This giant ransomware campaign just sent millions of malware-spreading emails

Over 23 million emails containing Locky were sent in a short amount of time.
Once considered almost dead, the Locky strain of ransomware has continued its resurgence with a new email distribution campaign, which researchers say is one of the largest malware campaigns of this half of the year.
Over 23 million messages containing Locky were sent in just 24 hours on 28 August, with the attacks spiking in time to hit US workers as they arrived at their desks on Monday morning.
The new campaign was discovered by researchers at AppRiver who say it represents "one of the largest malware campaigns seen in the latter half of 2017".
Millions of emails were sent with subjects such as 'please print', 'documents' and 'scans' in an effort to spread Locky ransomware.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
The malware payload was hidden in a ZIP file containing a Visual Basic Script (VBS) file, which if clicked, goes to download the latest version of Locky ransomware -- the recently spotted Lukitus variant -- and encrypts all the files on the infected computer.
Locky distribution email.
While the delivery method might seem basic, it's worth remembering that only a handful for the millions of messages sent need to successfully deliver the malicious payload to provide the attackers with a significant profit.
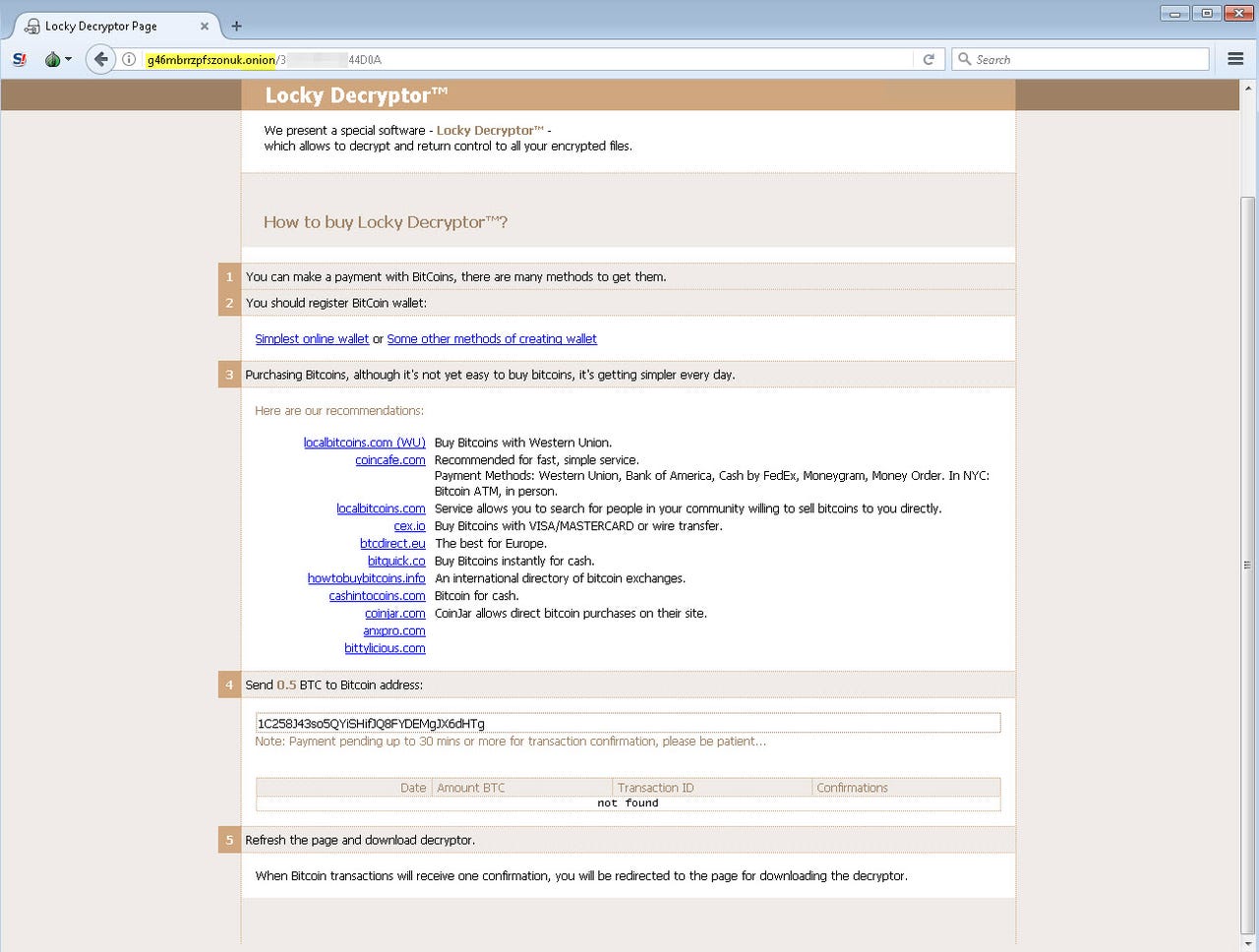
Victims unfortunate to succumb to Locky are presented with a ransom note demanding 0.5 bitcoin ($2,300/£1800) in order to pay for "special software" in the form of a "Locky decryptor" in order to get their files back.
Instructions on downloading and installing the Tor browser and how to buy Bitcoin are provided by the attackers in order to ensure victims can make the payment.
Security
Unfortunately for victims of Locky, researchers are yet to crack the latest version of the ransomware in order to provide free decryption tools.
Locky is one of the most successful families of ransomware of all time, rising to prominence during 2016 following a number of high-profile infections. Indeed, Locky was so successful that at one point it was one of the most common forms of malware in its own right.
But Locky has since had its position as king of ransomware usurped by Cerber, although this sudden resurgence shows that it remains very much a threat, especially as there isn't a free decryption tool available to victims.
This isn't the first time Locky has reappeared after a period of inactivity -- the ransomware appeared to stop spreading in December last year before coming back to life in January.
While it has never reached the scale it had last year, those behind Locky are still working on it to add new tricks to make it stronger and easier to spread, meaning it still poses a threat.
Related coverage
Locky ransomware is back from the dead again - with new 'Diablo' and 'Lukitus' variants
The godfather of ransomware returns: Locky is back and sneakier than ever
After a mysterious disappearance, Locky has reemerged -- and is borrowing attack techniques from Dridex.
Locky ransomware: How this malware menace evolved in just 12 months
Malware gets multiple updates as it tries to evade detection by security companies.
Locky ransomware campaign exploits fears of data stolen in OPM hack
Emails tell victims they need to download an attachment to view "suspicious activity" - then infects them with ransomware.
READ MORE ON CYBERCRIME
- Ransomware: The smart person's guide [TechRepublic]
- No more ransomware: How one website is stopping the crypto-locking crooks in their tracks
- After WannaCry, ransomware will get worse before it gets better
- Malware now comes with customer service [CNET]
- Cybercrime Inc: How hacking gangs are modeling themselves on big business