Researcher prints 'PWNED!' on hundreds of GPS watches' maps due to unfixed API

techrepublic cheat sheet
A German security researcher has printed the word "PWNED!" on the tracking maps of hundreds of GPS watches after the watch vendor ignored vulnerability reports for more than a year, leaving thousands of GPS-tracking watches --some of which are used by children and the elderly-- open to attackers.
Also: Online security 101: Tips for protecting your privacy
Speaking at the Troopers 2019 security conference that was held in Heidelberg, Germany, at the end of March, security researcher Christopher Bleckmann-Dreher presented a series of vulnerabilities impacting over 20 models of GPS watches manufactured by Austrian company Vidimensio.
The watch models all share a common backend API, which works as an intermediary and storage point between the GPS watches and associated mobile apps.
Back in December 2017, Dreher discovered flaws in the mechanism through which the GPS watches communicate with this backend API server.
His researcher began after German authorities banned the sale children's smartwatches with remote-listening capabilities --going as far as telling parents to destroy these types of watches-- after many brands were found to run on vulnerable firmware.
Consistent with the warning from German authorities, Dreher found security flaws that would have allowed threat actors to eavesdrop and track users wearing Vidimensio Paladin GPS watches, but also alter data stored on the API server and issue various commands to users' watches.
Watch vendor notified of security flaws in late 2017
The researcher said he notified Vidimensio of his findings at the end of December 2017, but the company had failed to take any action following his initial report.
Since most of these watches were popular in Austria and Germany, Dreher worked at the time with German IT news publication Heise.de to report the security flaws to the manufacturer, who, under public pressure, issued fixes in April 2018.
But in an interview with ZDNet today, Dreher said these patches only addressed the eavesdropping threat, but not the other security flaws.
"In 03/2018 the vendor removed the eavesdrop/monitor command from his backend," Dreher told ZDNet. "Nowadays monitor mode can be activated by sending an SMS directly to the watch, [but the watch's SIM] mobile number must be known."
"The SMS command is the blacked out port in the test report of the Federal Network Agency of Germany (BNetzA), see page 54 in my slide deck."
The other flaws remained unpatched --including the ability to alter data on the API server and send commands to users' watches.
Furthermore, in his Troopers presentation (see video below) the researcher said that the flaws he initially found in the Paladin model also impacted over 20 other models from the same vendor.
Dreher's new warning comes as the number vulnerable Vidimensio GPS watches grew ten times since December 2017, despite the warning from German authorities to destroy and stop using children smartwatches with intrusive tracking and eavesdropping capabilities.
According to the researcher, the number has grown from around 700 to 7,000, of which 3,000 have been active in the past month.
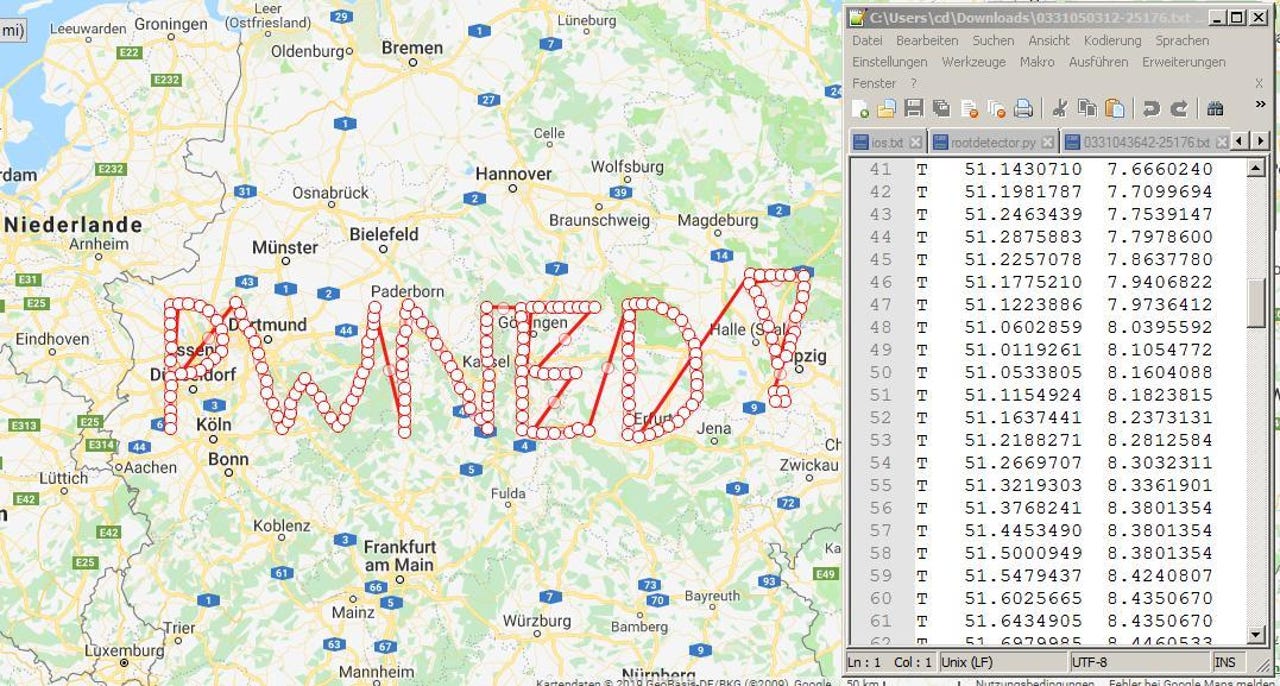
Over 300+ watches have been PWNED!
To raise awareness to these still-unpatched devices, Dreher told ZDNet that he has now turned to an unconventional strategy. The researcher has been using one of the security flaws he discovered to insert fake GPS coordinates in people's location history.
The researcher designed these fake GPS coordinates to look like the word "PWNED!" when displayed on the location history section map --displayed inside the mobile apps and the watches' web dashboard.
"I inserted fake GPS coordinates in watches (about 300) that have not been online since early 2018," the researcher told ZDNet. "I assume these watches have been destroyed by their owners as the BNetzA stated in their ban notice."
"I can do it at scale, so bad hacktivists could also do it," the researcher said.
The entire exploit chain, which he described in his Troopers talk, relies on changing a simple parameter, and entering another user's ID --which are sequential and start from 0 and go up to the number assigned to the latest registered user (currently around 7,000).
Dreher told ZDNet that he contacted BNetzA --the German federal agency who issued the ban-and-destroy notice on children smartwatches in 2017-- seeking help in forcing the vendor to patch its security flaws, but the agency declined to help, citing its recent ban notice as its lack of action.
Vidimensio did not respond to a contact request for additional details made through the company's website.
While the sale of children's smartwatches has been banned in Germany, it's pretty clear that the ban has not been enforced by authorities, and that users have continued to buy such devices for themselves, children, or elderly--ignoring the possible security risks.
But the tide is changing in regards to cyber-security and privacy-related issues at the EU level. In February 2019, EU authorities issued the first ever product recall over data security issues. Not coincidentally, it was for a kids smartwatch manufactured and sold primarily in Germany.
Dreher Troopers 2019 presentation includes the following list of Vidimensio GPS watch models that are deemed vulnerable.
Best wireless chargers for your smartphone or smart watch
More cybersecurity coverage:
- French gas stations robbed after forgetting to change gas pump PINs
- Researchers publish list of MAC addresses targeted in ASUS hack
- North Korean hackers continue attacks on cryptocurrency businesses
- Top dark web marketplace will shut down next month
- Report deems Russia a pioneer in GPS spoofing attacks
- Over 13K iSCSI storage clusters left exposed online without a password
- We invited professional hackers to attack us CNET
- The top 10 alternatives to the Apple Watch TechRepublic