Spyware expert: Vonage injects ads into others' sites

Spyware expert Ben Edelman- who is so brilliant he is scary-has posted a damning study of, as he titles it "How Vonage Funds Spyware."
Citing 12 examples of this practice, Ben groups them into four buckets: Spyware-Delivered Pop-Up Ads, Banners Injected Into Others' Sites, Spyware Lead Acquisitions and Spyware-Delivered Banner Farms.
Update: through spokesperson Brooke Schulz, Vonage denies these charges.
"Vonage has investigated every case of spyware that has been brought to its attention and terminated the relationship immediately with the entities in question who we find are in fact using spyware," Schulz said. "We believe Mr. Edelman's claims that this is a significant problem with our advertising are unfounded. Vonage takes this issue seriously and is committed to having good policing policies in place to prevent our brand from being sullied by unscrupulous spyware operators."
As Ben describes it, the "injection" assertion seems the most serious.
"I have repeatedly observed Vonage ads appearing through banners injected into others' sites using spyware, without permission from those sites. In general, the resulting Vonage banners appear in places where, but for the spyware at issue, no banner would exist," Ben writes.
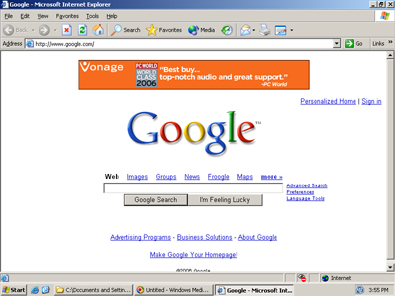
As an example, Ben sites a banner ad integrated into a Google page that appears to be integrated in Google itself. But it is really, not. Instead it was, t use Ben's term, "injected" there by Fullcontext spyware likely via a hook into Internet Explorer's API.
Oh, but Ben goes so much deeper than just showing that screen shot. He actually takes apart the packet log that he believes makes this "injection" possible.
Ben writes:
The injected Vonage ad (shown above) is unlabeled -- without any direct indication that it came from Fullcontext spyware. But packet log analysis confirms that Fullcontext was directly responsible for the injection. First Fullcontext spyware on my test PC sent a request to its controlling server (yellow), seeking an ad to inject into the Google site (shown, for good measure, as the HTTP Referer of the request, green). Fullcontext's controlling server replied with a URL to MediaPrecision (blue), which redirected me to Yield Manager (grey). Yield Manager sent back an ad that specified a URL at aQuantive's Atlas (pink) (which tracks most Vonage ad placements). Finally, that aQuantive Atlas URL is known (based on its URL syntax, red, as well as subsequent hands-on testing) to redirect to Vonage.
Next, we have the smoking gun. There's a lot of code here.. but since Ben thinks this documentation is vital to proving his "injection" assertions, well, then, so do I. If you click on the Google image in Ben's post, you'll see the code.
Not exactly eye candy by anyone's definition, but a very detailed exhibit for sure. And he has more...