Spear-phishing campaign compromises executives at 150+ companies

A cybercrime group operating since mid-2019 has breached the email accounts of high-ranking executives at more than 150 companies, cyber-security firm Group-IB reported today.
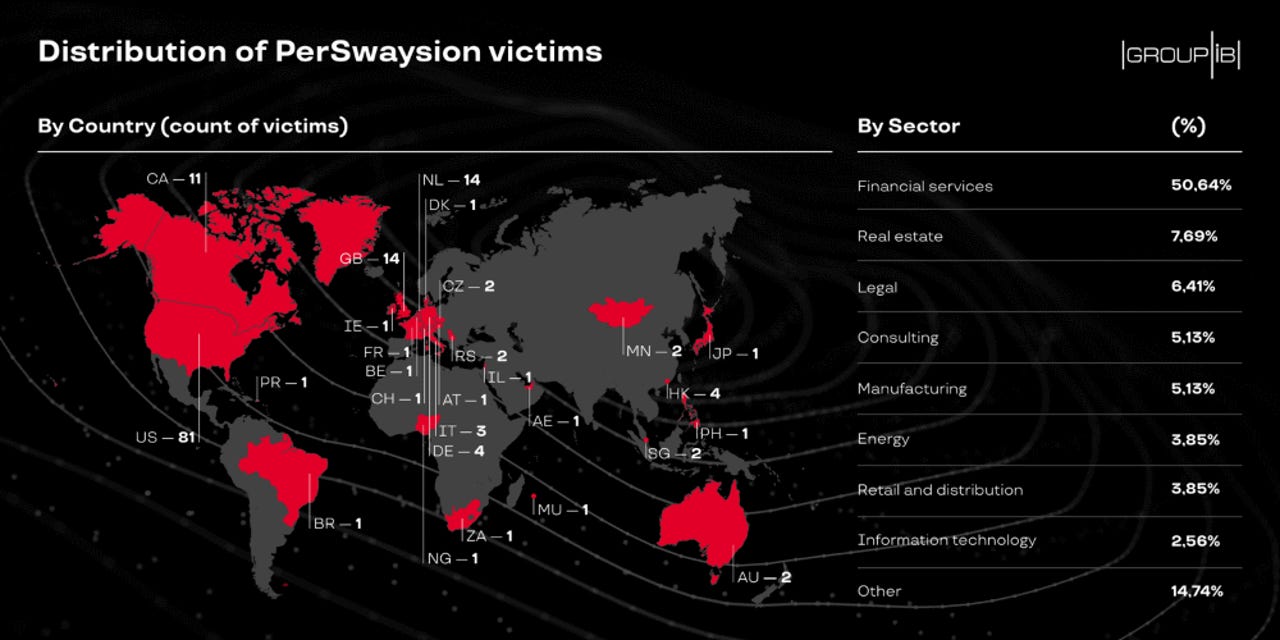
The group, codenamed PerSwaysion, appears to have targeted the financial sector primarily, which accounted for more than half of its victims; although, victims have been recorded at companies active across other verticals as well.
PerSwaysion operations were not sophisticated, but have been extremely successful, nonetheless. Group-IB says the hackers didn't use vulnerabilities or malware in their attacks but instead relied on a classic spear-phishing technique.
They sent boobytrapped emails to executives at targeted companies in the hope of tricking high-ranking executives into entering Office 365 credentials on fake login pages.
Group-IB said PerSwaysion's entire scheme could be narrowed down to a simple three-step process:
- Victims receive an email containing a clean PDF file as an email attachment. If victims open the file, they'd be asked to click a link to view the actual content.
- The link would redirect users to a Microsoft Sway (newsletter service) page, where a similar file would ask the victim to click on another link.
- This last link redirects the executive to a page mimicking the Microsoft Outlook login page, where hackers would collect the victim's credentials
PerSwaysion operators acted fast from the moment of a successful phish and usually accessed hacked email accounts within a day.
"After the credentials are sent to their [command and control servers], the PerSwaysion operators log into the compromised email accounts. They dump email data via API and establish the owner's high-level business connections," Group-IB said.
"Finally, they generate new phishing PDF files with current victim's full name, email address, company legal name. These PDF files are sent to a selection of new people who tend to be outside of the victim's organization and hold significant positions."
Group-IB said that once PerSwaysion operators sent out a new spear-phishing campaign from a compromised account, they also typically deleted impersonating emails from the outbox folder to avoid detection.
For the time being, Group-IB has been unable to determine what hackers have been doing after gaining access to these email accounts.
Hackers could be selling access to other cybercrime groups; they could be sitting, wating, and stealing intellectual property; or they could be preparing to launch a wire payment hijack (BEC scam) at a later date.
Group-IB said that based on current evidence, the PerSwaysion group appears to be formed of members based in Nigeria and South Africa, are using a phishing toolkit developed by a Vietnamese programmer, and the group's leader appears to be a suspect going by the name of "Sam."
The cyber-security firm launched today a website where executives can check if their email addresses have been acquired and targeted by the group in the past.