Microsoft versus Microsoft: IE9 busts MSDN for a security gaffe

Update 18-June 9AM PDT: The Web Platform and Tools team has replaced the original version of the Visual Studio update described in this post with one that is digitally signed.
You don’t see this sort of thing very often, thankfully.
Today, a self-described “rogue faction” at Microsoft (that's a joke, of course) released an add-in for Visual Studio 2010 that improves HTML5 and JavaScript support. (Read Mary Jo Foley’s writeup for more details.)
But a funny thing happens if you use Internet Explorer 9 to download the code from the Visual Studio gallery. A few weeks ago, I wrote about the new reputation-based security features in IE9 and noted in passing, “No domain or file gets a free pass—not even a new signed release from Microsoft or Google. Every file has to build a reputation.”
Here’s your proof:
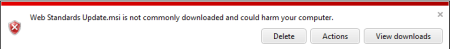
That red shield is a severe roadblock. IE9 makes it particularly difficult to download any file that falls into this category.
At first glance, this seems like a false positive (Tim Anderson described it as “extreme for a download from an official Microsoft site”).
Look more closely at the file and you will see there's a legitimate reason for the dire warning. It’s a Microsoft Installer file, which means its job is to install a program on your system. And yet this MSI package is not digitally signed. A brand new file that hasn’t been seen in public before and is not digitally signed? According to Microsoft Security, there’s about a 96% chance that that code is malware.
This really and truly is an unofficial release. But it’s hosted on a Microsoft server, where the public should never, ever be able to download executable code that isn’t digitally signed. Period. If that isn’t a companywide security policy, it should be.
I expect that this mistake will be fixed relatively quickly, but in a way I’m glad it happened. It offers a chance to see and learn from the real-world consequences when coders aren’t thinking about security.