Two hacking groups responsible for huge spike in hacked Magento 2.x stores

Two hacker groups are responsible for a huge spike in the number of hacked Magento 2.x shopping sites, according to Willem de Groot, founder of Sanguine Security.
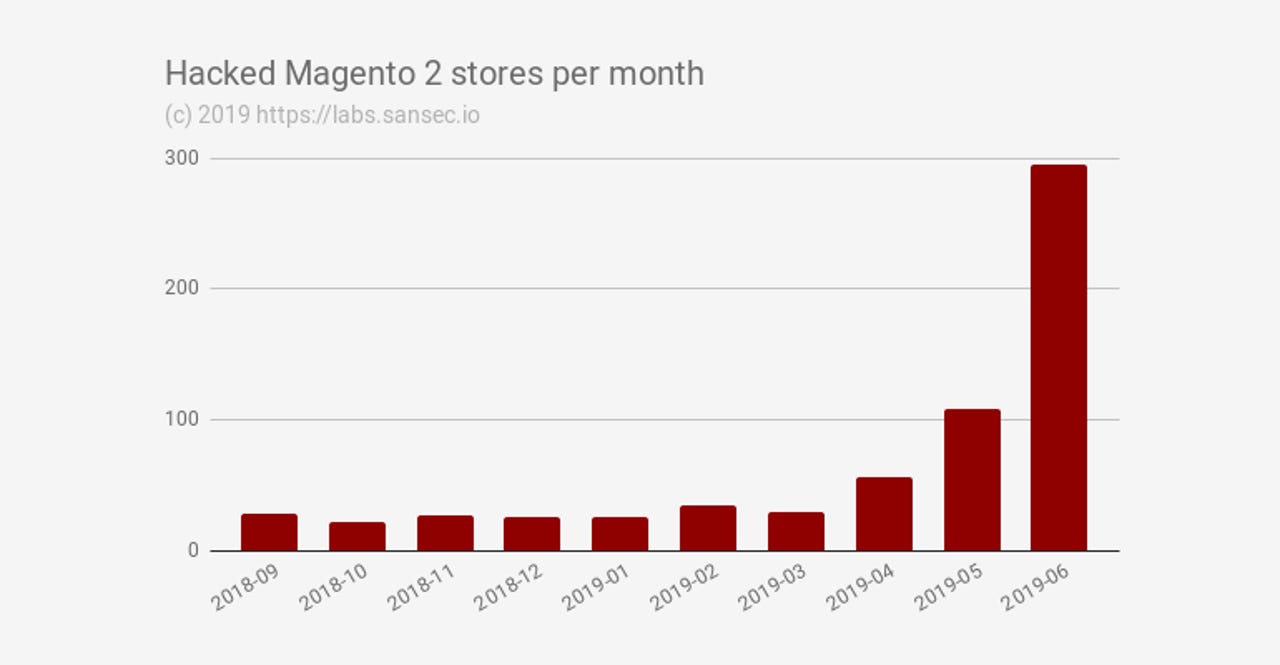
This is now the third month in a row when the number of hacked Magento 2.x sites has doubled, after it previously doubled from March to April, and again from April to May.
Spike after PRODSECBUG-2198 disclosure
At the heart of these spikes in hacked sites is "PRODSECBUG-2198," which is the codename of a security flaw in the Magento 2.x content management system (CMS), the most popular CMS for building self-hosted online shops.
The vulnerability is an SQL injection flaw in the Magento CMS that can be exploited by remote, unauthenticated attackers to take over unpatched, vulnerable sites.
The Magento team patched the bug at the end of March; however, things didn't go as planned, as attacks exploiting this bug started just 16 hours later, according to de Groot.
Things took a turn for the worse after Ambionics, the company who discovered the bug, also published proof-of-concept code just two days after the Magento patch, without giving store owners enough time to patch.
I feel it is not really professional to release a tool for exploiting it only 2 days after Magento release and on a Friday.
— Laurent Clouet (@laurent35240) March 30, 2019
After that, PRODSECBUG-2198 attacks skyrocketed, leading to an increase in the number of hacked Magento 2.x sites, with hackers planting malware on compromised stores, so they could steal payment card data from readers while they were purchasing new products.
Two groups responsible for 90% of hacked sites
"I run a daily scan on the top million sites and check for suspicious activity and verified malware," de Groot told ZDNet in an email today about how he compiled his data. "My graphs are based on verified malware."
But while there are several groups hacking and planting malware on Magento stores, de Groot says that the recent spike is almost entirely driven by the activity of only two groups.
"Two actors seem responsible," the researcher told ZDNet, "one has 70% and the other 20% of the breaches.
"The bigger one was also behind the Puma Australia hack and supports skimming of 50+ global payment services. This automation enables him/her to quickly scale the skimming operations," de Groot said.
"And once they are in, it's hard to get rid of these skimmers," the researcher added separately on Twitter. "20% of merchants get reinfected, typically within two weeks."
Besides applying updating Magento to versions 2.3.1, 2.2.8 and 2.1.17, which contain the fix for this security flaw, de Groot has also published several tips on the Sanguine Security site on how to deal with hacked sites, or how to take additional protection measures to secure Magento stores.
WordPress 5.0 is out. Here's a tour of the new features!
Related malware and cybercrime coverage:
- Ancient ICEFOG APT malware spotted again in new wave of attacks
- FIN8 hackers return after two years with attacks against hospitality sector
- Germany: Backdoor found in four smartphone models; 20,000 users infected
- Microsoft warns about email spam campaign abusing Office vulnerability
- 8 years later, the case against the Mariposa malware gang moves forward in the US
- A botnet is brute-forcing over 1.5 million RDP servers all over the world
- The dark web is smaller, and may be less dangerous, than we think TechRepublic
- Game of Thrones has the most malware of any pirated TV show CNET