Russian state hackers rarely share code with one another

Russia's state-sponsored hacking groups rarely share code with one another, and when they do, it's usually within groups managed by the same intelligence service, a new joint report published today reveals.
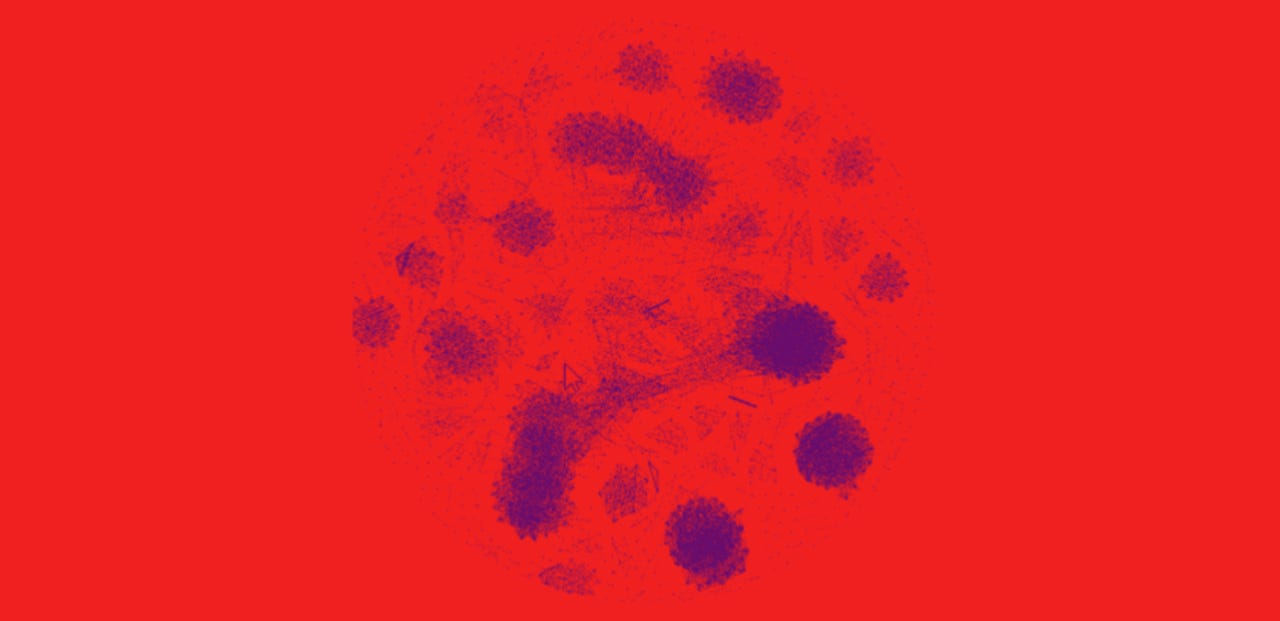
This report, co-authored by Check Point and Intezer Labs, is a first of its kind in its field. The two companies looked at nearly 2,000 malware samples that were previously linked to Russia state-sponsored hacking groups, in order to get an idea of how these malware samples related to each other.
Their investigation found 22,000 connections and 3.85 million pieces of code that were shared among the malware strains.
The conclusion of this vast research effort was the revelation that Russian APTs (advanced persistent threat, a term used to describe government-backed hacking groups) don't usually share code with one another.
Furthermore, in the rare instances they do, code reuse usually occurs inside the same intelligence service, showing that Russia's three main agencies that are in charge of foreign cyber-espionage operations don't collaborate for their campaigns.
The report's findings come to confirm previous journalistic investigations into Russian cyber operations but also reports from other foreign intelligence services.
These previous reports found that all of Russia's cyber-espionage operations can be tracked down and attributed to three intelligence services -- the FSB (Federal Security Service), the SVR (Foreign Intelligence Service), and GRU (Main Intelligence Directorate for Russia's military) -- none of which collaborate or coordinate with one another.
The Russian government has fostered competition among the three agencies, which operate independently from one another, and compete for funds. This, in turn, has resulted in each group developing and hoarding its tools, rather than sharing toolkits with their counterparts, a common sight among Chinese and North Korean state-sponsored hackers.
"Every actor or organization under the Russain APT umbrella has its own dedicated malware development teams, working for years in parallel on similar malware toolkits and frameworks," researchers said.
"While each actor does reuse its code in different operations and between different malware families, there is no single tool, library or framework that is shared between different actors."
Researchers say these findings suggest that Russia's cyber-espionage apparatus is investing a lot of effort into its operational
security.
"By avoiding different organizations re-using the same tools on a wide range of targets, they overcome the risk that one compromised operation will expose other active operations," researchers said.
Interactive map
"A research of such scale, to map code connections inside a whole ecosystem wasn't done before," Itay Cohen, a security researcher with Check Point told ZDNet in an email.
"We didn't analyze the nature of each code since we are talking about thousands of samples," Cohen added. "We can say that the obvious clusters we see in our mapping can tell us that each organization is working separately, at least in the technical aspect. Some clusters, such as the one of ComRAT, Agent.BTZ, and Uroburos, represents an evolution of a malware family across the years."
The research team launched a website today with an interactive map for highlighting the connections between the Russian APT malware samples they analyzed.
They also released a signature-based tool to scan a host or a file against the most commonly re-used pieces of code by Russian APTs. This tool should help organizations detect if they've been infected by malware that has ties (shared code) with older strains of Russian APT malware.
More info about this research can be found on the Check Point or Intezer Labs websites.