Zoom defends use of local web server on Macs after security report

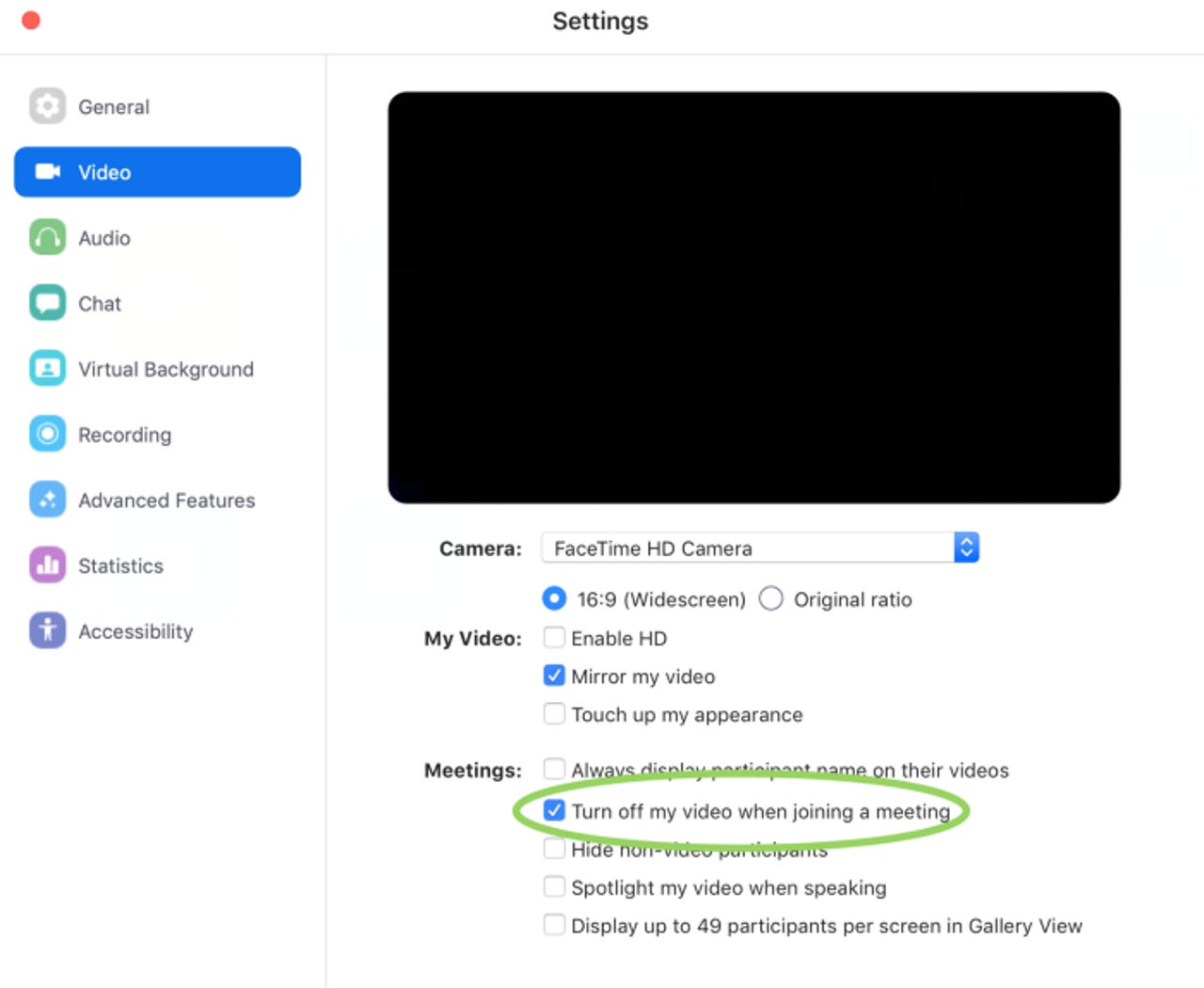
The very least that a user can do to protect themselves.
Video conferencing company Zoom has defended its use of a local web server on Macs as a "workaround" to changes that were introduced in Safari 12.
The company said in a statement that it felt running a local server in the background was a "legitimate solution to a poor user experience, enabling our users to have seamless, one-click-to-join meetings, which is our key product differentiator".
Zoom was responding to findings by security researcher Jonathan Leitschuh, who detailed the existence of the server in a blog post.
A Zoom install on a Mac will run a server on port 19421, which can be used to put a Zoom user into a call, as well update the application.
Leitschuh discovered that rather than making AJAX requests, the server uses the dimensions of an image from Zoom to handle error and status codes. He said this unique approach was done to bypass cross-origin resource sharing restrictions (CORS) since browsers do not use CORS for local servers.
"Let me start off by saying having an installed app that is running a web server on my local machine with a totally undocumented API feels incredibly sketchy to me," Leitschuh wrote.
"Secondly, the fact that any website that I visit can interact with this web server running on my machine is a huge red flag for me as a Security Researcher."
The security researcher said the use of the local server was a fundamental security vulnerability, and sites should not communicate with applications in such a fashion.
"Having every Zoom user have a web server that accepts HTTP GET requests that trigger code outside of the browser sandbox is painting a huge target on the back of Zoom," he wrote.
Zoom now signs the requests to the server, but Leitschuh maintains this is not enough to be secure.
Thanks to the report, Leitschuh said Zoom also removed the ability for a call host to automatically have participants join with video enabled.
"Zoom did end up patching this vulnerability, but all they did was prevent the attacker from turning on the user's video camera. They did not disable the ability for an attacker to forcibly join to a call anyone visiting a malicious site," the security researcher wrote.
By crafting GET requests, Leitschuh said he was able to have a URL that could drop users into a call, and thanks to the now-defunct ability of hosts, could force video and audio on for them.
Zoom said in its July release, it would save whether the user turns off video in their first call and apply it to future meetings, with these changes to occur on all its platforms.
"All first-time Zoom users, upon joining their first meeting from a given device, are asked whether they would like their video to be turned OFF," Zoom said in its statement.
"For subsequent meetings, users can configure their client video settings to turn OFF video when joining a meeting. Additionally, system administrators can pre-configure video settings for supported devices at the time of install or change the configuration at anytime."
Leitschuh also pointed out to Zoom that a domain it used for sending out updates was about to expire before May 1, but the domain was renewed in late April.
"All of the vulnerabilities described in this report can be exploited via 'drive-by attack' methodologies," he said.
"I believe that in order to fully protect users, I truly believe that this localhost web server solution needs to be removed."
Zoom rolled out the usual tropes in its statement and said it "takes all security concerns related to our products very seriously and has a dedicated Security team in place".
"We acknowledge that our website currently doesn't provide clear information for reporting security concerns," Zoom said.
"As such, in the next several weeks, Zoom will go live with its public bug bounty program, supplementing our existing private program."
After his experience with Zoom, Leitschuh recommended that researchers do not report vulnerabilities to the vendor, and instead use the Zero Day Initiative.
It is recommended users tick the setting to turn off video when joining a meeting inside Zoom, and if wanting to remove the application, the user would need to find the process ID, which can be done via `lsof -i :19421`, then removing the ~/.zoomus directory and touching it to prevent the application being reinstalled.
Samples of the vulnerabilities from Leitschuh can be found on GitHub.
Related Coverage
What Zoom's IPO says about the video collaboration space
The success behind Zoom isn't that surprising. Perhaps the big question is this: How did a bevy of large technology giants blow it in the video collaboration market.
Zoom's IPO opens at an eye-popping $65 per share
The cloud enterprise video communication company drummed up major market excitement as a Silicon Valley unicorn that has actually turned a profit.
Zoom reports strong Q1, ups outlook, adds to swelling customer base
Zoom's IPO was hot and the company's first quarter results weren't far behind.
Why Apple should follow Microsoft's move to get rid of passwords (TechRepublic)
Apple is testing biometric authentication as a new way of signing in to iCloud.com.
Cyberwar risk: Utilities fail to patch critical security vulnerabilities often enough (TechRepublic)
The potential risks associated with compromised systems are severe. Given the prospects of a potential cyberwar, utilities should place a greater emphasis on security.