The slow and steady evolution of cross-platform malware

The rise of the global Internet in the early to mid-2000s made online crime possible and profitable. The sheer size of Microsoft’s monopoly made Windows the only target that mattered for malware authors. And so for years all malware was Windows malware, which led some people to conclude that it would always be so.
But a funny thing happened over the past decade, as Microsoft was smacked down hard in antitrust suits in the United States and the European Union: Its monopoly began to erode, and alternative platforms began to succeed. At the same time, Microsoft became much more effective at responding to security threats.
See also: Oxford University IT staff 'somewhat overwhelmed by Mac malware'
One year ago this week, I wrote a post titled Why malware for Macs is on its way. In it, I laid out the economic reasons why Mac malware was almost certain to begin appearing in greater numbers. In that post, I quoted a 2008 paper by security researcher Adam J. O’Donnell, who said:
I expect relatively wide-spread, monetized Mac malware when we see around 5-10% of the Internet population using Macs.
We reached that tipping point more than a year ago. In April 2011, NetMarketShare stats showed Mac usage at 5.67%. A year later, in April 2012, those numbers have risen sharply, with Mac usage now up to 6.53% worldwide.
And now, with Flashback, we have the first example of widespread, monetized malware aimed exclusively at Macs. According to a report by Symantec researchers, the Flashback business model involved redirecting clicks from infected Macs and stealing the ad revenue:
Ad-clicking Trojans are nothing new and in an analysis of W32.Xpaj.B last August a botnet measuring in the region of 25,000 infections could generate the author up to $450 per day. Considering the Flashback Trojan measures in the hundreds of thousands, this figure could sharply rise to the order of $10000 per day.
(My ZDNet colleague Ryan Naraine has more details.)
In that same post a year ago, I made this prediction:
Upcoming versions of crimeware kits will probably be cross-platform, with the capability to build and deliver Windows and OS X packages using as many vulnerabilities and social engineering tricks as possible. On every poisoned web page, visitors get sorted by OS: Windows users this way, OS X users over there. Each group gets its own custom, toxic blend. If all it takes is a tick of a check box, the gangs using these kits can jump into the Mac market literally overnight.
Many of the poisoned web sites that delivered the Mac Defender rogue antivirus product last year were set up to handle both Windows and Mac-based victims. And now, in the wake of Flashback, guess what showed up in the news today?
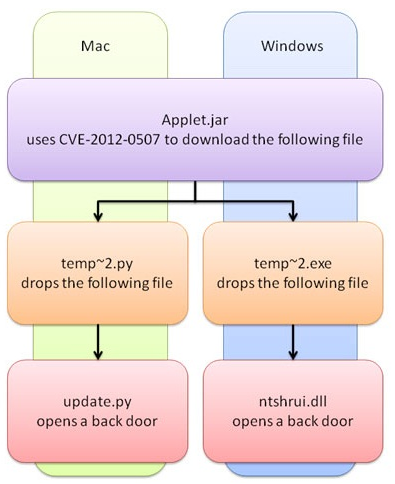
Security vendors have discovered a new piece of malware that attacks both PCs and Macs. It uses the same Java security vulnerability exploited by the Flashback malware that infected hundreds of thousands of Macs. While the attack vector is the same as in Flashback, this Java Applet checks which OS it is running on and downloads suitable malware for it.
[…]
Both droppers result in a Trojan that opens a back door on the compromised computer, allowing remote hackers to secretly send commands, upload code to the victim’s computer, steal files, and run commands without the user’s knowledge. The two Trojans are downloaded from the same server.
The Trojan only checks whether it is running on Windows once, but the downloaded Python dropper checks again whether it is running on a Mac or not. If it is running on Linux or some other operating system, the threat does nothing. Python is not often used to write malware, but in this case it works fine on Macs since Python is installed by default.
This diagram, which documents the workings of the newly discovered threat, is almost a perfect representation of what I predicted last year:
It would be trivially easy to make that exploit available for the widely used Blackhole exploit kit, which already contains one malicious Java applet that targets the same vulnerability.
Economic conditions are ripe for malicious activity to increase, slowly and steadily. Malware is a numbers game. As Mac sales continue to grow faster than Windows PC sales, especially in wealthy countries, the target gets more and more attractive to criminals.
Here’s what I wrote last year:
A gain of a few percentage points in the Mac market might not seem like a lot, but in a universe with a billion Internet-connected devices, each percentage point equals a potential 10 million victims. A market with 60 million, 80 million, or even a hundred million Mac users is big enough for the bad guys.
In the calendar year that ended March 30, 2012, Apple sold more than 17 million Macs. Mac sales continue to rise every quarter. By the end of this year there will be more than 80 million Macs, with probably half of them running versions of OS X for which Apple no longer supplies security updates. Among those running supported OS X versions, recent data shows that 20% or more are at least one update behind.
As the share of Macs online rises, so does interest from criminals. They will do to the Mac platform (albeit on a smaller scale) what they’ve been doing to the Windows platform for years: pick away at vulnerabilities in the OS, in related code, and in third-party apps, change their tactics regularly, and step up their social engineering efforts. Malware on Macs is likely to continue as a persistent low-level threat.
As part of that slow, steady evolution, you’re likely to see the stakes and the intensity level rise.
Windows users in commercial establishments have been targeted for the last six years by Trojans that steal banking information. Brian Krebs has documented case after case of small businesses that were attacked by gangs that then drained their bank accounts. Like this one from just a few weeks ago:
[C]yber crooks struck Alta East, a wholesale gasoline dealer in Middletown, N.Y. According to the firm’s comptroller Debbie Weeden, the thieves initiated 30 separate fraudulent transfers totaling more than $121,000. Half of those transfers went to prepaid cards issued by Metabank, a large prepaid card provider.
This attack was not random. It was planned like a bank job:
Sometime on March 13, four different employees of Alta East received emails that appeared to have been sent from a current client. The messages inquired about a recent transaction, and cited an invoice number. According to Weeden, all four Alta East employees opened the attached Adobe PDF file, which contained a hidden Javascript element that infected their Windows XP systems with a variant of the ZeuS Trojan.
Six days later, the thieves set up a batch of fraudulent payroll payments....
“The emails came from a legitimate customer, and we thought he was questioning an invoice,” Weeden said. “There were four of us who hit that attachment. Afterwards, we asked the customer about the email, but he said he hadn’t sent it.”
A mere two years ago, Krebs advised readers to use a Mac instead of a Windows PC for any online banking, citing the example of a similar near-six-figure ripoff. That doesn't seem like such a bulletproof option now.
How long until a banking/keylogger Trojan is available in a cross-platform package? I know a lot of successful high-end art dealers and antique shops that run on Macs. Think they'd be good targets?
How long before exploits take aim at vulnerabilities disclosed and patched in recent OS X updates? Knowing that so many Mac users update slowly, that's a tremendous untapped opportunity.
How long until web-based Mac malware adds packers and server-side polymorphism (PDF) like their Windows counterparts? With those technologies, malicious code can mutate rapidly and obfuscate itself with each new delivery so that it can’t be detected by Apple’s XProtect signatures.
I don’t know the answers to any of those specific questions. But the smart money is betting on “sooner, not later.”
See also: