"We've toasted so many of these (VoIP) networks...

Marty Graham of Wired.com's Threat Level blog writes about an interview he had with VoIP open source security tool VoIP Hopper's co-developer Jason Ostrom.
Apparently Ostrom and business partner John Kindervag used the VoIP Hopper tool to do some penetration testing of supposedly secure VoIP networks.
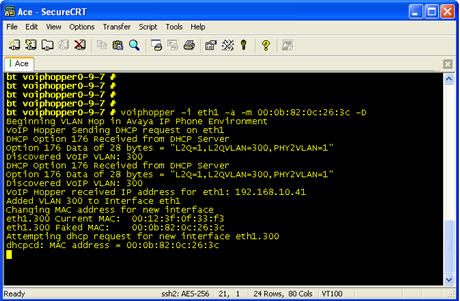
“The whole catalyst behing VoIP Hopper is we were in a hotel room with a Cisco phone,” Ostrom says. “We were (able to get) into the (hotel's) corporate network and got access to their financial and corporate network and recorded other phone calls.”
Ostrom says this hack was accomplished by means of a "really advanced hacker technique that results in VoIP hopper mimicking some Cisco data ppackets and then trades in a new Ethernet interface that gets the PC into the network where VoIP communication is being run.
“People tell us VoIP is secure by default," Ostrom tells Graham. "But a regular PC should never have access to it."
Graham also notes Ostrom told him that Cisco competitor Avaya's solution seems to be more secure than Cisco. The key reason: you need to send requests beyond a sniffer.
"But it can be breached the same way, by unplugging the phone and plugging in a PC," Graham points out. "Most VoIp users aren’t set up to keep their data secure from an attack launched through VoIP."
"In seven environments that we looked at, not one customer had a firewall between voice and data," Ostrom tells Graham. "We’ve toasted so many of these networks it’s not funny. VLAN is never, never a secure network."