Bing ad serves malware to would-be Google Chrome switchers

Update: The same gang is responsible for a wave of new ads that lead to malware. See Bing ad leads to more malware; new Mac Trojan in the wild.
Can you trust your favorite search engine? Don’t answer too quickly.
Earlier this year, Google was under siege by a gang of Russian criminals. The bad guys hijacked search results (especially for images) and used scripts to redirect Windows and Mac users to sites that tried to scare them into installing fake antivirus software.
Google eventually cleaned up the mess, and Russian authorities helped their cause immensely by arresting the ringleader.
But that doesn’t mean it’s safe to relax yet. This week I’m watching a new wave of attacks that are using web advertising and social engineering to deliver Windows-based malware. The payload looks like legitimate software, but it’s actually a malicious downloader .
Today’s example is from Bing, which may have a fraction of Google’s search traffic but still has attracted the attention of cybercriminals.
Earlier today I visited Bing and searched for google chrome. The results were accompanied by a handful of ads in prominent positions at the top and along the right side. Nothing unusual about that, except for two nearly identical ads that appeared side-by-side at the top of the list. Here's what they looked like (I've obscured the URL names to make the test tougher).
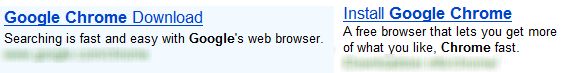
One of those ads was legitimate, and the other led to a malware attack. Can you tell which was which?
Here's the landing page for the first ad:
And here's where clicking the second ad led:
If you look closely enough, you can probably figure out that the first site is Google's legitimate Chrome download page and the second one is fake, but the differences are subtle. A nontechnical observer would have a very difficult time figuring out that one of those big blue Download Google Chrome buttons is the real deal and one is fake.
The path from my web browser to the malicious software was a convoluted one.
The landing page for the fake site is served from a domain called iDownloadster.info, which has been built for deception. The domain was registered with GoDaddy four days ago, and the ad is hosted at a Ukrainian site called Goodnet. The download link leads to a separate domain, dl-byte.com, which was registered seven days ago and is hosted on a server that is infested with malware, porn, and fake pharmaceutical sites, most of it located in Russia.
But there’s no way to know any of that if you simply click the link and download the software.
When I sent the fake download to VirusTotal for analysis, it was detected by only a handful of antivirus engines. Microsoft Security Essentials missed this threat initially, but a definition update a couple hours later identified the downloaded file as Rogue:Win32/FakeRean. This family of fake antivirus software goes by dozens of names in the wild: Win 7 Internet Security 2011 and Total Win 7 Security, among others.
That lag between the time I downloaded the file and when it was identified is a perfect illustration of the phenomenon I wrote about last week in Why malware networks are beating antivirus software. But that doesn’t mean I was a sitting duck. In fact, all of my main Windows PCs stopped this potential infection in its tracks, using security layers that don’t depend on definition files.
In my next post, I’ll offer a detailed look at how those antivirus alternatives work and why they represent the future of online security.
Update: Five hours after I reported this issue to Microsoft, the fake ad was removed. A Microsoft spokesperson provided the following comment:
Microsoft has identified the malicious ad and took the appropriate action to remove it. The advertiser also can no longer post ads on Bing. In addition, the site's URL is no longer available via adCenter. We remain vigilant in protecting consumers, advertisers and our network from fake online insertion orders and continue to directly work with our agency media partners to verify and confirm any suspicious orders.
Related posts: