Security researcher discloses Safari bug after Apple delays patch

A security researcher has published details today about a Safari browser bug that could be abused to leak or steal files from users' devices.
The bug was discovered by Pawel Wylecial, co-founder of Polish security firm REDTEAM.PL.
Wylecial initially reported the bug to Apple earlier this spring, in April, but the researcher decided to go public with his findings today after the OS maker delayed patching the bug for almost a year, to the spring of 2021.
How does the bug work
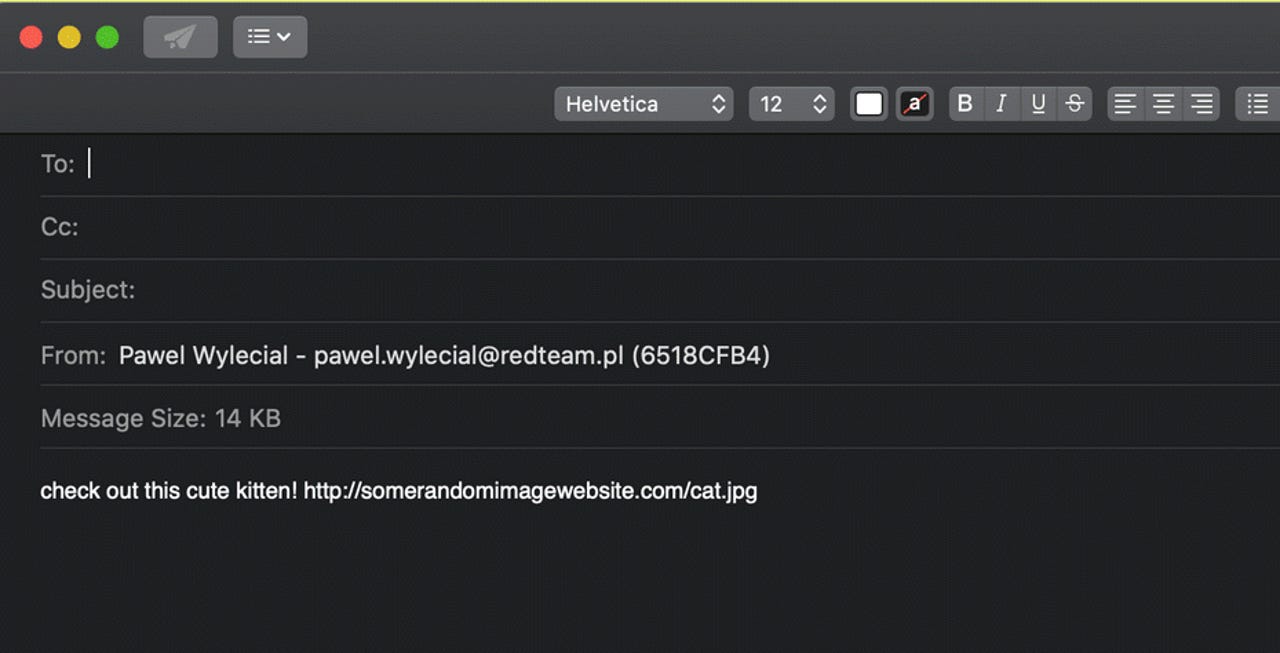
In a blog post today, Wylecial said the bug resides in Safari's implementation of the Web Share API — a new web standard that introduced a cross-browser API for sharing text, links, files, and other content.
The security researcher says that Safari (on both iOS and macOS) supports sharing files that are stored on the user's local hard drive (via the file:// URI scheme).
This is a big privacy issue as this could lead to situations where malicious web pages might invite users to share an article via email with their friends, but end up secretly siphoning or leaking a file from their device.
See the video below for a demonstration of the bug, or play with these two demo pages that can exfiltrate a Safari user's /etc/passwd or browser history database files.
Wylecial described the bug as "not very serious" as user interaction and complex social engineering is needed to trick users into leaking local files; however, he also admitted that it was also quite easy for attackers "to make the shared file invisible to the user."
Recent criticism of Apple's patch handling
However, the real issue here is not just the bug itself and how easy or complex it is to exploit it, but how Apple handled the bug report.
Not only did Apple fail to have a patch ready in time after more than four months, but the company also tried to delay the researcher from publishing his findings until next spring, almost a full year since the original bug report, and way past the standard 90-days vulnerability disclosure deadline that's broadly accepted in the infosec industry.
Situations like the one Wylecial had to face are becoming increasingly common among iOS and macOS bug hunters these days.
Apple — despite announcing a dedicated bug bounty program — is increasingly being accused of delaying bugs on purpose and trying to silence security researchers.
For example, when Wylecial disclosed his bug earlier today, other researchers reported similar situations where Apple delayed patching security bugs they reported for more than a year.
For two of my bugs they've told me same thing that it will be fixed on "Fall of 2020" and yesterday I ask for the update. They replied it's not a bug 😅
— Nikhil Mittal (@c0d3G33k) August 24, 2020
When in July, Apple announced the rules of the Security Research Device program, Google's vaunted Project Zero security team declined to participate, claiming that the program rules were specifically written to limit public disclosure and muzzle security researchers about their findings.
Three months before, in April, another security researcher also reported a similar experience with Apple's bug bounty program, which he described as "a joke," describing the program's goal as trying "to keep researchers quiet about bugs for as long as possible."
The industry standard for disclosure of security issues is 90 days. We're well beyond that point now. Why should I not publish?
— Jeff Johnson (@lapcatsoftware) April 21, 2020
Apple acknowledged a request for comment but did not have a statement on the issue.