Coming soon to a Mac near you: serious malware

Welcome, Daring Fireball visitors! You really should read the much longer and more detailed follow-up post here: Why Mac malware is on its way.
Follow-up: Malware attempts that use Apple-focused social engineering are now in the wild. I just found one via Google Image search. See for yourself: What a Mac malware attack looks like.
Last week I showed you how malware authors have begun using social engineering to target Google Chrome, with convincing replicas of Chrome’s bright-red security screens to trick victims into installing a package of malware.
Now I am seeing evidence that the next target is OS X. That’s potentially very bad news for Mac owners who have abandoned their PCs in the belief that switching to a Mac somehow immunizes them from malware.
Security experts know, of course, that there’s nothing magical about Macs when it comes to security. They just haven’t been targeted because Windows has been such a big juicy target for so long.
But now that Macs have achieved a critical mass of success in the marketplace, they’ve attracted the attention of malware authors. According to a report from a Danish IT security company, an underground group has completed work on a fully operational kit specifically designed to build malware aimed at the Mac OS platform:
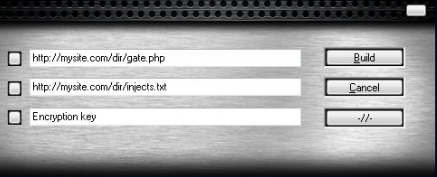
The first advanced DIY (Do-It-Yourself) crimeware kit aimed at the Mac OS X platform has just been announced on a few closed underground forums. … The kit is being sold under the name Weyland-Yutani BOT and it is the first of its kind to hit the Mac OS platform. Apparently, a dedicated iPad and Linux release are under preparation as well.
[…]
The Weyland-Yutani BOT supports web injects and form grabbing in Firefox; however both Chrome and Safari will soon follow. The webinjects templates are identical to the ones used in Zeus and Spyeye.
CSIS eCrime Unit is in possession of videos documenting both the admin panel and its functionality as well as the builder itself. Both video clips prove this kit to be fully operational already.
This is not a proof-of-concept attack written by a researcher or someone trying to score a prize in a security contest like Pwn2Own. This is the real deal.
CSIS partner Peter Kruse told me that the builder runs on Windows, “and based upon the configuration added by the user it will create a Mac binary which obviously can be used to steal data from infected Mac hosts.” I’ve had an opportunity to observe the videos of this program in operation, and it works as advertised. Building the malware package took literally a couple of clicks and less than five seconds. With the Trojan installed on a Mac, a remote host was able to log keystrokes in Safari and capture passwords for a Gmail account—it was even able to detect and log the victim’s attempt to change the compromised password.
The widespread attack that I watched unfold in late April already has all the ingredients in place to make an attack like this possible. Here, for example, is a snippet of the script that I saved from one of the Google-targeted sites:
This particular attack, which I saw over and over again in Google search results, customizes its results based on the victim’s browser and operating system. When I used Chrome, I saw an attack that duplicated the security screens from Chrome. When I used Internet Explorer, I saw screens that mimicked Windows Explorer in Windows 7. When I used Firefox, the attack looked like a series of Windows XP screens.
And when I visited a poisoned site using a Mac, the script detected my OS, skipped the fake malware screens, and redirected me instead to a phishing site.
So why didn’t the authors of this malware deliver a booby-trapped OS X installer package? Maybe it’s on their to-do list.
If a malware author can detect that you’re visiting a “poisoned” site using OS X, it could easily serve up an executable file tailor-made to run on a Mac and steal passwords, log keystrokes, send spam, or deliver pop-ups. The malware author can code in exploits to take advantage of unpatched vulnerabilities in OS X or in programs like iTunes or Adobe Flash to install the software as a drive-by download. They can also use the same tactics that have worked so well against Windows users. That’s where the social engineering comes in. If a Mac owner is told that there’s an important update for Flash or iTunes and they need to install it immediately, will they do so? Some significant percentage certainly will.
An even more sobering thought for Mac owners is the possibility that attackers will create targeted packages aimed at businesses that have switched to Macs. If you can send a booby-trapped PDF file that appears to come from your HR department, the chances that it will be opened go sky-high.
If a group decides to deploy an attack like this on a wide scale, the impact on Mac users could be devastating. Only a tiny percentage of Macs run antivirus software, and Mac users have been conditioned to believe they’re immune from Internet threats. That’s a deadly combination.
Update: H/T Rob VandenBrink at SANS, who mentioned this in a post this morning that sent me to the original source.