Web identity for several years now, including most notably Microsoft and Google. Josh Catone over at Read/Write Web wrote yesterday about Microsoft's stated intent to join the openid bandwagon, which will likely push the number of openid accounts well past half a billion, regardless of what happens with Microsoft's acquisition play for Yahoo! This kind of scale of support will put open identity, and specifically openid, on the map and hopefully simplify and empower Web users around the world.
Open identity does push users into considering their Terms of Service of their provider much more carefully, since the're making a long-term strategic decision with whom they'll will invest with their Web identity, and whether they offer a good home for what may be their last new Web account ever. A quick examination of Microsoft's Live ID (the open Web identity formerly known as Passport) shows how Microsoft has had to remake their service to be more open and friendly to users and businesses that support it. Expect that many of today's identity providers will begin making their offerings more appealing for those shopping for their new Web super-identity. This will likely include, as we see, some enterprises.What's so important about open Web identity and how does it affect enterprise identity?
Well for one, when using openid sites that allow 3rd party identities, users need only use a single set of account credentials for everything they do, from logging into Web apps, social networks, and e-commerce sites to posting on their blog and using their online banking and trading accounts. At least that's the vision, until more sites allow 3rd party identities to log in. Second, while much is made about how the authentication process of open Web identity is decentralized (it is), one thing it also does is recentralize ownership, control and management of identity in a single place. In other words, open Web identity allows us to choose the holder of a single Web account we can use any place that supports the same identity standards.
Getting sites to support 3rd party identities: Is the key encouraging open enterprise identities?
This is not to say the using openid and other Web identities is easy for end users at the moment. In fact it's sometimes bewildering as you have to go the Web site you want to use, specify your openid authentication URL, visit the site that holds your identity to log in, login, and then go back to the site you wanted to use. Usability will improve, however, as sites implement better, smoother integration approaches over time. The next issue around the future of Web identity after basic usability is about encouraging Web businesses to accept 3rd party Web identities for log in and not just letting other sites use their accounts elsewhere. Most sites are quite happy to have their identities used on other sites, but fewer want other entities -- especially their competitors -- to own their user's accounts and become a gateway for access.
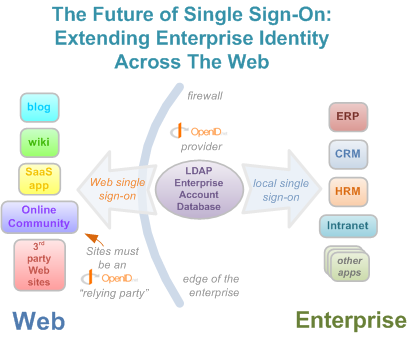
This is where discussion of moving enterprise identities out onto the Web starts to look increasingly promising. Right now the vast majority of medium and large enterprises already have a single sign-on environment, where identity is centralized, and one log-in to the network gives you access to all the local IT resources and applications. The Web is one place where IT departments have been unable, except for point SaaS implementations, to extend the the important single-sign on experience. As off premises SaaS and Web-based applications of every kind grows in adoption over the next few years, enterprises will be faced with a fragmentation of their identity strategies, as users accumulate collections of external user ids and passwords for the external Web sites they use to conduct the company's business.
This will return many enterprises to the classic headaches of years past: No single way of provisioning, managing, monitoring, and shutting down worker accounts. Without some form of externally federated identity, there's just no easy way to centrally manage the accounts workers create on external Web sites. Functions such as turning off the accounts of departing employees, guaranteeing future access to corporate data stored by workers in external sites, and so on don't scale well without either an iron grip on worker Web usage -- something increasingly futile as the consumerization of IT continues apace -- or with forthright support of open Web identity.
However, this could potentially be resolved if -- and this will be a big if for many -- enterprises decided to become openid providers themselves. This would let workers -- directed by official company policy -- safely use their existing enterprise identities on any openid-compliant Web site anywhere on the Web. In this way, thousands of existing sites would automatically be the beneficiaries of millions of new enterprise identities, provisioned for mandated use on the Web as enterprises forbid creating external accounts outside their sphere of influence. And enterprises would gain single sign-on for the Internet (at least the openid portion of it) as well as regain a single point of management for their worker's identities. Support for enterprise openid would also provide a much higher degree of protection over the access of the information kept in remote SaaS applications.
In other words, strategic support of openid by enterprises could lead to significant gains in governance, risk management, operational efficiency, and compliance goals by giving enterprises direct oversight of the accounts their workers use elsewhere on the Web.
If this value proposition bears out -- that by supporting 3rd party openids, a site will actually draw new traffic from high value sources, and that enterprises will be able to manage the growing problem of the proliferation of accounts created in external, off premises Web apps -- then you have a recipe that goes a significant way towards solving one of the largest problems in the open identity world: Providing a compelling business reason to offer full support of open identity, both as a provider and as as a consumer of external accounts.
And while openid iteself seems to have the upper hand in terms of marketshare and competent execution, it's still too early to declare a winner in the Web identity sweepstakes. However, there's no reason that enterprises can't support all the digital identity and open social graph initiatives they find rewarding today, creating an open, successful two-way relationship with the Web and its countless offerings.It's just another example of how opening up and giving up control on the network can create gains larger than what you relinquish. For it's clear that while there will be issues with open Web identity, particularly around phishing and other exploits, the advantage of having a single, simple, straightforward network identity for workers wherever they go could be an enormous win for forward-thinking enterprises.
Are you considering adopting open Web identity in your organization? Tell your story in TalkBack below.