UPDATE: ATI driver flaw exposes Vista kernel to attackers

(See update below for official response from ATI)
An unpatched flaw in an ATI driver was at the center of the mysterious Purple Pill proof-of-concept tool that exposed a way to maliciously tamper with the Windows Vista kernel.
Purple Pill, a utility released by Alex Ionescu and yanked an hour later after the kernel developer realized that the ATI driver flaw was not yet patched, provided an easy way to load unsigned drivers onto Vista -- effectively defeating the new anti-rootkit/anti-DRM mechanism built into Microsoft's newest operating system.
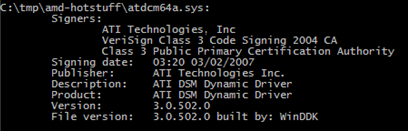
In an interview, Ionescu confirmed his tool was exploiting a vulnerability in an ATI driver -- atidsmxx.sys, version 3.0.502.0 -- to patch the kernel to turn off certain checks for signed drivers. This meant that a malicious rootkit author could essentially piggyback on ATI's legitimately signed driver to tamper with the Vista kernel.
[ SEE: Vista kernel tampering tool released, then mysteriously disappears ]
"I didn't know the [ATI] driver wasn't patched," Ionescu explained. He said he found out about the flaw from Joanna Rutkowska's Black Hat presentation (see .ppt file) and assumed it was something that was already fixed. "I wanted to be responsible about releasing the tool so I pulled it," Ionescu said, dismissing talk that he was pressured by Microsoft or Apple (where he is interning for the summer).
Ionescu said he discussed the issue with Microsoft and will likely re-release the tool after a patch is released.
A spokesman for Microsoft said the company is aware that an ATI driver might be "potentially vulnerable."
"Microsoft is in contact with ATI to help address this issue and once fixed we will assist in getting it to our customers," he said. "To the best of our knowledge, Purple Pill was a proof of concept demonstration tool that was available for a very limited time and is no longer available."
Ionescu said the tool was available for about 78 minutes and was downloaded 39 times.
[ SEE: Hardware-based rootkit detection proven unreliable ]
Among those downloaders were folks at Symantec. Eric Chien, a senior manager on Symantec's security response team, said his team looked at the Purple Pill code and was able to pinpoint the ATI driver as the culprit.
"Basically, that ATI driver has functionality that allows you to read and write kernel memory. It's either a bug or a feature of the driver. We're not sure why they're using it but because it's both signed and allowed to read/write kernel memory, any third party can use that driver to do the same thing," Chien explained in a telephone interview.
Symantec has deemed Purple Pill a hacking tool that can be used for malicious purposes and has shipped a definition update for its anti-malware products.
A spokesman for ATI said the company is investigating. (See update below)
It is likely that Microsoft will use its automatic update mechanism in Vista to ship a patch for this buggy driver. The company cannot revoke the certificate for the driver because, as Ionescu explained, it's already embedded in about 50% of all Vista laptops -- and any revocation will affect those machines.
Even after this is fixed, Ionescu said this episode points to a bigger issue of risks introduced by buggy third-party drivers.
"This is not a problem that will go away soon. As Joanna has already shown, anyone can get a driver signed. Now we know that even signed drivers have bugs that open up new ways to load something unsigned into the kernel," he said.
Ionescu suggested deeper collaboration between Microsoft and third party driver makers to improve the quality of code loading onto Vista. "Maybe they can do some code reviewing or require tests on drivers before they are signed. Something will have to be done because this is not only an ATI problem."
[UPDATE: August 11, 2007 @ 11:20 AM] ATI has confirmed the bug, which affects the AMD Catalyst software package. Here's a statement from AMD spokesman Jon Carvill:
“The market recently discovered a potential security vulnerability that could impact AMD’s Catalyst software package. After immediate investigation, AMD determined that a small section of code in one the files of our installer package file is potentially vulnerable. The AMD plan is to provide a new ATI Catalyst package no later than Monday, Aug. 13, 2007, that resolves this vulnerability. We strongly recommend that desktop ATI Radeon graphics users update to Catalyst version 7.8 once it is available on http://ati.amd.com/support/driver.html. AMD and Microsoft are also investigating additional distribution channels for this update. This vulnerability was not exclusive to AMD.”
In all likelihood, Microsoft will push this down to Windows Vista users on Patch Tuesday (August 14th) via the automatic update mechanism.