Thousands of web sites compromised, redirect to scareware
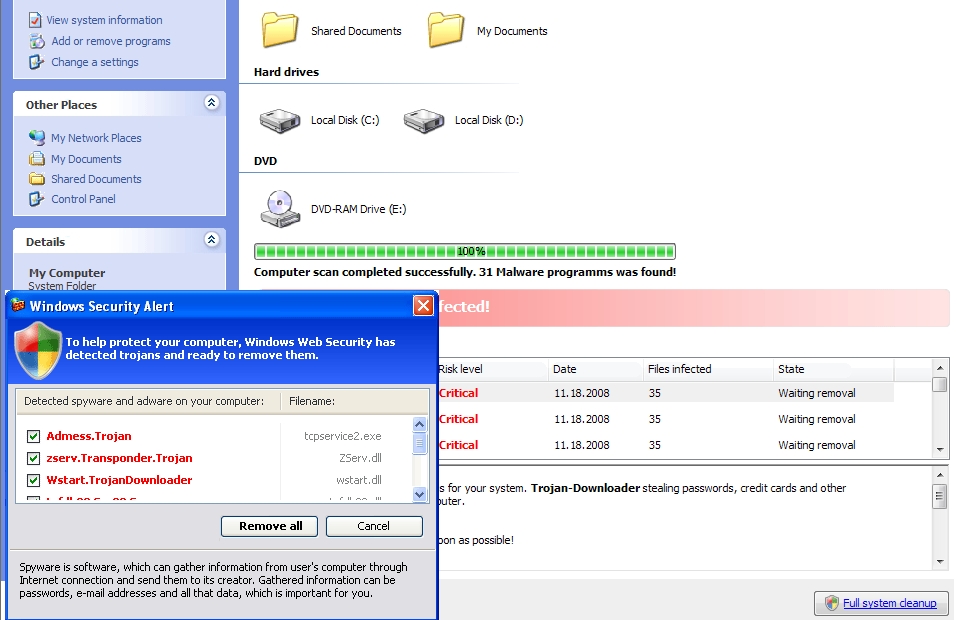
There are now over a million affected sites serving scareware, with only a small percentage of them currently marked as harmful. Google has been notified. As always, NoScript and your decent situational awareness are your best friends.
Security researchers have detected a massive blackhat SEO (search engine optimization) campaign consisting of over 200,000 compromised web sites, all redirecting to fake security software (Inst_58s6.exe), commonly referred to as scareware.
More details on the campaign:
The compromised sites are hosting legitimately looking templates, using automatically generated bogus content, with a tiny css.js (Trojan-Downloader.JS.FraudLoad) uploaded on each of them which triggers the scareware campaign only if the visitor is coming a search engine listed as known http referrer by the gang - in this case Google, Yahoo, Live, Altavista, and Baidu :
"Cyveillance has discovered a complex attack vector that uses Google search results to distribute malicious software (malware) to unsuspecting Internet users. Using this attack vector, users click on links within Google search results and are routed to sites that attempt to download malware to their computers. The attack method also relies on inattentive webmasters who do not update the software on their sites and often unknowingly provide the material that appears in the search results.
The common string albums/bsblog/category is found in the URLs for all these blogs. By simply using the Google search parameter allinurl, along, you can see how many other sites contain the same string. As can be seen in the image above, more than 260,000 URLs are presented in Google’s search index leading to blogs similar to the ones illustrated in our example.
As you can see, only a small portion of sites in the search results carry a warning provided by Google. The reason for the small number of warnings is likely because the actual attacks do not take place on the website URLs in the search results, but on the sites you’re redirected to thereby decreasing the chances that Google will designate the destination sites as harmful."
At first, it would appear that the campaign is an isolated one and is maintained by a cybercrime enterprise yet to be analyzed. However, analyzing it reveals a rather anticipated connection - the massive blackat SEO campaign has been launched by the same people who operate/or manage the campaigns for the Koobface botnet. For instance, the domains mentioned by Cyveillance, as well as the newly introduced ones over the past couple of hours, are the very same domains currently embedded on Koobface infected hosts.
- Go through related posts - The ultimate guide to scareware protection; My scareware night and how McAfee lost a customer; Scareware scammers hijack Twitter trending topics; 9/11 related keywords hijacked to serve scareware; Koobface Botnet's Scareware Business Model - Part One; Koobface Botnet's Scareware Business Model - Part Two
How did they manage the compromise the sites? Through web application vulnerabilities as the attack vector, with OWASP's recently updated Top 10 most critical web application security risks, highlighting some of the riskiest ones.